Thursday, 08 March 2018
An argument against proxies
Inductive Bias | 17:53, Thursday, 08 March 2018
Proxies? In companies getting started with an upstream first concept this is what people are called who act as the only interface between their employer and an open source project: All information from any project used internally flows through them. All bug reports and patches intended as upstream contribution also flows through them - hiding entire teams producing the actual contributions.At Apache projects I learnt to dislike this setup of having proxies act in place of the real contributors. Why so?
Apache is built on the premise of individuals working together in the best interest of their projects. Over time, people who prove to commit themselves to a project get added to that project. Work contributed to a project gets rewarded - in a merit doesn't go away kind-of sense working on an Apache project is a role independent of other work committments - in the "merit doesn't go away" sense this merit is attached to the individual making contributions, not to the entity sponsoring that individual in one way or another.
This mechanism does not work anymore if proxy committers act as gateway between employers and the open source world: While proxied employees are saved from the tax that working in the public brings by being hidden behind proxies, they will also never be able to accrue the same amount of merit with the project itself. They will not be rewarded by the project for their committment. Their contributions do not end up being attached to themselves as individuals.
From the perspective of those watching how much people contribute to open source projects the concept of proxy committers often is neither transparent nor clear. For them proxies establish a false sense of hyper productivity: The work done by many sails under the flag of one individual, potentially discouraging others with less time from participating: "I will never be able to devote that much work to that project, so why even start?"
From an employer point of view proxies turn into single point of failure roles: Once that person is gone (on vacation, to take care of a relative, found a new job) they take the bonds they made in the open source project with them - including any street cred they may have gathered.
Last but not least I believe in order to discuss a specific open source contribution the participants need a solid understanding of the project itself. Something only people in the trenches can acquire.
As a result you'll see me try and pull those actually working with a certain project to get active and involved themselves, to dedicate time to the core technology they rely on on a daily basis, to realise that working on these projects gives you a broader perspective beyond just your day job.
Sunday, 04 March 2018
Encrypted files in Dropbox
Evaggelos Balaskas - System Engineer | 19:18, Sunday, 04 March 2018
Encrypted files in Dropbox
As we live in the age of smartphones and mobility access to the cloud, the more there is the need to access our files from anywhere. We need our files to be available on any computer, ours (private) or others (public). Traveling with your entire tech equipment is not always a good idea and with the era of cloud you dont need to bring everything with you.
There are a lot of cloud hosting files providers out there. On wikipedia there is a good Comparison of file hosting services article you can read.
I’ve started to use Dropbox for that reason. I use dropbox as a public digital bucket, to store and share public files. Every digital asset that is online is somehow public and only when you are using end-to-end encryption then you can say that something is more secure than before.
I also want to store some encrypted files on my cloud account, without the need to trust dropbox (or any cloud hosting file provider for that reason). As an extra security layer on top of dropbox, I use encfs and this blog post is a mini tutorial of a proof of concept.
EncFS - Encrypted Virtual Filesystem
(definition from encfs github account)
EncFS creates a virtual encrypted filesystem which stores encrypted data in the rootdir directory and makes the unencrypted data visible at the mountPoint directory. The user must supply a password which is used to (indirectly) encrypt both filenames and file contents.
That means that you can store your encrypted files somewhere and mount the decrypted files on folder on your computer.
Disclaimer: I dont know how secure is encfs. It is an extra layer that doesnt need any root access (except the installation part) for end users and it is really simple to use. There is a useful answer on stackexchange that you night like to read .
For more information on enfs you can also visit EncFS - Wikipedia Page
Install EncFS
-
archlinux
$ sudo pacman -S --noconfirm encfs -
fedora
$ sudo dnf -y install fuse-encfs -
ubuntu
$ sudo apt-get install -y encfs
How does Encfs work ?
- You have two(2) directories. The source and the mountpoint.
- You encrypt and store the files in the source directory with a password.
- You can view/edit your files in cleartext, in the mount point.
-
Create a folder inside dropbox
eg./home/ebal/Dropbox/Boostnote - Create a folder outside of dropbox
eg./home/ebal/Boostnote
both folders are complete empty.
- Choose a long password.
just for testing, I am using a SHA256 message digest from an image that I can found on the internet!
eg.sha256sum /home/ebal/secret.png
that means, I dont know the password but I can re-create it whenever I hash the image.
BE Careful This suggestion is an example - only for testing. The proper way is to use a random generated long password from your key password manager eg. KeePassX
How does dropbox works?
The dropbox-client is monitoring your /home/ebal/Dropbox/ directory for any changes so that can sync your files on your account.
You dont need dropbox running to use encfs.
Running the dropbox-client is the easiest way, but you can always use a sync client eg. rclone to sync your encrypted file to dropbox (or any cloud storage).
I guess it depends on your thread model. For this proof-of-concept article I run dropbox-client daemon in my background.
Create and Mount
Now is the time to mount the source directory inside dropbox with our mount point:
$ sha256sum /home/ebal/secret.png |
awk '{print $1}' |
encfs -S -s -f /home/ebal/Dropbox/Boostnote/ /home/ebal/Boostnote/Reminder: EncFs works with absolute paths!
Check Mount Point
$ mount | egrep -i encfsencfs on /home/ebal/Boostnote type fuse.encfs
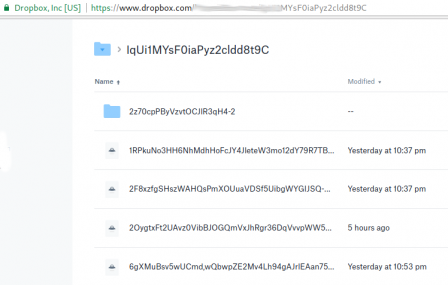
(rw,nosuid,nodev,relatime,user_id=1001,group_id=1001,default_permissions)View Files on Dropbox
Files inside dropbox:
View Files on the Mount Point
Unmount EncFS Mount Point
When you mount the source directory, encfs has an option to auto-umount the mount point on idle.
Or you can use the below command on demand:
$ fusermount -u /home/ebal/BoostnoteOn another PC
The simplicity of this approach is when you want to access these files on another PC.
dropbox-client has already synced your encrypted files.
So the only thing you have to do, is to type on this new machine the exact same command as in Create & Mount chapter.
$ sha256sum /home/ebal/secret.png |
awk '{print $1}' |
encfs -S -s -f /home/ebal/Dropbox/Boostnote/ /home/ebal/Boostnote/Android
How about Android ?
You can use Cryptonite.
Cryptonite can use EncFS and TrueCrypt on Android and you can find the app on Google Play

Monday, 26 February 2018
The Goal and The DevOps Handbook
Evaggelos Balaskas - System Engineer | 12:44, Monday, 26 February 2018
I’ve listened two audiobooks this month, both on DevOps methodology or more accurate on continuous improving of streamflow.
also started audible - amazon for listening audiobooks. The android app is not great but decent enough, although most of the books are DRM.
The first one is The Goal - A Process of Ongoing Improvement by: Eliyahu M. Goldratt, Jeff Cox
I can not stress this enough: You Have To Read this book. This novel is been categorized under business and it is been written back in 1984. You will find innovating even for today’s business logic. This book is the bases of “The Phoenix Project” and you have to read it before the The Phoenix Project. You will understand in details how lean and agile methodologies drive us to DevOps as a result of Ongoing Improvement.
https://www.audible.com/pd/Business/The-Goal-Audiobook/B00IFG88SM
The second book is The DevOps Handbook or How to Create World-Class Agility, Reliability, and Security in Technology Organizations by By: Gene Kim, Patrick Debois, John Willis, Jez Humble Narrated by: Ron Butler
I have this book in both hardcopy and audiobook. It is indeed a handbook. If you are just now starting on devops you need to read it. Has stories of companies that have applied the devops practices and It is really well structured. My suggestion is to keep notes when reading/listening to this book. Keep notes and re-read them.
https://www.audible.com/pd/Business/The-DevOps-Handbook-Audiobook/B0767HHZLZ
Friday, 23 February 2018
Okular gains some more JavaScript support

TSDgeos' blog | 15:53, Friday, 23 February 2018
Andre Heinecke did some patches [1][2][3][4][5] over the last few weeks that finally got landed this week.With it we support recalculation of some fields based on others. An example that calculates sum, average, product, minimum and maximum of three numbers can be found in this youtube video.
<iframe allow="autoplay; encrypted-media" allowfullscreen="allowfullscreen" frameborder="0" height="315" src="https://www.youtube.com/embed/f77NV15tums" width="560"></iframe>
This code will be available for the Okular version that will ship with KDE Applications 18.04
Tuesday, 20 February 2018
Hacking at EPFL Toastmasters, Lausanne, tonight
DanielPocock.com - fsfe | 11:39, Tuesday, 20 February 2018
As mentioned in my earlier blog, I give a talk about Hacking at the Toastmasters club at EPFL tonight. Please feel free to join us and remember to turn off your mobile device or leave it at home, you never know when it might ring or become part of a demonstration.
Sunday, 18 February 2018
SwissPost putting another nail in the coffin of Swiss sovereignty
DanielPocock.com - fsfe | 22:17, Sunday, 18 February 2018
A few people have recently asked me about the SwissID, as SwissPost has just been sending spam emails out to people telling them "Link your Swiss Post user account to SwissID".
This coercive new application of technology demands users email addresses and mobile phone numbers "for security". A web site coercing people to use text messages "for security" has quickly become a red flag for most people and many blogs have already covered why it is only an illusion of security, putting your phone account at risk so companies can profit from another vector for snooping on you.
SwissID is not the only digital identity solution in Switzerland but as it is run by SwissPost and has a name similar to another service it is becoming very well known.
In 2010 they began offering a solution which they call SuisseID (notice the difference? They are pronounced the same way.) based on digital certificates and compliant with Swiss legislation. Public discussion focussed on the obscene cost with little comment about the privacy consequences and what this means for Switzerland as a nation.
Digital certificates often embed an email address in the certificate.
With SwissID, however, they have a web site that looks like little more than vaporware, giving no details at all whether certificates are used. It appears they are basically promoting an app that is designed to harvest the email addresses and phone numbers of any Swiss people who install it, lulling them into that folly by using a name that looks like their original SuisseID. If it looks like phishing, if it feels like phishing and if it smells like phishing to any expert takes a brief sniff of their FAQ, then what else is it?
The thing is, the original SuisseID runs on a standalone smartcard so it doesn't need to have your mobile phone number, have permissions to all the data in your phone and be limited to working in areas with mobile phone signal.
The emails currently being sent by SwissPost tell people they must "Please use a private e-mail address for this purpose" but they don't give any information about the privacy consequences of creating such an account or what their app will do when it has access to read all the messages and contacts in your phone.
The actions you can take that they didn't tell you about
- You can post a registered letter to SwissPost and tell them that for privacy reasons, you are immediately retracting the email addresses and mobile phone numbers they currently hold on file and that you are exercising your right not to give an email address or mobile phone number to them in future.
- If you do decide you want a SwissID, create a unique email address for it and only use that email address with SwissPost so that it can't be cross-referenced with other companies. This email address is also like a canary in a coal mine: if you start receiving spam on that email address then you know SwissPost/SwissID may have been hacked or the data has been leaked or sold.
- Don't install their app and if you did, remove it and you may want to change your mobile phone number.

