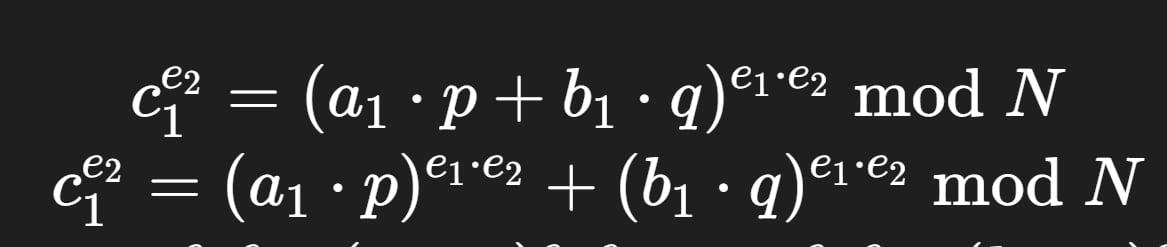I'm a beginner in cybersecurity and CTF where I used to spend lot of time in searching of websites to learn related courses, To be precise I need separate website's to learn for pwn,crypto,web,rev and all categories that makes a strong foundation in cybersecurity
I've been spending 6/7 hrs a day learning cybersecurity (for the last 17 days), i've learned the basics and something more, i've done all the easier ctf problems, but rn i'm struggling doing the web and binary/reverse medium problems. Do you have anything to recommend to me, like some videos or sites where I should look to learn how to do any type of pwn/reverse/web at a medium/difficult level. i'm really stucked and idk what to do. tysm for any kind of help.
I have a team with a buddy of mine and are looking for more people to do CTFs with every weekend for the remainder of the summer. We are looking for people that do any category (crypto, rev, web, misc, pwn, etc) for the rest of the summer. Anyone is welcome we just want as many people as possible to make doing CTFs a more fun experience. DM if interested.
Hey there,
I want to host a small CTF competition for my school.
but i'm unable to understand to make a challenge using binwalk
i want to hide a file on a .jpg or .zip file and it should be extracted only using binwalk.
Trying to form a small CTF team, No need for much prior knowledge, hmu if interested in one of the following CTF topics and you are willing to commit for at least a couple months:
-
Web
-
Blockchain
-
Cryptography
-
Pwn
-
Reverse Engineering
-
OSINT
Anyone loves to play Ctf, I'm lonely I wish to join a team, im more intrigued to Web category but doesn't matter. I Want to Join a Team with any of you as long as you like to play Ctf!! Preferable chatting on Discord
Hey guys. I am new to ctf world. Where should i begin?
Hey guys..need some help with finding a flag on an IP contained in a flag.txt file. Tried URL encoding etc but I can't seem to locate
I need a help in solving CTF
I'm looking for some teammates to do CTFs with. I tend to procrastinate, so having a team would help us stay accountable and support each other. If you're interested, join the Discord server here:
Hope to see you there :)


Anybody have the address to any of the admins I can contact directly? I have a subscription but can't get any challenges or learning labs to load. Thanks in advance.
I am not good at rev. I managed to decompile C code - thus I can see I have a say 21 character buffer char array on the stack (local variable). My input is copied into it with no bounds checking, and I can see I can get some misbehaving overflowing the buffer. And a dump.
Now, how do I use this to inject code? Say a reverse shell or something else ? Are there any relative easy guides out there ?
x86 assembly isn’t my strongest - But plenty of experience for old days with Z80 and 68k (writing assembler, debugging, simple bypassing of checks etc)

![u/[deleted] avatar](http://web.archive.org./web/20240803055355im_/https://www.redditstatic.com/shreddit/assets/snoovatar-back-64x64px.png) [deleted]
[deleted]
I have this cryptography CTF to solve, which is a vulnerable python implementation of AES in CFB mode. There is the main file we're trying to decrypt and 26 other files, which I'm guessing are the partial ciphertexts in CFB mode. There is also the not-important.txt file which contains this string: e20aad41819bf26e6b1de4f5c61f7c04, which might be key, might be IV, not sure.
Does anyone know how to solve this?
Instructions and source files:
Hello CTF community , I am kind of new on the cybersecurity field, and my company has made us complete a series of challenges.
I got this issue. I have a photo, from Atenea's oldtimes challenge () using exiftool, I can see that in the “rights” parameter, it has the following information: 2012, VVIDM1VSQDN3dwIiiCd3M2aDNmI=, all rights reserved. That appears to be a base64 string, but when I decode it, I get: UR3UR@3ww"'w3f6b. That indicates another encryption format, but I don't know what it is. I currently find myself out of options on how to solve this challenge.
Could you give me some guide or some source material that can help me solve it?
Thanks in advance.
I spent two weeks learning and developing the website.CTF crypto and decrypto online tools ,i hope this website can be of assistance to some new CTFer in the CTF community. :)
Hi
I'm trying to get into the world of ctfs and I'm clueless on how to start,
what do u recommend me to do in order to start? I dont now where to begin
Can anyone help with this -
Wow my friend's a real rockstar, I mean look at the program they wrote:
revenge is a dish best served cold they say
put revenge into me
death takes my pain
death's touch I long for
it is a sin but
the sin is mine
you are a false prophet
I was good, I did good, but
you said no
give it back
the lord takes everything
passion is nought but fire
reason is the smith who tempers the fire and yet
if passion without reason isn't nothing
what is the point?
the moon is beautiful tonight
put the lord taking revenge into a prayer
Let faith be death taking me
Whisper a prayer with faith
HII, i am participating in a CTF, i am stuck on this question, im sure that its morse code, but i need some help
So far ive tried -
-
DTAE#
-
WAET#
-
J E T M J
None of these have worked
Hi .., I am solving one question in the Google CTF , beginners quest , so in the second level of the quest(1837) , there is one audio of the morse code , and I got the text through the decoder , and from the hint I got that ADFGVX cipher is again encrypted using 7 word key , and I tried to findout how , and I read some writeupss too , but didn't understand them , can anyone please help me.
Details:
1837 level challenge -2 .