- published: 08 Jun 2015
- views: 4233171
-
remove the playlistHacking
-
remove the playlistLatest Videos
-
remove the playlistLongest Videos
- remove the playlistHacking
- remove the playlistLatest Videos
- remove the playlistLongest Videos
- published: 15 Feb 2015
- views: 15816252
- published: 17 Dec 2016
- views: 1429030
- published: 27 May 2015
- views: 3165733
- published: 21 Jul 2015
- views: 2074130
- published: 06 May 2017
- views: 625000
- published: 28 Jan 2017
- views: 1130633
- published: 12 Dec 2010
- views: 2844768
- published: 30 Aug 2012
- views: 14984769
- published: 11 May 2016
- views: 4680678
Hacking
Hacking may refer to:
- Hacker (programmer subculture), activity within the computer programmer subculture
- Hacker (computer security), to access computer networks, legally or otherwise
- Computer crime
People with the surname
See also
This article is licensed under the Creative Commons Attribution-ShareAlike 3.0 Unported License, which means that you can copy and modify it as long as the entire work (including additions) remains under this license.

Kali Linux
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security Ltd. Mati Aharoni, Devon Kearns and Raphaël Hertzog are the core developers. It is also not a Linux distribution which is suggested for daily use due to the fact that is designed for professional penetration testers, not users so it is not user-friendly.
Development
Kali Linux is preinstalled with over 600 penetration-testing programs, including Armitage (a graphical cyber attack management tool), nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), Aircrack-ng (a software suite for penetration-testing wireless LANs), Burp suite and OWASP ZAP (both web application security scanners). Kali Linux can run natively when installed on a computer's hard disk, can be booted from a live CD or live USB, or it can run within a virtual machine. It is a supported platform of the Metasploit Project's Metasploit Framework, a tool for developing and executing security exploits.
This article is licensed under the Creative Commons Attribution-ShareAlike 3.0 Unported License, which means that you can copy and modify it as long as the entire work (including additions) remains under this license.
White hat (computer security)
The term "white hat" in Internet slang refers to an ethical computer hacker, or a computer security expert, who specializes in penetration testing and in other testing methodologies to ensure the security of an organization's information systems.Ethical hacking is a term coined by IBM meant to imply a broader category than just penetration testing. White-hat hackers may also work in teams called "sneakers",red teams, or tiger teams.
History
One of the first instances of an ethical hack being used was a "security evaluation" conducted by the United States Air Force of the Multics operating systems for "potential use as a two-level (secret/top secret) system." Their evaluation found that while Multics was "significantly better than other conventional systems," it also had "... vulnerabilities in hardware security, software security and procedural security" that could be uncovered with "a relatively low level of effort." The authors performed their tests under a guideline of realism, so that their results would accurately represent the kinds of access that an intruder could potentially achieve. They performed tests that were simple information-gathering exercises, as well as other tests that were outright attacks upon the system that might damage its integrity. Clearly, their audience wanted to know both results. There are several other now unclassified reports that describe ethical hacking activities within the U.S. military.
This article is licensed under the Creative Commons Attribution-ShareAlike 3.0 Unported License, which means that you can copy and modify it as long as the entire work (including additions) remains under this license.

SQL injection
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
SQL injection attacks allow attackers to spoof identity, tamper with existing data, cause repudiation issues such as voiding transactions or changing balances, allow the complete disclosure of all data on the system, destroy the data or make it otherwise unavailable, and become administrators of the database server.
In a 2012 study, security company Imperva observed that the average web application received 4 attack campaigns per month, and retailers received twice as many attacks as other industries.
This article is licensed under the Creative Commons Attribution-ShareAlike 3.0 Unported License, which means that you can copy and modify it as long as the entire work (including additions) remains under this license.
- Loading...