Oddly enough, none of these privacy-protecting ideas were suggested in the email from SwissPost. Who's side are they on?
Why should people be concerned?
SwissPost, like every postal agency, has seen traditional revenues drop and so they seek to generate more revenue from direct marketing and they are constantly looking for ways to extract and profit from data about the public. They are also a huge company with many employees: when dealing with vast amounts of data in any computer system, it only takes one employee to compromise everything: just think of how Edward Snowden was able to act alone to extract many of the NSA's most valuable secrets.
SwissPost is going to great lengths to get accurate data on every citizen and resident in Switzerland, including deploying an app to get your mobile phone number and demanding an email address when you use their web site. That also allows them to cross-reference with your IP addresses.
- Any person or organization who has your email address or mobile number may find it easier to get your home address.
- Any person or organization who has your home address may be able to get your email address or mobile phone number.
- When you call a company from your mobile phone and their system recognizes your phone number, it becomes easier for them to match it to your home address.
- If SwissPost and the SBB successfully convince a lot of people to use a SwissID, some other large web sites may refuse to allow access without getting you to link them to your SwissID and all the data behind it too. Think of how many websites already try to coerce you to give them your mobile phone number and birthday to "secure" your account, but worse.
The Google factor
The creepiest thing is that over seventy percent of people are apparently using Gmail addresses in Switzerland and these will be a dependency of their registration for SwissID.
Given that SwissID is being promoted as a solution compliant with ZertES legislation that can act as an interface between citizens and the state, the intersection with such a powerful foreign actor as Gmail is extraordinary. For example, if people are registering to vote in Switzerland's renowned referendums and their communication is under the surveillance of a foreign power like the US, that is a mockery of democracy and it makes the allegations of Russian election hacking look like child's play.
Switzerland's referendums, decentralized system of Government, part-time army and privacy regime are all features that maintain a balance between citizen and state: by centralizing power in the hands of SwissID and foreign IT companies, doesn't it appear that the very name SwissID is a mockery of the Swiss identity?
No canaries were harmed in the production of this blog.
Wednesday, 14 February 2018
I love Free Software Day 2018

Ramblings of a sysadmin (Posts about planet-fsfe) | 22:10, Wednesday, 14 February 2018
Today isn't just Valentines day, but also I love Free Software Day! I've been using (and contributing) Free Software for years now and don't want anything else. Even when I've given non-Free Software another chance, every time I was glad when I returned to Free Software.
A big thank you goes out to all developers, sysadmins, network guru's, translators, bugsquashers and all other contributors.
A small selection of tools/libraries/projects/organizations I'm thankful for this year: debian, ubuntu, terminator, mate, vi(m), firefox, thunderbird, postgresql, apache, kvm, libvirt, bash, openssh, nextcloud, workrave, audacious, vlc, mtp (Media Transfer Protocol), ext2/ext3/ext4/btrfs, mdadm, postfix, the linux kernel, fosdem, fsfe, eff, bitsoffreedom, ccc and kodi.
For the next year, let's make sure we don't squabble amongst ourselves. Let us be even more understanding and help each other out more. Let us agree to disagree and be fine with that. I do not care which window manager, editor, desktop or database you use. Of course I have my own preferences and don't mind a good discussion. As long as we give each other the freedom to choose what we want, it's OK. We're all playing for the Free Software team. And yes, each of us known that we are right ;-)
At the previous FOSDEM I picked up the following card and gave it to my wife, she liked it a lot (just a tip)

What is the best online dating site and the best way to use it?
DanielPocock.com - fsfe | 17:25, Wednesday, 14 February 2018
Somebody recently shared this with me, this is what happens when you attempt to access Parship, an online dating site, from the anonymous Tor Browser.

Experian is basically a private spy agency. Their website boasts about how they can:
- Know who your customers are regardless of channel or device
- Know where and how to reach your customers with optimal messages
- Create and deliver exceptional experiences every time
Is that third objective, an "exceptional experience", what you were hoping for with their dating site honey trap? You are out of luck: you are not the customer, you are the product.
When the Berlin wall came down, people were horrified at what they found in the archives of the Stasi. Don't companies like Experian and Facebook gather far more data than this?

So can you succeed with online dating?
There are only three strategies that are worth mentioning:
- Access sites you can't trust (which includes all dating sites, whether free or paid for) using anonymous services like Tor Browser and anonymous email addresses. Use fake photos and fake all other data. Don't send your real phone number through the messaging or chat facility in any of these sites because they can use that to match your anonymous account to a real identity: instead, get an extra SIM card that you pay for and top-up with cash. One person told me they tried this for a month as an experiment, expediently cutting and pasting a message to each contact to arrange a meeting for coffee. At each date they would give the other person a card that apologized for their completely fake profile photos and offering to start over now they could communicate beyond the prying eyes of the corporation.
- Join online communities that are not primarily about dating and if a relationship comes naturally, it is a bonus.
- If you really care about your future partner and don't want your photo to be a piece of bait used to exploit and oppress them, why not expand your real-world activities?
How to batch geotag your photos using Free Software and OpenStreetMap
English Planet – Dreierlei | 08:35, Wednesday, 14 February 2018
If you like shooting and collecting pictures, you might be interested in geotagging your pictures. More and more software can use such geospatial metadata information for categorizing and visualizing these pictures, for example in an interactive map. Today, on I love Free Software day, I show you a way how to batch geotag your pictures with OpenStreetMap and Free Software only.
Geospatial metadata, together with time-stamps, seem to me to be the most important meta-information a picture can have. It is extremely helpful in organizing pictures, for example to cluster pictures that have been taken at the same location but at different times. Personally, I always need this data whenever I upload my pictures to Wikimedia Commons, as it asks me during the process about the geolocation of these pictures. Before, each time I had to look up the data individually on OpenStreetMap and fill in the information manually. Pretty fast, I got bored of this and I was looking for a way to write this information automatically into my pictures even before uploading.
One solution to this is a GPS-recorder built-in or attached to the camera. Unfortunately, very few cameras come with a GPS-recorder built-in and additional GPS-modules are a way too expensive for most hobby enthusiasts. Fortunately, there are software-solutions, that enable you to use just any other device which is able to capture GPS-tracks and then later merge this recorded geo-information with your pictures taken.
For sure, there are multiple ways to do this. In this blogpost, I will show you how you can do this with a smarthphone, OpenStreetMap and Free Software. All you need is:
- a smartphone running Android or a custom fork
- Osmand~
- a camera
- GPS correlate
Set up your infrastructure
Get Osmand
If you have a phone that is running Android or a more privacy and freedom friendly fork of Android get yourself Osmand, the “Global Mobile Map Viewing and Navigation for Online and Offline OpenStreetMaps”.
You can get it in the usual app-stores, but as it is Free Software, you can also get in on F-Droid, the Free Software app repository. For your privacy I recommend the latter and I wrote up a short manual about how to do it in a previous blogpost. If you choose this way, however, please consider donating to finance further development.
Sync your time
It is crucial that you have the time on your devices in sync. If not, there are possibilities to fix that afterwards, but you save yourself a lot of work if you make sure that your GPS-recorder (your smartphone in our case) and your camera are in time sync.
In action: record your track
Once you have downloaded Osmand, there is no need to download additional plugins. However, you have to activate the Trip recording plugin first.
Here is how to do and use it:
<figure class="wp-caption aligncenter" id="attachment_1267" style="max-width: 400px"> <figcaption class="wp-caption-text">In the menu, go for plugins.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2432" style="max-width: 400px">
<figcaption class="wp-caption-text">In the menu, go for plugins.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2432" style="max-width: 400px"> <figcaption class="wp-caption-text">Click on “Trip recording”</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2435" style="max-width: 400px">
<figcaption class="wp-caption-text">Click on “Trip recording”</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2435" style="max-width: 400px"> <figcaption class="wp-caption-text">Enable Trip recording here</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2434" style="max-width: 400px">
<figcaption class="wp-caption-text">Enable Trip recording here</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2434" style="max-width: 400px"> <figcaption class="wp-caption-text">If you click on settings, you can fine-tune your GPS-recordings, also depending if you go by car, on a bicycle or by foot.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2433" style="max-width: 400px">
<figcaption class="wp-caption-text">If you click on settings, you can fine-tune your GPS-recordings, also depending if you go by car, on a bicycle or by foot.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2433" style="max-width: 400px"> <figcaption class="wp-caption-text">After enabling, your Plugin page should look like this.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2431" style="max-width: 400px">
<figcaption class="wp-caption-text">After enabling, your Plugin page should look like this.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2431" style="max-width: 400px"> <figcaption class="wp-caption-text">As long as the Plugin is enabled, you will see a GPX-symbol in the top-right corner. Click it and you will be prompted with the following record screen.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2427" style="max-width: 400px">
<figcaption class="wp-caption-text">As long as the Plugin is enabled, you will see a GPX-symbol in the top-right corner. Click it and you will be prompted with the following record screen.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2427" style="max-width: 400px"> <figcaption class="wp-caption-text">Choose your logging interval and if you like to see your track while recording. That’s it! From here on your track is being recorded and the only thing you have to do is to stop it once you are finished.</figcaption></figure>
<figcaption class="wp-caption-text">Choose your logging interval and if you like to see your track while recording. That’s it! From here on your track is being recorded and the only thing you have to do is to stop it once you are finished.</figcaption></figure>
And by the way:
<figure class="wp-caption aligncenter" id="attachment_2428" style="max-width: 400px"> <figcaption class="wp-caption-text">Once you have recorded some tracks, you will see a list of previously recorded tracks. You can export them, delete them and visualize them inside the app.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2429" style="max-width: 400px">
<figcaption class="wp-caption-text">Once you have recorded some tracks, you will see a list of previously recorded tracks. You can export them, delete them and visualize them inside the app.</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2429" style="max-width: 400px"> <figcaption class="wp-caption-text">This is an example of how you can also visualize individual trips and statistics afterwards.</figcaption></figure>
<figcaption class="wp-caption-text">This is an example of how you can also visualize individual trips and statistics afterwards.</figcaption></figure>
Afterwards: Geotag your pictures
Get GPS Correlate
There are many ways to get GPS Correlate. You can
- get it from Github
- via your terminal with $ apt-get install gpscorrelate
- or via the Synaptic package manager:
Use GPS Correlate
The interface is pretty simple:
- Press to “add photos” and choose the photos you like to geotag. It can be a single picture or multiple pictures (e.g. all pictures along one gpx-track).
- Choose your recorded gpx-track where is written “GPS Data”
- Keep the default ticked options to “Interpolate” and “Write DD MM SS.SS”
- Choose a maximum gap time for a picture to be matched. I choose 5 minutes (300 seconds) here.
- Put your time zone in UTC
- Go ahead, correlate photos
Now you should see the interpolated match of your pictures and your gpx-track and you are done:
Enjoy your batch processed pictures!
A big hug and thank you to all the people behind OpenStreetMap, behind Osmand, to Daniel Foote and Dan Fandrich for making this possible! Happy I love Free Software Day 2018!
—
Related articles:
Tuesday, 13 February 2018
FOSDEM 2018 - recap
Inductive Bias | 06:13, Tuesday, 13 February 2018
Too crowded, too many queues, too little space - but also lots of friendly people, Belgian waffles, ice cream, an ASF dinner with grey beards and new people, a busy ASF booth, bumping into friends every few steps, meeting humans you see only online for an entire year or more: For me, that's the gist of this year's FOSDEM.Note: German version of the article including images appeared in my employer's tech blog.
To my knowledge FOSDEM is the biggest gathering of free software people in Europe at least. It's free of charge, kindly hosted by ULB, organised by a large group of volunteers. Every year early February the FOSS community meets for two one weekend in Brussels to discuss all sorts of aspects of Free and Open Source Software Development - including community, legal, business and policy aspects. The event features more than 600 talks as well as several dozen booths by FOSS projects and FOSS friendly companies. There's several FOSDEM fringe events surrounding the event that are not located on campus. If you go to any random bar or restaurant in Brussels that weekend you are bound to bump into FOSDEM people.
Fortunately for those not lucky enough to have made it to the event, video recordings (unfortunately in varying quality) are available online at video.fosdem.org. Some highlights you might want to watch:
- Exploiting modern microarchitectures - Meltdown, Spectre, and other hardware attacks by Jon Masters in case you want to understand what the Meltdown and Spectre and the underlying causes really mean for computer security.
- Passing the Baton: Succession Planning for FOSS leadership by VM (Vicky) Brasseur on why you should build hand over into your open source project before it's too late including some hints on how to best do that.
- Too young to Rock'n'Roll by Dominik George and Niels Hradek on what legal hurdles minors encounter when trying to contribute to open source projects.
- State of OpenJDK by Mark Reinhold if you're interested in the state of OpenJDK, both in terms of community as well as in terms of technical challenges ahead.
One highlight for me personally this year: I cannot help but believe that I met way more faces from The Apache Software Foundation than at any other FOSDEM before. The booth was crowded at all times - Sharan Foga did a great job explaining The ASF to people. Also it's great to hear The ASF mentioned in several talks as one of the initiatives to look at to understand how to run open source projects in a sustainable fashion with an eye on longevity. It was helpful to have at least two current Apache board members (Bertrand Delacretaz as well as Rich Bowen) on site to help answer tricky questions. Last but not least it was lovely meeting several of the Apache Grey Beards (TM) for an Apache Dinner on Saturday evening. Luckily co-located with the FOSDEM HPC speaker dinner - which took a calendar conflict out of the Apache HPC people's calendar :)
Me personally, I hope to see many more ASF people later this year in Berlin for FOSS Backstage - the advertisement sign that was located at the FOSDEM ASF booth last weekend already made it here, will you follow?
Wednesday, 07 February 2018
KDE Applications 18.04 Schedule finalized

