What is OpenID Connect?
OpenID Connect 1.0 is a simple identity layer on top of the OAuth 2.0 protocol. It allows Clients to verify the identity of the End-User based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the End-User in an interoperable and REST-like manner.
OpenID Connect allows clients of all types, including Web-based, mobile, and JavaScript clients, to request and receive information about authenticated sessions and end-users. The specification suite is extensible, allowing participants to use optional features such as encryption of identity data, discovery of OpenID Providers, and session management, when it makes sense for them.
See http://openid.net/connect/faq/ for a set of answers to Frequently Asked Questions about OpenID Connect.
How is OpenID Connect different than OpenID 2.0?
OpenID Connect performs many of the same tasks as OpenID 2.0, but does so in a way that is API-friendly, and usable by native and mobile applications. OpenID Connect defines optional mechanisms for robust signing and encryption. Whereas integration of OAuth 1.0a and OpenID 2.0 required an extension, in OpenID Connect, OAuth 2.0 capabilities are integrated with the protocol itself.
Specification Organization
The OpenID Connect 1.0 specification consists of these documents:
- Core – Defines the core OpenID Connect functionality: authentication built on top of OAuth 2.0 and the use of Claims to communicate information about the End-User
- Discovery – (Optional) Defines how Clients dynamically discover information about OpenID Providers
- Dynamic Registration – (Optional) Defines how clients dynamically register with OpenID Providers
- OAuth 2.0 Multiple Response Types – Defines several specific new OAuth 2.0 response types
- OAuth 2.0 Form Post Response Mode – (Optional) Defines how to return OAuth 2.0 Authorization Response parameters (including OpenID Connect Authentication Response parameters) using HTML form values that are auto-submitted by the User Agent using HTTP POST
- Session Management – (Optional) Defines how to manage OpenID Connect sessions, including postMessage-based logout and RP-initiated logout functionality
- Front-Channel Logout – (Optional) Defines a front-channel logout mechanism that does not use an OP iframe on RP pages
- Back-Channel Logout – (Optional) Defines a logout mechanism that uses direct back-channel communication between the OP and RPs being logged out
- OpenID Connect Federation – (Optional) Defines how sets of OPs and RPs can establish trust by utilizing a Federation Operator
Two implementer’s guides are also available to serve as self-contained references for implementers of basic Web-based Relying Parties:
- Basic Client Implementer’s Guide – Simple subset of the Core functionality for a web-based Relying Party using the OAuth code flow
- Implicit Client Implementer’s Guide – Simple subset of the Core functionality for a web-based Relying Party using the OAuth implicit flow
A protocol migration specification has been finalized:
- OpenID 2.0 to OpenID Connect Migration 1.0 – Defines how to migrate from OpenID 2.0 to OpenID Connect
Finally, the OpenID Connect working group has started this new work:
- OpenID Connect Profile for SCIM Services – (Optional) Defines how to use SCIM with OpenID Connect
- OpenID Connect for Identity Assurance – (Optional) Defines an OpenID Connect extension for Identity Assurance
The OpenID Connect specifications, implementer’s guides, and specifications they are built upon are shown in the diagram below. Click on the boxes in the diagram to view the specification.
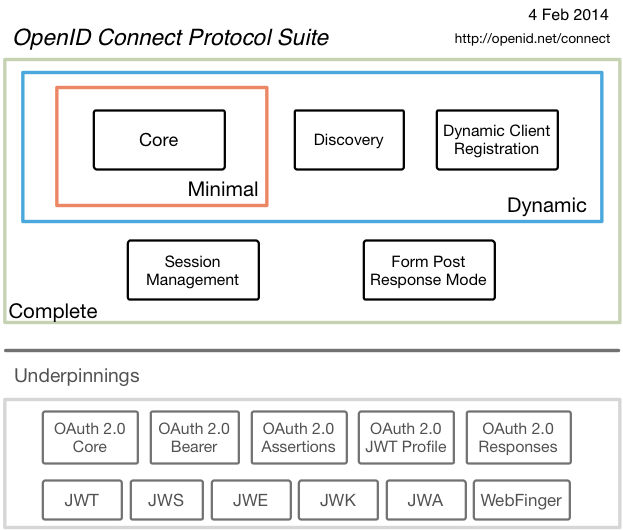
Participation in the Working Group
The easiest way to monitor progress on the OpenID Connect 1.0 Specification is to join the mailing list at http://lists.openid.net/mailman/listinfo/openid-specs-ab.
Please note that while anyone can join the mailing list as a read-only recipient, posting to the mailing list or contributing to the specifications requires the submission of an IPR Agreement. More information is available at http://openid.net/intellectual-property. Make sure to specify the working group as “OpenID AB/Connect”, because this group is a merged working group and both names must be specified.
For more details on participating, see the OpenID Connect Working Group Page.
Implementations
The Libraries page lists libraries that implement OpenID Connect and related specifications.
Interop Testing
Interop testing for OpenID Connect implementations is under way. If you are interested in participating in the interop activities, join the OpenID Connect Interop mailing list.
Status
Final OpenID Connect specifications were launched on February 26, 2014.
The certification program for OpenID Connect was launched on April 22, 2015.
Final OAuth 2.0 Form Post Response Mode Specification was approved on April 27, 2015.
OpenID Certification for RPs was made available to all in August 2017.
Implementer’s Draft of OpenID Connect Federation Specification Approved on August 7, 2018.