-
 2:59
2:59Hacking demo(messing with loud neighbors)
Hacking demo(messing with loud neighbors)Hacking demo(messing with loud neighbors)
http://www.facebook.com/JoseIsFunny To use this video in a commercial player or in broadcasts, please email licensing@storyful.com If you didn't see the original here it is: https://www.youtube.com/watch?v=csgrXFCtPqI This is not a how to, but a demo. I'll be hacking into the computers in the back, that are on their own network. if you google the tools below you could certainly figure out how to do this yourself. I did my best to edit out my hashes, and waiting time. Entire hack from beginning to end took about 2 hours. Once inside you have as much control as the owner of the computer. Tools used: Kali Linux *Aircrack-ng suite *Responder.py *Metasploit (Armitage) for brevity and aesthetic purposes *Veil-Evasion *BeEF *Meterpreter (Payload) 'The Complex' Kevin MacLeod (incompetech.com) Licensed under Creative Commons: By Attribution 3.0 http://creativecommons.org/licenses/by/3.0/ This Video is also meant to double as ASMR enjoy. -
 4:32
4:325 Most Dangerous Hackers Of All Time
5 Most Dangerous Hackers Of All Time5 Most Dangerous Hackers Of All Time
Here are 5 of the most dangerous hackers to ever walk the streets of the Internet. Visit our site: http://TopTrending.com Like us on Facebook: https://www.facebook.com/TopTrending Follow us on Twitter: https://twitter.com/TopTrending Commentator: http://www.youtube.com/user/BaerTaffy Music: Hacking the System http://audiojungle.net/item/hacking-the-system/8798270 5 Most Dangerous Hackers Of All Time -
 5:01
5:01How Hackers Really Crack Your Passwords
How Hackers Really Crack Your PasswordsHow Hackers Really Crack Your Passwords
How do computer hackers figure out our passwords? Learn about the techniques they use to crack the codes, and what systems protect us. Building Digital Labyrinths To Hide Your Password - https://youtu.be/KFPkmhcSlo4 Sign Up For The Seeker Newsletter Here - http://bit.ly/1UO1PxI Read More: Here's How to Stop Russian Cyber-Hacking http://www.seeker.com/heres-how-to-stop-russian-cyber-hacking-2149775375.html “In October, malware embedded in residential internet routers and DVRs helped orchestrate a large-scale distributed denial of service (DDOS) attack on the East Coast that shut down Amazon, Netflix, Twitter and other major websites. The following month, a ransomware hack shut down San Francisco's public transit ticketing system for a few days after Thanksgiving.” 7 sneak attacks used by today's most devious hackers http://www.infoworld.com/article/2610239/malware/7-sneak-attacks-used-by-today-s-most-devious-hackers.html “Millions of pieces of malware and thousands of malicious hacker gangs roam today's online world preying on easy dupes. Reusing the same tactics that have worked for years, if not decades, they do nothing new or interesting in exploiting our laziness, lapses in judgment, or plain idiocy.” How Your Passwords Are Stored on the Internet (and When Your Password Strength Doesn't Matter) http://lifehacker.com/5919918/how-your-passwords-are-stored-on-the-internet-and-when-your-password-strength-doesnt-matter “There are a number of ways a site can store your password, and some are considerably more secure than others. Here’s a quick rundown of the most popular methods, and what they mean for the security of your data.” ____________________ DNews is dedicated to satisfying your curiosity and to bringing you mind-bending stories & perspectives you won't find anywhere else! New videos daily. Watch More DNews on Seeker http://www.seeker.com/show/dnews/ Subscribe now! http://www.youtube.com/subscription_center?add_user=dnewschannel Seeker on Twitter http://twitter.com/seeker Trace Dominguez on Twitter https://twitter.com/tracedominguez DNews on Facebook https://facebook.com/DiscoveryNews DNews on Google+ https://plus.google.com/u/0/+dnews Seeker http://www.seeker.com/ Sign Up For The Seeker Newsletter Here: http://bit.ly/1UO1PxI -