TSDgeos' blog | 20:56, Wednesday, 07 February 2018
It is available at the usual place https://community.kde.org/Schedules/Applications/18.04_Release_ScheduleDependency freeze is in 5 weeks and Feature Freeze in 6 weeks, so hurry up!
FSFE Assembly at 34C3: Wir taten was
English Planet – Dreierlei | 20:04, Wednesday, 07 February 2018
In December 2017, the Chaos Communication Congress moved for the first time onto the Messegelände Leipzig. The FSFE came along and as in recent years, our assembly attracted a lot of visitors. Together with EDRi, for the first time we have been setting up a cluster called “Rights & Freedoms” with our own stage for multiple sessions. Although there have been some organisational issues, this Cluster was a big success and during three days, it has been visited by thousands of people.
I am happy to see the FSFE assembly again growing every year and having the possibility to bring our message of Software Freedom to the people at the Chaos Communication Congress. The CCC is Germany’s biggest annual meetup of hackers and political activists and is “considered one of the largest events of this kind, alongside the DEF CON in Las Vegas” (wikipedia).
<figure class="wp-caption aligncenter" id="attachment_2382" style="max-width: 580px"> <figcaption class="wp-caption-text">FSFE assembly by day</figcaption></figure>
<figcaption class="wp-caption-text">FSFE assembly by day</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2381" style="max-width: 580px">
 <figcaption class="wp-caption-text">FSFE assembly by night</figcaption></figure>
<figcaption class="wp-caption-text">FSFE assembly by night</figcaption></figure>
After setting up our own self-created track in the session-rooms offered by the CCC in the last two years [2015, 2016], we aligned this year with European Digital Rights (EDRi) and together we have been forming a Cluster called “Rights & Freedoms” around our own lecture hall with a 100-people-audience stage in one half – and room for several friendly organisations to settle their own assemblies in the other half.
<figure class="wp-caption aligncenter" id="attachment_2385" style="max-width: 580px"> <figcaption class="wp-caption-text">Polina Malaja and Katharina Nocun give a presentation of FSFE’s Public Money? Public Code! campaign</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2383" style="max-width: 580px">
<figcaption class="wp-caption-text">Polina Malaja and Katharina Nocun give a presentation of FSFE’s Public Money? Public Code! campaign</figcaption></figure>
<figure class="wp-caption aligncenter" id="attachment_2383" style="max-width: 580px"> <figcaption class="wp-caption-text">Hanno Böck explains “Hacking with wget”</figcaption></figure>
<figcaption class="wp-caption-text">Hanno Böck explains “Hacking with wget”</figcaption></figure>
This way, the FSFE’s track became for the first time official part of the CCC-program. Together with likeminded organisations we used our stage to set up a full-time-program in our cluster that in sum led thousands of visitors in there with the FSFE booth being prominently located directly at its entrance.
Also from the organisers of the CCC, people were very happy with us and our organisation and we were giving the hope to get an even bigger lecture room next year. I see this FSFE’s growing presence at the CCC as a strategically important success because it is not “the usual Free Software conference” but a general technology meet-up. So, a good presence at CCC is not simply stewing our own soup but instead extending our outreach into new networks.
As is true for most of our booths and activities, the whole booth would not have been possible to run without our dedicated volunteer booth team! You are the ones empowering FSFE. And I like to use this occasion to give a special thanks to André Klöpfel, Berlin-based volunteer, without whom I would have not been able to organise our booth so smooth this year and last year already.
<figure class="wp-caption aligncenter" id="attachment_2384" style="max-width: 580px"> <figcaption class="wp-caption-text">No Free Software without some love …</figcaption></figure>
<figcaption class="wp-caption-text">No Free Software without some love …</figcaption></figure> More XEPs for Smack
vanitasvitae's blog » englisch | 14:05, Wednesday, 07 February 2018
I spent the last weekend from Thursday to Sunday in Brussels at the XSF-Summit (here is a very nice post about it by JCBrand) and the FOSDEM. It was really nice to meet all the faces belonging to the JIDs you otherwise only see in the MUCs or on GitHub in real life.
There was a lot of discussion about how to make XMPP more accessible to the masses and one point that came up was to pay more attention to XMPP libraries, as they are often somewhat of a gateway for new developers who discovered the XMPP protocol. A good library with good documentation can help those new developers immensely to get started with XMPP.
During my stay and while on the train, I found some time to work on Smack again and so I added support for 3 more XEPs:
Ge0rG gave a talk about what’s currently wrong with the XMPP protocol. One suggested improvement was to rely more on Stable and Unique Stanza IDs to improve message identification in various use-cases, so I quickly implemented XEP-0359.
XEP-0372: References is one dependency of XEP-0385: Stateless Inline Media Sharing, which I’m planning to implement next, so the boring lengthy train ride was spent adding support for XEP-0372.
A very nice XEP to implement was XEP-0392: Consistent Color Generation, which is used to generate consistent colors for usernames across different clients. I really like the accessibility aspect of that XEP, as it provides methods to generate colors easily distinguishable by users with color vision deficiency.
I hope my contributions will draw one or two developers who seak to implement a chat client themselves to the awesome XMPP protocol ![]()
Happy Hacking!
Friday, 02 February 2018
Everything you didn't know about FSFE in a picture
DanielPocock.com - fsfe | 09:51, Friday, 02 February 2018
As FSFE's community begins exploring our future, I thought it would be helpful to start with a visual guide to the current structure.
All the information I've gathered here is publicly available but people rarely see it in one place, hence the heading. There is no suggestion that anything has been deliberately hidden.
The drawing at the bottom includes Venn diagrams to show the overlapping relationships clearly and visually. For example, in the circle for the General Assembly, all the numbers add up to 29, the total number of people listed on the "People" page of the web site. In the circle for Council, there are 4 people in total and in the circle for Staff, there are 6 people, 2 of them also in Council and 4 of them in the GA but not council.
The financial figures on this diagram are taken from the 2016 financial summary. The summary published by FSFE is very basic so the exact amount paid in salaries is not clear, the number in the Staff circle probably pays a lot more than just salaries and I feel FSFE gets good value for this money.
Some observations about the numbers:
- The volunteers don't elect any representatives to the GA, although some GA members are also volunteers
- From 1,700 fellowship members, only 2 are elected in 2 of the 29 GA seats yet they provide over thirty percent of the funding through recurring payments
- Out of 6 staff, all 6 are members of the GA (6 out of 29) since a decision to accept them at the last GA meeting
- Only the 29 people in the General Assembly are full (legal) members of the FSFE e.V. association with the right to vote on things like constitutional changes. Those people are all above the dotted line on the page. All the people below the line have been referred to by other names, like fellow, supporter, community, donor and volunteer.
If you ever clicked the "Join the FSFE" button or filled out the "Join the FSFE" form on the FSFE web site and made a payment, did you believe you were becoming a member with an equal vote? If so, one procedure you can follow is to contact the president as described here and ask to be recognized as a full member. I feel it is important for everybody who filled out the "Join" form to clarify their rights and their status before the constitutional change is made.

I have not presented these figures to create conflict between staff and volunteers. Both have an important role to play. Many people who contribute time or money to FSFE are very satisfied with the concept that "somebody else" (the staff) can do difficult and sometimes tedious work for the organization's mission and software freedom in general. As I've been elected as a fellowship representative, I feel a responsibility to ensure the people I represent are adequately informed about the organization and their relationship with it and I hope these notes and the diagram helps to fulfil that responsibility.
Therefore, this diagram is presented to the community not for the purpose of criticizing anybody but for the purpose of helping make sure everybody is on the same page about our current structure before it changes.
If anybody has time to make a better diagram it would be very welcome.