 4:51:54
4:51:54Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
Everything you need to get started as a hacker and take your hacking skills to an expert level is included in this free screen capture HD video tutorial course! Begin with the basics of hacking including what is ethical hacking, introduction to hacking terms, and how hackers setup their computers. Follow along as you see exactly what software you need including VirtualBox and Kali Linux. See what to do next after you download VirtualBox, create your virtual environment, and install Kali Linux. Meet the Linux terminal you will use to do your work in including the basic functionalities and Linux Command Line Interface (CLI). See how to navigate in Kali Linux and then get started with the real hacking! Learn Tor, proxychains, Virtual Private Networks (VPN), Macchanger, Nmap, and get an introduction to wifi hacker cracking for WPA and WPA2 security with aircrack and reaver. See a live usage example of aircrack and see how to get all of your questions answered! Take this and 75 more of my courses online free at https://jerrybanfield.com/freecourses/. Help me reach 250,000 subscribers at https://www.youtube.com/c/jerrybanfield?sub_confirmation=1. You get a comprehensive free course here covering all the basics of hacking with exact instructions you can use to take your hacking to an expert level! The best part is you can do all of this in as little as one day! Here is a complete list of what the course includes so you can find your way around it fast. 2:35 Introduction to Ethical Hacking. What is it in detail? 10:39 Basic hacking terms you will want to know getting started. 18:06 Hacking terminology such as white hat, grey hat, and black hat hacking. 30:07 SQL injections, VPN , proxy, VPS, and key loggers. 48:25 How to get your questions about hacking and about this video answered by an expert hacker. 51:20 How to install VirtualBox with rpm plus why use a virtual machine. 1:00:18 Installing VirtualBox using the default package manager from repositories. 1:15:20 Creating the virtual environment. 1:28:55 Installing VirtualBox in a Windows 8.1 environment. 1:34:11 How to install Kali Linux within a virtual environment. 1:50:16 Kali Linux installation after it is running and getting starting using it. 2:02:36 Installing VirtualBox Guest Additions. 2:17:16 Introduction to the Linux terminal. 2:26:51 Linux Command-Line Interface (CLI) basics. 2:40:55 The Linux CLI explained in greater detail to give you a good understanding. 2:56:22 How to get full access to the 17+ hour HD video course including advanced tutorials. 2:58:41 What is Tor? How can you use it to protect your anonymity online? 3:09:39 ProxyChains for using proxy servers, hiding your ip, and obtaining access. 3:21:41 What is a Virtual Private Network (VPN) and how you can stay anonymous with VPN? 3:27:49 What is a macchanger? How can you use it to change your mac address? 3:40:12 Footprinting with Nmap and external resources. 3:57:50 Attacking wireless networks. Overview of the tools. Intro to wifi hacker cracking WPA⁄WPA2. 4:13:04 Aircrack and reaver installation. 4:25:48 Installing aircrack-ng on Windows + crunch on Linux. 4:38:20 Breaking WPA/WPA2 encryption. Wifi hacking and wifi hacker training. 4:49:25 Thank you for watching and how to get more! Get access to the full course which is loaded with tips for successful hacking in over 25 hours of HD video at https://jerrybanfield.com/product/hacking/. Subscribe on YouTube at http://jerry.tips/1CdZJw7 and get more on my website at http://jerrybanfield.com/. My Facebook page is https://www.facebook.com/jbanfield and my Twitter profile is https://twitter.com/jerrybanfield/. -
 5:07