Thursday, 01 February 2018
containers containers containers
Evaggelos Balaskas - System Engineer | 21:08, Thursday, 01 February 2018
systemd
Latest systemd version now contains the systemd-importd daemon .
That means that we can use machinectl to import a tar or a raw image from the internet to use it with the systemd-nspawn command.
so here is an example
machinectl
from my archlinux box:
# cat /etc/arch-release
Arch Linux releaseWe can download the tar centos7 docker image from the docker hub registry:
# machinectl pull-tar --verify=no https://github.com/CentOS/sig-cloud-instance-images/raw/79db851f4016c283fb3d30f924031f5a866d51a1/docker/centos-7-docker.tar.xz
...
Created new local image 'centos-7-docker'.
Operation completed successfully.
Exiting.we can verify that:
# ls -la /var/lib/machines/centos-7-docker
total 28
dr-xr-xr-x 1 root root 158 Jan 7 18:59 .
drwx------ 1 root root 488 Feb 1 21:17 ..
-rw-r--r-- 1 root root 11970 Jan 7 18:59 anaconda-post.log
lrwxrwxrwx 1 root root 7 Jan 7 18:58 bin -> usr/bin
drwxr-xr-x 1 root root 0 Jan 7 18:58 dev
drwxr-xr-x 1 root root 1940 Jan 7 18:59 etc
drwxr-xr-x 1 root root 0 Nov 5 2016 home
lrwxrwxrwx 1 root root 7 Jan 7 18:58 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Jan 7 18:58 lib64 -> usr/lib64
drwxr-xr-x 1 root root 0 Nov 5 2016 media
drwxr-xr-x 1 root root 0 Nov 5 2016 mnt
drwxr-xr-x 1 root root 0 Nov 5 2016 opt
drwxr-xr-x 1 root root 0 Jan 7 18:58 proc
dr-xr-x--- 1 root root 120 Jan 7 18:59 root
drwxr-xr-x 1 root root 104 Jan 7 18:59 run
lrwxrwxrwx 1 root root 8 Jan 7 18:58 sbin -> usr/sbin
drwxr-xr-x 1 root root 0 Nov 5 2016 srv
drwxr-xr-x 1 root root 0 Jan 7 18:58 sys
drwxrwxrwt 1 root root 140 Jan 7 18:59 tmp
drwxr-xr-x 1 root root 106 Jan 7 18:58 usr
drwxr-xr-x 1 root root 160 Jan 7 18:58 var
systemd-nspawn
Now test we can test it:
[root@myhomepc ~]# systemd-nspawn --machine=centos-7-docker
Spawning container centos-7-docker on /var/lib/machines/centos-7-docker.
Press ^] three times within 1s to kill container.
[root@centos-7-docker ~]#
[root@centos-7-docker ~]#
[root@centos-7-docker ~]# cat /etc/redhat-release
CentOS Linux release 7.4.1708 (Core)
[root@centos-7-docker ~]#
[root@centos-7-docker ~]# exit
logout
Container centos-7-docker exited successfully.
and now returning to our system:
[root@myhomepc ~]#
[root@myhomepc ~]#
[root@myhomepc ~]# cat /etc/arch-release
Arch Linux release
CS3 Workshop 2018 - Global Scale and the future of Federated Cloud Sharing

English on Björn Schießle - I came for the code but stayed for the freedom | 17:00, Thursday, 01 February 2018
At this years CS3 Workshop in Krakow I presented the current state of Nextcloud’s Global Scale architecture. Probably the most interesting part of the talk was the current development in the area of Federated Cloud Sharing, a central component of Global Scale. Originally, Federated Cloud Sharing was developed by Frank Karlitschek and me in 2014 at ownCloud. These day it enables cloud solutions from ownCloud, Pydio and Nextcloud to exchange files.
As part of Global Scale we will add federated group sharing in the coming months. Further we want to enable apps to provide additional “federated share providers” in order to implement federated calendar sharing, federated contact sharing and more.
The next iteration of Federated Cloud Sharing will be based on the Open Cloud Mesh (OCM) specification. The Open Cloud Mesh initiative by GÉANT aims to turn our original idea of Federated Cloud Sharing into a vendor neutral standard. Something I explicitly support. In the process of implementing OCM we will propose some minor changes and additions to the existing specification to meet all our requirements. Directly after my talk I received a lot of positive feedback from different members of the Open Cloud Mesh initiative. I was especially happy to hear that PowerFolder already started to implement OCM as well and that our friends at Seafile also want to join us. I’m looking forward to work together with the OCM-Community in the following weeks and months in order to make our changes part of the official specification.
I will write a more detailed article once we have a first prototype of our implementation. For now I want to share my presentation slides with you:
(This blog contain some presentation slides, you can see them here.)
Tags: #Nextcloud #cs3 #ocm #cloud #federation #slides
Our future relationship with FSFE
DanielPocock.com - fsfe | 13:19, Thursday, 01 February 2018
Below is an email that has been distributed to the FSFE community today. FSFE aims to be an open organization and people are welcome to discuss it through the main discussion group (join, thread and reply) whether you are a member or not.
 For more information about joining FSFE, local groups, campaigns and other activities please visit the FSFE web site. The "No Cloud" stickers and the Public Money Public Code campaign are examples of initiatives started by FSFE - you can request free stickers and posters by filling in this form.
For more information about joining FSFE, local groups, campaigns and other activities please visit the FSFE web site. The "No Cloud" stickers and the Public Money Public Code campaign are examples of initiatives started by FSFE - you can request free stickers and posters by filling in this form.
Dear FSFE Community,
I'm writing to you today as one of your elected fellowship representatives rather than to convey my own views, which you may have already encountered in my blog or mailing list discussions.
The recent meeting of the General Assembly (GA) decided that the annual elections will be abolished but this change has not yet been ratified in the constitution.
Personally, I support an overhaul of FSFE's democratic processes and the bulk of the reasons for this change are quite valid. One of the reasons proposed for the change, the suggestion that the election was a popularity contest, is an argument I don't agree with: the same argument could be used to abolish elections anywhere.
One point that came up in discussions about the elections is that people don't need to wait for the elections to be considered for GA membership. Matthias Kirschner, our president, has emphasized this to me personally as well, he looks at each new request with an open mind and forwards it to all of the GA for discussion. According to our constitution, anybody can write to the president at any time and request to join the GA. In practice, the president and the existing GA members will probably need to have seen some of your activities in one of the FSFE teams or local groups before accepting you as a member. I want to encourage people to become familiar with the GA membership process and discuss it within their teams and local groups and think about whether you or anybody you know may be a good candidate.
According to the minutes of the last GA meeting, several new members were already accepted this way in the last year. It is particularly important for the organization to increase diversity in the GA at this time.
The response rate for the last fellowship election was lower than in previous years and there is also concern that emails don't reach everybody thanks to spam filters or the Google Promotions tab (if you use gmail). If you had problems receiving emails about the last election, please consider sharing that feedback on the discussion list.
Understanding where the organization will go beyond the extinction of the fellowship representative is critical. The Identity review process, championed by Jonas Oberg and Kristi Progri, is actively looking at these questions. Please contact Kristi if you wish to participate and look out for updates about this process in emails and Planet FSFE. Kristi will be at FOSDEM this weekend if you want to speak to her personally.
I'll be at FOSDEM this weekend and would welcome the opportunity to meet with you personally. I will be visiting many different parts of FOSDEM at different times, including the FSFE booth, the Debian booth, the real-time lounge (K-building) and the Real-Time Communications (RTC) dev-room on Sunday, where I'm giving a talk. Many other members of the FSFE community will also be present, if you don't know where to start, simply come to the FSFE booth. The next European event I visit after FOSDEM will potentially be OSCAL in Tirana, it is in May and I would highly recommend this event for anybody who doesn't regularly travel to events outside their own region.
Changing the world begins with the change we make ourselves. If you only do one thing for free software this year and you are not sure what it is going to be, then I would recommend this: visit an event that you never visited before, in a city or country you never visited before. It doesn't necessarily have to be a free software or IT event. In 2017 I attended OSCAL in Tirana and the Digital-Born Media Carnival in Kotor for the first time. You can ask FSFE to send you some free stickers and posters (online request with optional donation) to give to the new friends you meet on your travels. Change starts with each of us doing something new or different and I hope our paths may cross in one of these places.
For more information about joining FSFE, local groups, campaigns and other activities please visit the FSFE web site.
Please feel free to discuss this through the FSFE discussion group (join, thread and reply)
Wednesday, 31 January 2018
Network-Bound Disk Encryption
Evaggelos Balaskas - System Engineer | 23:25, Wednesday, 31 January 2018
Network-Bound Disk Encryption
I was reading the redhat release notes on 7.4 and came across: Chapter 15. Security
New packages: tang, clevis, jose, luksmeta
Network Bound Disk Encryption (NBDE) allows the user to encrypt root volumes of the hard drives on physical and virtual machines without requiring to manually enter password when systems are rebooted.
That means, we can now have an encrypted (luks) volume that will be de-crypted on reboot, without the need of typing a passphrase!!!
Really - really useful on VPS (and general in cloud infrastructures)
Useful Links
- https://github.com/latchset/tang
- https://github.com/latchset/jose
- https://github.com/latchset/clevis
CentOS 7.4 with Encrypted rootfs
(aka client machine)
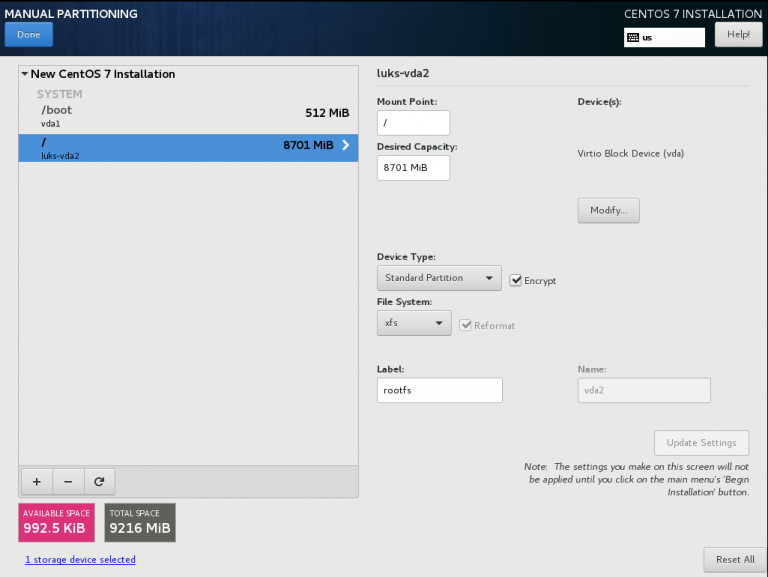
Below is a test centos 7.4 virtual machine with an encrypted root filesystem:
/boot
/
Tang Server
(aka server machine)
Tang is a server for binding data to network presence. This is a different centos 7.4 virtual machine from the above.
Installation
Let’s install the server part:
# yum -y install tang
Start socket service:
# systemctl restart tangd.socket
Enable socket service:
# systemctl enable tangd.socket
TCP Port
Check that the tang server is listening:
# netstat -ntulp | egrep -i systemd
tcp6 0 0 :::80 :::* LISTEN 1/systemdFirewall
Dont forget the firewall:
Firewall Zones
# firewall-cmd --get-active-zones
public
interfaces: eth0
Firewall Port
# firewall-cmd --zone=public --add-port=80/tcp --permanent
or
# firewall-cmd --add-port=80/tcp --permanent
successReload
# firewall-cmd --reload
successWe have finished with the server part!
Client Machine - Encrypted rootfs
Now it is time to configure the client machine, but before let’s check the encrypted partition:
CryptTab
Every encrypted block devices is configured under crypttab file:
[root@centos7 ~]# cat /etc/crypttab
luks-3cc09d38-2f55-42b1-b0c7-b12f6c74200c UUID=3cc09d38-2f55-42b1-b0c7-b12f6c74200c none FsTab
and every filesystem that is static mounted on boot, is configured under fstab:
[root@centos7 ~]# cat /etc/fstab
UUID=c5ffbb05-d8e4-458c-9dc6-97723ccf43bc /boot xfs defaults 0 0
/dev/mapper/luks-3cc09d38-2f55-42b1-b0c7-b12f6c74200c / xfs defaults,x-systemd.device-timeout=0 0 0Installation
Now let’s install the client (clevis) part that will talk with tang:
# yum -y install clevis clevis-luks clevis-dracut
Configuration
with a very simple command:
# clevis bind luks -d /dev/vda2 tang '{"url":"http://192.168.122.194"}'
The advertisement contains the following signing keys:
FYquzVHwdsGXByX_rRwm0VEmFRo
Do you wish to trust these keys? [ynYN] y
You are about to initialize a LUKS device for metadata storage.
Attempting to initialize it may result in data loss if data was
already written into the LUKS header gap in a different format.
A backup is advised before initialization is performed.
Do you wish to initialize /dev/vda2? [yn] y
Enter existing LUKS password:
we’ve just configured our encrypted volume against tang!
Luks MetaData
We can verify it’s luks metadata with:
[root@centos7 ~]# luksmeta show -d /dev/vda2
0 active empty
1 active cb6e8904-81ff-40da-a84a-07ab9ab5715e
2 inactive empty
3 inactive empty
4 inactive empty
5 inactive empty
6 inactive empty
7 inactive empty
dracut
We must not forget to regenerate the initramfs image, that on boot will try to talk with our tang server:
[root@centos7 ~]# dracut -f
Reboot
Now it’s time to reboot!
A short msg will appear in our screen, but in a few seconds and if successfully exchange messages with the tang server, our server with de-crypt the rootfs volume.
Tang messages
To finish this article, I will show you some tang msg via journalct:
Initialization
Getting the signing key from the client on setup:
Jan 31 22:43:09 centos7 systemd[1]: Started Tang Server (192.168.122.195:58088).
Jan 31 22:43:09 centos7 systemd[1]: Starting Tang Server (192.168.122.195:58088)...
Jan 31 22:43:09 centos7 tangd[1219]: 192.168.122.195 GET /adv/ => 200 (src/tangd.c:85)reboot
Client is trying to decrypt the encrypted volume on reboot
Jan 31 22:46:21 centos7 systemd[1]: Started Tang Server (192.168.122.162:42370).
Jan 31 22:46:21 centos7 systemd[1]: Starting Tang Server (192.168.122.162:42370)...
Jan 31 22:46:22 centos7 tangd[1223]: 192.168.122.162 POST /rec/Shdayp69IdGNzEMnZkJasfGLIjQ => 200 (src/tangd.c:168)
Tuesday, 30 January 2018
Fair communication requires mutual consent
DanielPocock.com - fsfe | 20:33, Tuesday, 30 January 2018
I was pleased to read Shirish Agarwal's blog in reply to the blog I posted last week Do the little things matter?
Given the militaristic theme used in my own post, I was also somewhat amused to see news this week of the Strava app leaking locations and layouts of secret US military facilities like Area 51. What a way to mark International Data Privacy Day. Maybe rather than inadvertently misleading people to wonder if I was suggesting that Gmail users don't make their beds, I should have emphasized that Admiral McRaven's boot camp regime for Navy SEALS needs to incorporate some of my suggestions about data privacy?