5:07Hackers Remotely Kill a Jeep on the Highway—With Me in It
Hackers Remotely Kill a Jeep on the Highway—With Me in ItHackers Remotely Kill a Jeep on the Highway—With Me in It
Two hackers have developed a tool that can hijack a Jeep over the internet. WIRED senior writer Andy Greenberg takes the SUV for a spin on the highway while the hackers attack it from miles away. Still haven’t subscribed to WIRED on YouTube? ►► http://wrd.cm/15fP7B7 CONNECT WITH WIRED Web: http://wired.com Twitter: https://twitter.com/WIRED Facebook: https://facebook.com/WIRED Pinterest: https://pinterest.com/wired Google+: https://plus.google.com/+WIRED Instagram: http://instagram.com/WIRED Tumblr: http://WIRED.tumblr.com Want even more? Subscribe to The Scene: http://bit.ly/subthescene ABOUT WIRED WIRED is where tomorrow is realized. Through thought-provoking stories and videos, WIRED explores the future of business, innovation, and culture. Hackers Remotely Kill a Jeep on the Highway—With Me in It Executive Producer: Editor in Chief - Scott Dadich Consulting Producer: Creative Director - Billy Sorrentino and Editorial Director - Robert Capps Producer: Senior Producer - Sean Patrick Farrell Post Supervisor: Nurie Mohamed -
 6:20
6:20Start Hacking With Android | Best Hacking App | Hindi - White Hat
Start Hacking With Android | Best Hacking App | Hindi - White HatStart Hacking With Android | Best Hacking App | Hindi - White Hat
(For Beginners) Quick Hack Hacking Course: http://imojo.in/681ivb (Take This after Quick Hack) Tech Master Hacking Course: http://imojo.in/9srl0c Buy Hacking Courses With Paytm: http://technicalsagar.in/paytm/ Namaskar Dosto !!! Is video me main aapko bataunga aapko ek aisi app ke bare me jis se aap apne android phone se he hacking start kar sakte ho. Mere paas aksar yahi sawal aata hai ki kali linux ko android me kaise run karna hai kya bina root kiye kali linux ko run kar sakte hai android me. un sabhi logo ke liye ye video bohut special hone wali hai. aasha karta hu aapko ye video pasand ayegi. Is video ko like kare aur apne dosto ke sath share kare aur agar aap naye hai is channel par to subscribe kare sath he bell icon ko bhi press kare taaki aap humari aane wali video sabse pehle dekh paye. Clash of Clans Hack Ho Sakta Hai ? : https://youtu.be/PVSZc2oNCBw Hack Wifi: https://www.youtube.com/watch?v=9LYeVCL1oCw Hacking Playlist: https://youtu.be/9LYeVCL1oCw?list=PL-5gYa7CLd4hUktJHMpPeyMUz5Q_RgV3t Subscribe to my channel for more videos like this and to support my efforts. Thanks and Love #TechnicalSagar LIKE | COMMENT | SHARE | SUBSCRIBE ---------------------------------------------------------------------------------- For all updates : LIKE My Facebook Page https://www.facebook.com/technicalsagarindia Follow Me on Twitter : http://www.twitter.com/iamasagar Follow Abhishek Sagar on Instagram: theabhisheksagar -
 15:55:20
15:55:20The Complete Ethical Hacking Course: Beginner to Advanced!
The Complete Ethical Hacking Course: Beginner to Advanced!The Complete Ethical Hacking Course: Beginner to Advanced!
Get the complete hacking bundle! http://josephdelgadillo.com/product/hacking-bundle-2017/ Enroll in the FREE teachable course! https://goo.gl/em1Dg9 Enroll in the 4 courses directly on Udemy! The Complete Ethical Hacking Course for 2017! http://bit.ly/2jFrv3e Certified Ethical Hacker Boot Camp for 2017! http://bit.ly/2iZvhDS The Complete Ethical Hacker Course: Beginner to Advanced! http://bit.ly/2klAkkc Build an Advanced Keylogger for Ethical Hacking! http://bit.ly/2jqfTOE If you want to get started hacking you will LOVE The Complete Ethical Hacking Course: Beginner to Advanced! This complete course as seen on Udemy http://bit.ly/2klAkkc, and will take you from beginner to expert hacker. We will begin with the very basics showing you how to setup your environment, and move on to password cracking, WiFi hacking, Dos