A highlight of Agarwal's blog is his comment I usually wait for a day or more when I feel myself getting inflamed/heated and I wish this had occurred in some of the other places where my ideas were discussed. Even though my ideas are sometimes provocative, I would kindly ask people to keep point 2 of the Debian Code of Conduct in mind, Assume good faith.
One thing that became clear to me after reading Agarwal's blog is that some people saw my example one-line change to Postfix's configuration as a suggestion that people need to run their own mail server. In fact, I had seen such comments before but I hadn't realized why people were reaching a conclusion that I expect everybody to run a mail server. The purpose of that line was simply to emphasize the content of the proposed bounce message, to help people understand, the receiver of an email may never have agreed to Google's non-privacy policy but if you do use Gmail, you impose that surveillance regime on them, and not just yourself, if you send them a message from a Gmail account.
Communication requires mutual agreement about the medium. Think about it another way: if you go to a meeting with your doctor and some stranger in a foreign military uniform is in the room, you might choose to leave and find another doctor rather than communicate under surveillance.
As it turns out, many people are using alternative email services, even if they only want a web interface. There is already a feature request discussion in ProtonMail about letting users choose to opt-out of receiving messages monitored by Google and send back the bounce message suggested in my blog. Would you like to have that choice, even if you didn't use it immediately? You can vote for that issue or leave your own feedback comments in there too.
Imagine the world's biggest Kanban / Scrumboard
DanielPocock.com - fsfe | 18:52, Tuesday, 30 January 2018
Imagine a Kanban board that could aggregate issues from multiple backends, including your CalDAV task list, Bugzilla systems (Fedora, Mozilla, GNOME communities), Github issue lists and the Debian Bug Tracking System, visualize them together and coordinate your upstream fixes and packaging fixes in a single sprint.
It is not so farfetched - all of those systems already provide read access using iCalendar URLs as described in my earlier blog. There are REST APIs to manipulate most of them too. Why not write a front end to poll them and merge the content into a Kanban board view?
We've added this as a potential GSoC project using Python and PyQt.
If you'd like to see this or any of the other proposed projects go ahead, you don't need to be a Debian Developer to suggest ideas, refer a student or be a co-mentor. Many of our projects have relevance in multiple communities. Feel free to get in touch with us through the debian-outreach mailing list.

Sunday, 28 January 2018
Let's talk about Hacking (EPFL, Lausanne, 20 February 2018)
DanielPocock.com - fsfe | 21:54, Sunday, 28 January 2018
I've been very fortunate to have the support from several free software organizations to travel to events around the world and share what I do with other people. It's an important mission in a world where technology is having an increasing impact on our lives. With that in mind, I'm always looking for ways to improve my presentations and my presentation skills. As part of mentoring programs like GSoC and Outreachy, I'm also looking for ways to help newcomers in our industry to maximize their skills in communicating about the great work they do when they attend their first event.
With that in mind, one of the initiatives I've taken this year is participating in the Toastmasters organization. I've attended several meetings of the Toastmasters group at EPFL and on 20 February 2018, I'll give my first talk there on the subject of Hacking.
If you live in the area, please come along. Entrance is free, there is plenty of parking available in the evening and it is close to the metro too. Please try to arrive early so as not to disrupt the first speaker. Location map, Add to your calendar.

The Toastmasters system encourages participants to deliver a series of ten short (5-7 minute) speeches, practicing a new skill each time.
The first of these, the The Ice Breaker, encourages speakers to begin using their existing skills and experience. When I read that in the guide, I couldn't help wondering if that is a cue to unleash some gadget on the audience.
Every group provides a system for positive feedback, support and mentoring for speakers at every level. It is really wonderful to see the impact that this positive environment has for everybody. At the EPFL meetings, I've met a range of people, some with far more speaking experience than me but most of them are working their way through the first ten speeches.
One of the longest running threads on the FSFE discussion list in 2017 saw several people arguing that it is impossible to share ideas without social media. If you have an important topic you want to share with the world, could public speaking be one way to go about it and does this possibility refute the argument that we "need" social media to share ideas? Is it more valuable to learn how to engage with a small audience for five minutes than to have an audience of hundreds on Twitter who scrolls past you in half a second as they search for cat photos? If you are not in Lausanne, you can easily find a Toastmasters club near you anywhere in the world.