attacks, SQL injections, and much more! Enroll in The Complete Hacking Course Bundle for 2017! http://josephdelgadillo.com/product/hacking-bundle-2017/ Time Stamps 01:01 Introduction to ethical hacking 09:02 Prerequisites for this course 16:31 Basic terminology: white hat, gray hat, black hat 28:31 Basic terminology: SQL injections, VPN, proxy, VPS, and keyloggers 46:49 VirtualBox installation 55:48 VirtualBox installation through the repositories 1:10:50 Creating a virtual environment 1:24:25 Installing VirtualBox on Windows 1:29:41 Kali Linux installation/setup 1:57:59 VirtualBox Guest Additions installation 2:12:39 Linux terminal basics 2:22:11 Linux command line interface basics 2:51:41 Tor browser setup 3:17:46 Proxychains 3:57:21 Virtual private network 4:15:50 Changing your mac address with macchanger 4:39:07 Footprinting with network mapper (nmap) and external resources 5:26:19 Attacking wireless networks cracking WPA/WPA2 5:41:33 Aircrack-ng & reaver installation 5:54:17 Installing aircrack-ng on Windows & Crunch on Linux 6:05:52 Aricrack-ng & crunch hacking example 6:48:03 Cracking WPS pins with reaver pt.1 7:03:27 Cracking WPS pins with reaver pt.2 7:14:09 Cracking WPS pins with reaver pt.3 7:30:34 Performing denial of service attacks on wireless networks pt.1 7:43:48 Performing denial of service attacks on wireless networks pt.2 8:01:44 SSL strip pt.1 8:10:33 SSL strip pt.2 8:21:11 SSL strip pt.3 8:39:24 Funny things pt.1 8:46:28 Funny things pt.2 8:58:40 Funny things pt.3 9:17:02 Evil twin pt.1 9:27:37 Evil twin pt.2 9:35:05 Evil twin pt.3 9:46:24 Using known vulnerabilities pt.1 9:56:04 Using know vulnerabilities pt.2 10:05:25 Using known vulnerabilities pt.3 10:24:20 Post authentication exploitation (DNS) pt.1 10:33:58 Post authentication exploitation (DNS) pt.2 10:46:20 Post authentication exploitation (DNS) pt.3 11:00:01 SQL injection pt.1 11:12:34 SQL injection pt.2 11:27:20 SQL injection pt.3 11:40:42 SQL injection pt.4 11:52:06 SQL injection pt.5 12:09:02 Brute force methods for cracking passwords – cracking hashes 12:21:06 Cracking linux passwords with john the ripper pt.1 12:33:51 Cracking linux passwords with john the ripper pt.2 12:42:41 Cracking windows passwords with john the ripper 13:02:06 Hydra usage pt.1 13:19:20 Hydra usage pt.2 13:37:41 DoS attack pt.1 introduction to denial of service attacks 13:56:18 DoS attack pt.2 combine slowloris.pl with nmap 14:04:38 DoS attack pt.3 featuring hackers.org 14:14:24 Intro to metasploit and reverse shells 14:32:52 Metasploit starting from a two terminal setup 14:51:16 Making reverse shells persistent on another system and escalating privileges 15:07:51 Creating a persistent shell with metasploit 15:18:48 Using netcat to make any kind of connection you may need 15:38:49 How to upload a reverse shell onto a web server -
 1:09:40
1:09:40Introduction to Hacking
Introduction to HackingIntroduction to Hacking
Attend Question/ Answer MEETUP: http://goo.gl/kPHGFw Schedule a Skype Meeting with Eli: https://silicondiscourse.com Info Level: Beginner Presenter: Eli the Computer Guy Date Created: November 3, 2010 Length of Class: 68 Minutes Tracks Hacking Prerequisites None Purpose of Class This class gives an overview of what hacking is and what hackers do. Topics Covered What is Hacking and Who are Hackers Legal Questions for "Ethical Hackers" Planning an Attack Ways to Attack Protecting Yourself from Discovery Class Notes What is Hacking and Who are Hackers Hacking is Non Convenenal Ways of Interacting with Systems Hats -- Black is Bad, White is Good, Grey Depends on Who You Ask "Ethical Hacking" -- is more a marketing term then anything else. Reasons Acquire Data Impersonation Destruction Fun Fog of Law Corporate Privacy Policy Who owns the SYSTEM is not the same as who owns the DATA Beware of HIPPA and other Privacy Laws Ways to Attack Physical