Friday, 26 January 2018
Local OsmAnd and Geo URL's

Ramblings of a sysadmin (Posts about planet-fsfe) | 22:50, Friday, 26 January 2018
Earlier this year I went on a long holiday to Japan and China. I have an Android phone and am a very big fan of OpenStreetMap. So I used OsmAnd (which uses OpenStreetMap data) to navigate through those countries. I made a spreadsheet with LibreOffice, which included a few links to certain location which are hard to find or do not have an address. Then I exported that .ods to a .pdf and was able to click on the links, which then openend perfectly in OsmAnd.
The URL I was able to use in my PDF document was this one (of course you can substitute longitude and latitude):
http://osmand.net/go?lat=51.4404&lon=4.3294&z=16
And then I helped a friend of mine with something similar to use on a website. Of course the link above did not work. After a short look on Wikipedia I found the page about Geo URI scheme. Constructing a URL with the Geo URI scheme will trigger the default navigation application on a mobile device to open the location. And of course, here you can also substitute the longitude and latitude.
<a href="geo:51.4404,4.3294;u=15">Hoogerheide</a>
Which will result in this link (usable on mobile devices) and of course you can still create a "normal one" for non-mobile device such as this one.
Thursday, 25 January 2018
Do the little things matter?
DanielPocock.com - fsfe | 20:44, Thursday, 25 January 2018
In a widely shared video, US Admiral McRaven addressing University of Texas at Austin's Class of 2014 chooses to deliver a simple message: make your bed every day.
A highlight of this talk is the quote The little things in life matter. If you can't do the little things right, you'll never be able to do the big things right.
In the world of free software engineering, we have lofty goals: the FSF's High Priority Project list identifies goals like private real-time communication, security and diversity in our communities. Those deploying free software in industry have equally high ambitions, ranging from self-driving cars to beating the stock market.
Yet over and over again, we can see people taking little shortcuts and compromises. If Admiral McRaven is right, our failure to take care of little decisions, like how we choose an email provider, may be the reason those big projects, like privacy or diversity, appear to be no more than a pie-in-the-sky.
 The IT industry has relatively few regulations compared to other fields such as aviation, medicine or even hospitality. Consider a doctor who re-uses a syringe - how many laws would he be breaking? Would he be violating conditions of his insurance? Yet if an IT worker overlooks the contempt for the privacy of Gmail users and their correspondents that is dripping off the pages of the so-called "privacy" policy, nobody questions them. Many people will applaud their IT staff for choices or recommendations like this, because, of course, "it works". A used syringe "just works" too, but who would want one of those?
The IT industry has relatively few regulations compared to other fields such as aviation, medicine or even hospitality. Consider a doctor who re-uses a syringe - how many laws would he be breaking? Would he be violating conditions of his insurance? Yet if an IT worker overlooks the contempt for the privacy of Gmail users and their correspondents that is dripping off the pages of the so-called "privacy" policy, nobody questions them. Many people will applaud their IT staff for choices or recommendations like this, because, of course, "it works". A used syringe "just works" too, but who would want one of those?
Google's CEO Eric Schmidt tells us that if you don't have anything to hide, you don't need to worry.
Compare this to the advice of Sun Tzu, author of the indispensable book on strategy, The Art of War. The very first chapter is dedicated to estimating, calculating and planning: what we might call data science today. Tzu unambiguously advises to deceive your opponent, not to let him know the truth about your strengths and weaknesses.
In the third chapter, Offense, Tzu starts out that The best policy is to take a state intact ... to subdue the enemy without fighting is the supreme excellence. Surely this is only possible in theory and not in the real world? Yet when I speak to a group of people new to free software and they tell me "everybody uses Windows in our country", Tzu's words take on meaning he never could have imagined 2,500 years ago.
In many tech startups and even some teams in larger organizations, the oft-repeated mantra is "take the shortcut". But the shortcuts and the things you get without paying anything, without satisfying the conditions of genuinely free software, compromises such as Gmail, frequently involve giving up a little bit too much information about yourself: otherwise, why would they leave the bait out for you? As Mr Tzu puts it, you have just been subdued without fighting.
In one community that has taken a prominent role in addressing the challenges of diversity, one of the leaders recently expressed serious concern that their efforts had been subdued in another way: Gmail's Promotions Tab. Essential emails dispatched to people who had committed to their program were routinely being shunted into the Promotions Tab along with all that marketing nonsense that most people never asked for and the recipients never saw them.
I pointed out many people have concerns about Gmail and that I had been having thoughts about simply blocking it at my mail server. It is quite easy to configure a mail server to send an official bounce message, for example, in Postfix, it is just one line in the /etc/postfix/access file:
gmail.com REJECT The person you are trying to contact hasn't accepted Gmail's privacy policy. Please try sending the email from a regular email provider.
(NOTE: some people read this and thought I meant everybody should run their own email server, but the above code is just an example to encourage discussion. There is discussion about adding a similar feature to block messages from Gmail to ProtonMail webmail accounts, so anybody can do this without their own server and take back control over their privacy)
Some communities could go further, refusing to accept Gmail addresses on mailing lists or registration forms: would that be the lesser evil compared to a miserable fate in Promotions Tab limbo?
I was quite astounded at the response: several people complained that this was too much for participants to comply with (the vast majority register with a Gmail address) or that it was even showing all Gmail users contempt (can't they smell the contempt for users in the aforementioned Gmail "privacy" policy?). Nobody seemed to think participants could cope with that and if we hope these people are going to be the future of diversity, that is really, really scary.
Personally, I have far higher hopes for them: just as Admiral McRaven's Navy SEALS are conditioned to make their bed every day at boot camp, people entering IT, especially those from under-represented groups, need to take pride in small victories for privacy and security, like saying "No" each and every time they have the choice to give up some privacy and get something "free", before they will ever hope to accomplish big projects and change the world.
If they don't learn these lessons at the outset, like the survival and success habits drilled into soldiers during boot-camp, will they ever? If programs just concentrate on some "job skills" and gloss over the questions of privacy and survival in the information age, how can they ever deliver the power shift that is necessary for diversity to mean something?
Come and share your thoughts on the FSFE discussion list (join, thread and reply).
Please also see the subsequent blog on this topic, Fair communication requires mutual consent

Wednesday, 24 January 2018
What is DNS Privacy and how to set it up for OpenWRT
Free Software – | 19:08, Wednesday, 24 January 2018
The Domain Name System (DNS) enables your computer to find the actual addresses of other computers. So when you type fsfe.org in your browser, the DNS tells you that 217.69.89.176 is the actual IP address for fsfe.org. It needs this real address to make a connection to that server and present the website hosted there to you.
DNS requests leak a lot of data to anybody who can read your network traffic, because they are typically not encrypted. Every server/site you visit will be leaked in a DNS request.
To solve this problem, there is DNS Privacy, a project dedicated to improve privacy around DNS. The most obvious solution is to encrypt the DNS requests, so someone looking at your internet traffic doesn’t see anymore which sites you visit just by looking into your DNS queries.
There’s many different ways to encrypt this information. I will focus on DNS over TLS as this seems to be the best solution at the moment and is relatively easy to set up.
Everything you own that is connected to the internet is making DNS requests. You could of course try to set all of these devices up for DNS over TLS individually, but that is mostly not even possible and a lot of work. If you just have one local desktop or laptop computer, you can use Stubby a local DNS Privacy stub resolver. The solution I recommend is to set up DNS Privacy directly on your router, so all devices entering the internet via this router (and using it for DNS queries) will benefit from it.
DNS over TLS for OpenWRT
OpenWRT (or LEDE) is a Free Software operating system for routers. The following assumes that you are running the latest version of OpenWRT (at the moment LEDE 17.01.4).
Log into your router via ssh and then run:
# Install unbound (System -> Software -> Find package: unbound -> Install) opkg install unbound
Add some more privacy options to the unbound server config:
cat >> /etc/unbound/unbound_srv.conf <<UNBOUND_SERVER_CONF do-tcp: yes prefetch: yes qname-minimisation: yes rrset-roundrobin: yes use-caps-for-id: yes UNBOUND_SERVER_CONF # Don't let each server know the next recursion. uci set 'unbound.@unbound[0].query_minimize=1'
Now, the important part comes. It tells unbound to forward all (except local) DNS requests to special DNS resolvers that allow you to connect encrypted with TLS on port 853.
cat >> /etc/unbound/unbound_ext.conf <<UNBOUND_FORWARD_CONF
forward-zone:
name: "."
forward-addr: 9.9.9.9@853 # quad9.net primary
forward-addr: 149.112.112.112@853 # quad9.net secondary
forward-addr: 145.100.185.15@853 # Surfnet primary
forward-addr: 145.100.185.16@853 # Surfnet secondary
forward-addr: 185.49.141.37@853 # getdnsapi.net
forward-ssl-upstream: yes
UNBOUND_FORWARD_CONF
The last option turns on DNS over TLS.
Now, you just need to move the existing dnsmasq server aside, so unbound can answer your devices DNS queries.
# Move dnsmasq to port 53535 where it will still serve local DNS from DHCP # Network -> DHCP & DNS -> Advanced Settings -> DNS server port to 53535 uci set 'dhcp.@dnsmasq[0].port=53535' # Configure dnsmasq to send a DNS Server DHCP option with its LAN IP # since it does not do this by default when port is configured. uci add_list "dhcp.lan.dhcp_option=option:dns-server,$(uci get network.lan.ipaddr)" uci set 'unbound.@unbound[0].dhcp_link=dnsmasq' # Save & Apply (will restart dnsmasq, DNS unreachable until unbound is up) uci commit # Restart (or start) unbound (System -> Startup -> unbound -> Restart) /etc/init.d/unbound restart
Now you can test your DNS queries:
nslookup fsfe.org
If this works, your DNS requests should now be made over TLS and even cached locally by unbound. If you have problems, try the logread command to see what is going on. If you want to further tune the settings, checkout OpenWRT’s awesome unbound README.
Note: The DNS servers you use can of course still see your requests and the domains in them. Only passive network observers get locked out by using DNS over TLS.
<script type="text/javascript"> (function () { var s = document.createElement('script'); var t = document.getElementsByTagName('script')[0]; s.type = 'text/javascript'; s.async = true; s.src = '/wp-content/libs/SocialSharePrivacy/scripts/jquery.socialshareprivacy.min.autoload.js'; t.parentNode.insertBefore(s, t); })(); </script>apt-get install more contributors
DanielPocock.com - fsfe | 11:21, Wednesday, 24 January 2018
Every year I participate in a number of initiatives introducing people to free software and helping them make a first contribution. After all, making the first contribution to free software is a very significant milestone on the way to becoming a leader in the world of software engineering. Anything we can do to improve this experience and make it accessible to more people would appear to be vital to the continuation of our communities and the solutions we produce.
During the time I've been involved in mentoring, I've observed that there are many technical steps in helping people make their first contribution that could be automated. While it may seem like creating SSH and PGP keys is not that hard to explain, wouldn't it be nice if we could whisk new contributors through this process in much the same way that we help people become users with the Debian Installer and Synaptic?
Paving the path to a first contribution
Imagine the following series of steps:
- Install Debian
- apt install new-contributor-wizard
- Run the new-contributor-wizard (sets up domain name, SSH, PGP, calls apt to install necessary tools, procmail or similar filters, join IRC channels, creates static blog with Jekyll, ...)
- write a patch, git push
- write a blog about the patch, git push
Steps 2 and 3 can eliminate a lot of "where do I start?" head-scratching for new contributors and it can eliminate a lot of repetitive communication for mentors. In programs like GSoC and Outreachy, where there is a huge burst of enthusiasm during the application process (February/March), will a tool like this help a higher percentage of the applicants make a first contribution to free software? For example, if 50% of applicants made a contribution last March, could this tool raise that to 70% in March 2019? Is it likely more will become repeat contributors if their first contribution is achieved more quickly after using a tool like this? Is this an important pattern for the success of our communities? Could this also be a useful stepping stone in the progression from being a user to making a first upload to mentors.debian.net?
Could this wizard be generic enough to help multiple communities, helping people share a plugin for Mozilla, contribute their first theme for Drupal or a package for Fedora?
Not just for developers
Notice I've deliberately used the word contributor and not developer. It takes many different people with different skills to build a successful community and this wizard will also be useful for people who are not writing code.
What would you include in this wizard?
Please feel free to add ideas to the wiki page.
All projects really need a couple of mentors to support them through the summer and if you are able to be a co-mentor for this or any of the other projects (or even proposing your own topic) now is a great time to join the debian-outreach list and contact us. You don't need to be a Debian Developer either and several of these projects are widely useful outside Debian.
Ready Player One by Ernest Cline
Evaggelos Balaskas - System Engineer | 10:51, Wednesday, 24 January 2018
Ready Player One by Ernest Cline
I’ve listened to the audiobook, Narrated by Wil Wheaton.
The book is AMAZING! Taking a trip down memory lane to ’80s pop culture, video games, music & movies. A sci-fi futuristic book that online gamers are trying to solve puzzles on a easter egg hunt for the control of oasis, a virtual reality game.
You can find more info here
Tuesday, 23 January 2018
FOSS Backstage - CfP open
Inductive Bias | 16:21, Tuesday, 23 January 2018
It's almost ten years ago that I attended my first ApacheCon EU in Amsterdam. I wasn't entirely new to the topic of open source or free software. I attended several talks on Apache Lucene, Apache Solr, Hadoop, Tomcat, httpd (I still remember that the most impressive stories didn't necessarily come from the project members, but from downstream users. They were the ones authorized to talk publicly about what could be done with the project - and often became committers themselves down the road.With "community over code" being one of the main values at Apache, ApacheCon also hosted several non-technical tracks: Open source and business, Open Development (nowadays better known as Inner Source), Open Source project management, project governance, an Apache Way talk. Over the past decade one learning survived any wave of tech buzzword: At the end of the day, success in Open Source (much like in any project) is defined by how well the project is run (read: managed). Reflecting on that the idea was born to create a space to discuss just these topics: What does it take to be "Leading the wave of open source"?
As announced on Berlin Buzzwords we (that is Isabel Drost-Fromm, Stefan Rudnitzki as well as the eventing team over at newthinking communications GmbH) are working on a new conference in summer in Berlin. The name of this new conference will be "FOSS Backstage". Backstage comprises all things FOSS governance, open collaboration and how to build and manage communities within the open source space.
Submission URL: Call for Presentations
The event will comprise presentations on all things FOSS governance, decentralised decision making, open collaboration. We invite you to submit talks on the topics: FOSS project governance, collaboration, community management. Asynchronous/ decentralised decision making. Vendor neutrality in FOSS, sustainable FOSS, cross team collaboration. Dealing with poisonous people. Project growth and hand-over. Trademarks. Strategic licensing. While it's primarily targeted at contributions from FOSS people, we would love to also learn more on how typical FOSS collaboration models work well within enterprises. Closely related topics not explicitly listed above are welcome.
Important Dates (all dates in GMT +2)
Submission deadline: February 18th, 2018.
Conference: June, 13th/14th, 2018
High quality talks are called for, ranging from principles to practice. We are looking for real world case studies, background on the social architecture of specific projects and a deep dive into cross community collaboration. Acceptance notifications will be sent out soon after the submission deadline. Please include your name, bio and email, the title of the talk, a brief abstract in English language.
We have drafted the submission form to allow for regular talks, each 45 min in length. However you are free to submit your own ideas on how to support the event: If you would like to take our attendees out to show them your favourite bar in Berlin, please submit this offer through the CfP form. If you are interested in sponsoring the event (e.g. we would be happy to provide videos after the event, free drinks for attendees as well as an after-show party), please contact us.
Schedule and further updates on the event will be published soon on the event web page.
Please re-distribute this CfP to people who might be interested.
Contact us at:
newthinking communications GmbH
Schoenhauser Allee 6/7
10119 Berlin, Germany
info@foss-backstage.de
Looking forward to meeting you all in person in summer :)
Monday, 22 January 2018
Concise Attribute Initialisation in Lichen… and Python?
Paul Boddie's Free Software-related blog » English | 21:50, Monday, 22 January 2018
In my review of 2017, I mentioned a project of mine to make a Python-like language called Lichen that is more amenable to compile-time analysis than Python is, while still having a feature set I might actually be able to use in “real” programs one day. There are a lot of different “moving parts” in the Lichen toolchain, and being preoccupied with various other projects and activities, I haven’t been able to get back into working on it properly in the last few months.
Recently, as I found myself writing Python code for another of my projects, I got to wondering about something in Python that can occur a lot: the initialisation of instance attributes. Here is a classic example:
class Point:
def __init__(self, x, y):
self.x = x
self.y = y
# For illustration, here is how the class is used...
p = Point(640, 512)
print p.x, p.y # 640 512
In this example, having to assign the parameter values to the instance attributes is not much of a hardship. But with more verbose initialisation methods with more parameters and more attributes involved, writing everything out can be tiresome. Moreover, mistakes can be made, particularly if the interfaces and structures are evolving. Naturally, there are a range of improvements and measures that attempt to alleviate the problem. Here is the most obvious:
class Point:
def __init__(self, x, y):
self.x = x; self.y = y
This just puts the same statements on one line, so let us move beyond it to the next attempt:
class Point:
def __init__(self, x, y):
self.x, self.y = x, y
Here, we are actually performing “tuple assignment”, with the parameter values being placed in a tuple whose elements are then assigned to the names in the corresponding positions on the left-hand side of the assignment.
Now, without any Python “magic”, this is probably as far as you can get. The “magic” involves introspection and a feature known as “decorators” (which Lichen doesn’t support) to let us use something like this:
class Point:
@initialising("x", "y")
def __init__(self, x, y):
pass
Here, I am taking inspiration from a collection of actual suggestions and solutions, but none of them look like the above. Indeed, many of them take the approach of initialising attributes using every parameter in the method signature which isn’t always what you want, although it does seem to be requested every now and again.
Although the above example looks quite nice, the mechanism responsible for performing the attribute assignments will not look as nice, and so I won’t show it here. And unless a mode is supported where the names can be omitted, thus initialising attributes using all parameters (except self) when you do want to, it is perhaps tiresome to have to write the names out again somewhere else, even more so as strings.
You will also find people advocating more transparent use of the ** catch-all parameter (also not supported by Lichen), sometimes in response to people worried that writing out lots of assignments is a sign of bad code. This yields solutions like this one:
class Point:
def __init__(self, **kw):
for name in ("x", "y"):
setattr(self, name, kw.get(name))
But keeping named parameters in the signature helps to prevent certain kinds of errors, which is one reason why I don’t intend to support catch-all parameters in Lichen.
But what I wondered is why Python never supported something closer to C++’s initialisation lists. In C++, we might write the code somewhat as follows:
class Point
{
Number x, y;
public:
Point(Number x, Number y) : x(x), y(y) {};
}
Here, it is evident that repetition occurs just as in the “magic” Python example, which is something I might want to eliminate. Maybe we would want to have a shorthand for attribute initialisation within the parameter list itself. And then I thought of a possible syntax:
class Point:
def __init__(self, .x, .y):
pass
So, any parameter employing a dot before its name would result in the assignment of its value to the instance attribute having the same name. Of course, this wouldn’t support a parameter with one name having its value assigned to an attribute with another name, but I thought it best to stick to the simple cases. “Why not add this to Lichen?” I thought.
And in line with not getting too immersed in the toolchain straight away after such a long break, I decided on some rather simple semantics for this feature: dot-prefixed names would still exist as local names; dot-prefixing would just be a form of shorthand meaning that an assignment would be generated at the very start of the function body. So, the above would really translate to the very first example given at the start of this article or, indeed, the second one which is equivalent and is reproduced below:
# Lichen-only... # Python and Lichen...
class Point: class Point:
def __init__(self, .x, .y): def __init__(self, x, y):
pass self.x = x; self.y = y
Keeping the sophistication of the feature at an unambitious level, besides letting me slowly familiarise myself again with the code, also helps to deal with potential conflicts with other mechanisms. For example, what if someone wanted to employ a name twice – once dot-prefixed, once unprefixed – like this…?
class Point:
def __init__(self, .x, .y, x):
self.intensity = x ** 2
By asserting that the dot-prefixed x is really just x that also initialises the attribute of the same name, we can fall back on the normal rules around parameters and forbid such duplicate names without having to think very hard about temporary names or more exotic mechanisms that might be used to initialise attributes directly. One other thing worth mentioning is that I don’t reserve the use of such parameters for the exclusive use of initialiser methods, so other applications are possible. For example:
class Point:
def __init__(.x, .y): pass
def update(.x, .y): pass
Here, I also omit self because Lichen defines it as always being present in methods, anyway. And we could actually make the update method an alias of the initialiser method, too, but let us not get too carried away!
Fortunately, I adopted a parser framework in Lichen that was originally written for PyPy that allows relatively straightforward modification of the language grammar. Conveniently, the grammar changes required for this feature are minimal and I don’t even have to add any extra tokens. That made me wonder whether such a syntax had been suggested for Python at some point or other. Some quick searches haven’t yielded any results, and I can’t be bothered to trawl the different mailing list archives to find mentions of such features. I can easily imagine that such a feature might have been discussed rather early in Python’s lifetime, possibly in the mid-1990s.
Arguments for new syntax in Python are often met with arguments against “syntactic sugar”, with such “sugar” introducing more convenient notation or a form of shorthand for particular operations. Over the years, people have argued for more concise ways of referencing instance attributes and class attributes instead of using the almost-special self name (that is rather more special in Lichen). Compound assignments to instance attributes have probably been discussed, too, maybe proposing things like this:
# Compound assignment idea... # Equivalent assignment... self.(x, y) = x, y self.x, self.y = x, y
In response to such suggestions, people seem to be asked how often they need to write such things, whether it is really such a burden to do so, and whether their programming tools cannot help them write out the conventional assignments semi-automatically instead. Proposed general language constructs may well risk introducing conflicts with other language features in unanticipated ways, and if such constructs only ever get used in certain, rather limited, circumstances then one can justifiably ask whether it is really worth the effort to support them. They will, after all, need people to implement them, test them, maintain them, and keep fixing them long into the future.
As is evident from the discussion of the problem of concise initialisation, Python’s community has grown accustomed to solving simple problems in fairly complicated ways using general mechanisms introduced to support broad classes of functionality. Decorators were introduced into Python as a way of inserting extra code around methods and functions to modify or extend their behaviour, allowing people to tackle such problems by getting that extra code to initialise attributes or to do many other weird, wild and wonderful things. Providing such mechanisms lets the language designers send people elsewhere when those people descend on the designers demanding a quick syntactic fix for a specific problem they might be having.
But it really does surprise me that something as simple as dot-prefixing parameter names never managed to get suggested and quickly introduced into an early version of Python. I did wonder whether other Python-inspired languages might have subconsciously inspired me, but a brief perusal of the Boo, Cobra, Delight and Genie documentation turned up nothing. And so, without any more insight into my inspiration, that is the tale of my first experiment in extending Lichen’s syntax beyond that of Python.
Update
I finally remembered where I had seen the dot-prefixed name notation before. When initialising structures in C, you can explicitly indicate a structure member when specifying a value, and I do this all the time in the code generated for Lichen programs. I even define macros that use this feature. For example:
#define __INTVALUE(VALUE) ((__attr) {.intvalue=((VALUE) << 1) | 1})
So I suppose it shows how long it has been since I had to look at that part of the toolchain! Of course, this is directly initialising a structure member by indicating a value, whereas the Lichen syntax enhancement associates an attribute, which is similar to a member, with a parameter received in a method call. But there are some similarities in purpose, nevertheless.
Keeping an Irish home warm and free in winter
DanielPocock.com - fsfe | 09:20, Monday, 22 January 2018
The Irish Government's Better Energy Homes Scheme gives people grants from public funds to replace their boiler and install a zoned heating control system.
Having grown up in Australia, I think it is always cold in Ireland and would be satisfied with a simple control switch with a key to make sure nobody ever turns it off but that isn't what they had in mind for these energy efficiency grants.
Having recently stripped everything out of the house, right down to the brickwork and floorboards in some places, I'm cautious about letting any technologies back in without checking whether they are free and trustworthy.

This issue would also appear to fall under the scope of FSFE's Public Money Public Code campaign.
Looking at the last set of heating controls in the house, they have been there for decades. Therefore, I can't help wondering, if I buy some proprietary black box today, will the company behind it still be around when it needs a software upgrade in future? How many of these black boxes have wireless transceivers inside them that will be compromised by security flaws within the next 5-10 years, making another replacement essential?
With free and open technologies, anybody who is using it can potentially make improvements whenever they want. Every time a better algorithm is developed, if all the homes in the country start using it immediately, we will always be at the cutting edge of energy efficiency.
 Are you aware of free and open solutions that qualify for this grant funding? Can a solution built with devices like Raspberry Pi and Arduino qualify for the grant?
Are you aware of free and open solutions that qualify for this grant funding? Can a solution built with devices like Raspberry Pi and Arduino qualify for the grant?
Please come and share any feedback you have on the FSFE discussion list (join, reply to the thread).

Sunday, 21 January 2018
Fabric MiniTutorial
Evaggelos Balaskas - System Engineer | 20:27, Sunday, 21 January 2018
Fabric
Fabric is a Python (2.5-2.7) library and command-line tool for streamlining the use of SSH for application deployment or systems administration tasks.
You can find the documentation here
Installation
# yum -y install epel-release
# yum -y install fabric
Hello World
# cat > fabfile.py <<EOF
> def hello():
> print("Hello world!")
>
> EOFand run it
# fab hello -f ./fabfile.py
Hello world!
Done.A more complicated example
def HelloWorld():
print("Hello world!")
def hello(name="world"):
print("Hello %s!" % name )# fab HelloWorld -f ./fabfile.py
Hello world!
Done.
# fab hello -f ./fabfile.py
Hello world!
Done.
# fab hello:name=ebal -f ./fabfile.py
Hello ebal!
Done.
A remote example
from fabric.api import run , env
env.use_ssh_config = True
def HelloWorld():
print("Hello world!")
def hello(name="world"):
print("Hello %s!" % name )
def uptime():
run('uptime')
ssh configuration file
with the below variable declaration
(just remember to import env)
fabric can use the ssh configuration file of your system
env.use_ssh_config = Trueand run it against server test
$ fab -H test uptime -f ./fabfile.py
[test] Executing task 'uptime'
[test] run: uptime
[test] out: 20:21:30 up 10 days, 11 min, 1 user, load average: 0.00, 0.00, 0.00
[test] out:
Done.
Disconnecting from 192.168.122.1:22... done.
Planet FSFE (en):  RSS 2.0 |
RSS 2.0 |  Atom |
Atom |  FOAF |
FOAF | 

 /127.0.0.?
/127.0.0.?
 /var/log/fsfe/flx » planet-en
/var/log/fsfe/flx » planet-en
 Albrechts Blog
Albrechts Blog
 Alessandro at FSFE » English
Alessandro at FSFE » English
 Alessandro's blog
Alessandro's blog
 Alina Mierlus - Building the Freedom » English
Alina Mierlus - Building the Freedom » English
 Andrea Scarpino's blog
Andrea Scarpino's blog
 André Ockers on Free Software » English
André Ockers on Free Software » English
 Being Fellow #952 of FSFE » English
Being Fellow #952 of FSFE » English
 Bela's Internship Blog
Bela's Internship Blog
 Bernhard's Blog
Bernhard's Blog
 Bits from the Basement
Bits from the Basement
 Blog of Martin Husovec
Blog of Martin Husovec
 Blog » English
Blog » English
 Blog – Think. Innovation.
Blog – Think. Innovation.
 Bobulate
Bobulate
 Brian Gough's Notes
Brian Gough's Notes
 Carlo Piana :: Law is Freedom ::
Carlo Piana :: Law is Freedom ::
 Ciarán's free software notes
Ciarán's free software notes
 Colors of Noise - Entries tagged planetfsfe
Colors of Noise - Entries tagged planetfsfe
 Communicating freely
Communicating freely
 Computer Floss
Computer Floss
 Daniel Martí's blog
Daniel Martí's blog
 Daniel's FSFE blog
Daniel's FSFE blog
 DanielPocock.com - fsfe
DanielPocock.com - fsfe
 David Boddie - Updates (Full Articles)
David Boddie - Updates (Full Articles)
 Don't Panic » English Planet
Don't Panic » English Planet
 ENOWITTYNAME
ENOWITTYNAME
 English Planet – Dreierlei
English Planet – Dreierlei
 English on Björn Schießle - I came for the code but stayed for the freedom
English on Björn Schießle - I came for the code but stayed for the freedom
 English – Kristi Progri
English – Kristi Progri
 English – Max's weblog
English – Max's weblog
 English — mina86.com
English — mina86.com
 Escape to freedom
Escape to freedom
 Evaggelos Balaskas - System Engineer
Evaggelos Balaskas - System Engineer
 FLOSS – Creative Destruction & Me
FLOSS – Creative Destruction & Me
 FSFE Fellowship Vienna » English
FSFE Fellowship Vienna » English
 FSFE interviews its Fellows
FSFE interviews its Fellows
 FSFE – Patis Blog
FSFE – Patis Blog
 Fellowship News
Fellowship News
 Fellowship News » Page not found
Fellowship News » Page not found
 Florian Snows Blog » en
Florian Snows Blog » en
 Frederik Gladhorn (fregl) » FSFE
Frederik Gladhorn (fregl) » FSFE
 Free Software & Digital Rights Noosphere
Free Software & Digital Rights Noosphere
 Free Software with a Female touch
Free Software with a Female touch
 Free Software –
Free Software –
 Free Software – Frank Karlitschek_
Free Software – Frank Karlitschek_
 Free Software – GLOG
Free Software – GLOG
 Free Software – hesa's Weblog
Free Software – hesa's Weblog
 Free as LIBRE
Free as LIBRE
 Free speech is better than free beer » English
Free speech is better than free beer » English
 Free, Easy and Others
Free, Easy and Others
 From Out There
From Out There
 Graeme's notes » Page not found
Graeme's notes » Page not found
 Green Eggs and Ham
Green Eggs and Ham
 Handhelds, Linux and Heroes
Handhelds, Linux and Heroes
 HennR's FSFE blog
HennR's FSFE blog
 Henri Bergius
Henri Bergius
 Hook’s Humble Homepage
Hook’s Humble Homepage
 Hugo - FSFE planet
Hugo - FSFE planet
 Inductive Bias
Inductive Bias
 Jelle Hermsen » English
Jelle Hermsen » English
 Jens Lechtenbörger » English
Jens Lechtenbörger » English
 Karsten on Free Software
Karsten on Free Software
 Losca
Losca
 MHO
MHO
 Mario Fux
Mario Fux
 Martin's notes - English
Martin's notes - English
 Matej's blog » FSFE
Matej's blog » FSFE
 Matthias Kirschner's Web log - fsfe
Matthias Kirschner's Web log - fsfe
 Myriam's blog
Myriam's blog
 Mäh?
Mäh?
 Nice blog
Nice blog
 Nico Rikken » fsfe
Nico Rikken » fsfe
 Nicolas Jean's FSFE blog » English
Nicolas Jean's FSFE blog » English
 Norbert Tretkowski
Norbert Tretkowski
 PB's blog » en
PB's blog » en
 Paul Boddie's Free Software-related blog » English
Paul Boddie's Free Software-related blog » English
 Planet FSFE on Iain R. Learmonth
Planet FSFE on Iain R. Learmonth
 Posts - A blog
Posts - A blog
 Posts on Hannes Hauswedell's homepage
Posts on Hannes Hauswedell's homepage
 Pressreview
Pressreview
 Ramblings of a sysadmin (Posts about planet-fsfe)
Ramblings of a sysadmin (Posts about planet-fsfe)
 Rekado
Rekado
 Repentinus » English
Repentinus » English
 Riccardo (ruphy) Iaconelli - blog
Riccardo (ruphy) Iaconelli - blog
 Saint's Log
Saint's Log
 Seravo
Seravo
 TSDgeos' blog
TSDgeos' blog
 Tarin Gamberini
Tarin Gamberini
 Technology – Intuitionistically Uncertain
Technology – Intuitionistically Uncertain
 The Girl Who Wasn't There » English
The Girl Who Wasn't There » English
 The trunk
The trunk
 Thib's Fellowship Blog » fsfe
Thib's Fellowship Blog » fsfe
 Thinking out loud » English
Thinking out loud » English
 Thomas Koch - free software
Thomas Koch - free software
 Thomas Løcke Being Incoherent
Thomas Løcke Being Incoherent
 Told to blog - Entries tagged fsfe
Told to blog - Entries tagged fsfe
 Tonnerre Lombard
Tonnerre Lombard
 Torsten's FSFE blog » english
Torsten's FSFE blog » english
 Viktor's notes » English
Viktor's notes » English
 Vitaly Repin. Software engineer's blog
Vitaly Repin. Software engineer's blog
 Weblog
Weblog
 Weblog
Weblog
 Weblog
Weblog
 Weblog
Weblog
 Weblog
Weblog
 Weblog
Weblog
 Werner's own blurbs
Werner's own blurbs
 With/in the FSFE » English
With/in the FSFE » English
 a fellowship ahead
a fellowship ahead
 agger's Free Software blog
agger's Free Software blog
 anna.morris's blog
anna.morris's blog
 ayers's blog
ayers's blog
 bb's blog
bb's blog
 blog
blog
 drdanzs blog » freesoftware
drdanzs blog » freesoftware
 egnun's blog » FreeSoftware
egnun's blog » FreeSoftware
 free software - Bits of Freedom
free software - Bits of Freedom
 free software blog
free software blog
 freedom bits
freedom bits
 gollo's blog » English
gollo's blog » English
 julia.e.klein's blog
julia.e.klein's blog
 marc0s on Free Software
marc0s on Free Software
 mkesper's blog » English
mkesper's blog » English
 nikos.roussos - opensource
nikos.roussos - opensource
 pichel's blog
pichel's blog
 polina's blog
polina's blog
 rieper|blog » en
rieper|blog » en
 softmetz' anglophone Free Software blog
softmetz' anglophone Free Software blog
 stargrave's blog
stargrave's blog
 the_unconventional's blog » English
the_unconventional's blog » English
 things i made
things i made
 tobias_platen's blog
tobias_platen's blog
 tolld's blog
tolld's blog
 vanitasvitae's blog » englisch
vanitasvitae's blog » englisch
 wkossen's blog
wkossen's blog
 yahuxo's blog
yahuxo's blog