Physically Enter a Building for Theft or to Open a Breach Gaining Entry to a Building Posing as Computer Tech/ Security Be a Temp Employee Hack systems internally Leave a Device to Allow Hacking into Network Planning Attacks What do you want? Mass Attack is where you go after as many systems as possible. Semi Targeted attacks mean you go after a group of targets. Such as you attack companies that use a specific program. Targeted attacks mean you single out a single company for attack Protecting Yourself You can be tracked, but it's not usually worth their time Hack from an Internet Connection that is unattached to you. Leave no trace on your system -- Temp and Log files will document your activities Use compromised systems for attacks Use prepaid credit cards/ phones for transactions and communication RUN and deny everything if found out Criminal Justice Funnel -- Approx. 2% of Criminals Caught Receive any kind of punishment -
 17:50
17:50Top hacker shows us how it's done | Pablos Holman | TEDxMidwest
Top hacker shows us how it's done | Pablos Holman | TEDxMidwestTop hacker shows us how it's done | Pablos Holman | TEDxMidwest
Never miss a talk! SUBSCRIBE to the TEDx channel: http://bit.ly/1FAg8hB You think your wireless and other technology is safe? From Blue Tooth to automobile remotes, PCs, and "secure" credit cards, Hacker extraordinaire shows how nearly every secure system is vulnerable. In the spirit of ideas worth spreading, TEDx is a program of local, self-organized events that bring people together to share a TED-like experience. At a TEDx event, TEDTalks video and live speakers combine to spark deep discussion and connection in a small group. These local, self-organized events are branded TEDx, where x = independently organized TED event. The TED Conference provides general guidance for the TEDx program, but individual TEDx events are self-organized.* (*Subject to certain rules and regulations) -
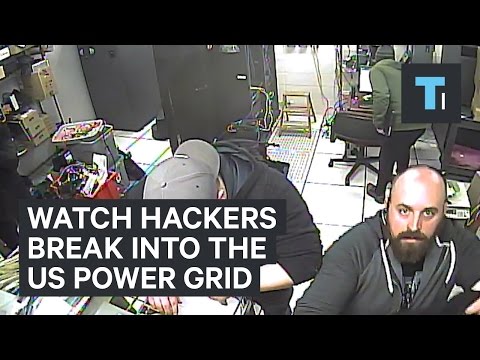 15:51
15:51Watch hackers break into the US power grid
Watch hackers break into the US power gridWatch hackers break into the US power grid
A power company in the Midwest hired a group of white hat hackers known as RedTeam Security to test its defenses. We followed them around for 3 days, as they attempted to break into buildings and hack into its network, with the goal of gaining full access. And it was all much easier than you might think. Based on our experiences, it would seem that power companies need to step up their game in the fight against cyber attackers or it could be "lights out." Produced by Chris Snyder and Paul Szoldra Read more: http://www.techinsider.io/ FACEBOOK: https://www.facebook.com/techinsider TWITTER: https://twitter.com/techinsider INSTAGRAM: https://instagram.com/tech_insider/ TUMBLR: http://techinsider.tumblr.com/
-

Hacking demo(messing with loud neighbors)
http://www.facebook.com/JoseIsFunny To use this video in a commercial player or in broadcasts, please email licensing@storyful.com If you didn't see the original here it is: https://www.youtube.com/watch?v=csgrXFCtPqI This is not a how to, but a demo. I'll be hacking into the computers in the back, that are on their own network. if you google the tools below you could certainly figure out how to do this yourself. I did my best to edit out my hashes, and waiting time. Entire hack from beginning to end took about 2 hours. Once inside you have as much control as the owner of the computer. Tools used: Kali Linux *Aircrack-ng suite *Responder.py *Metasploit (Armitage) for brevity and aesthetic purposes *Veil-Evasion *BeEF *Meterpreter (Payload) 'The Complex' Kevin MacLeod (incompetech.com...
published: 08 Jun 2015 -

5 Most Dangerous Hackers Of All Time
Here are 5 of the most dangerous hackers to ever walk the streets of the Internet. Visit our site: http://TopTrending.com Like us on Facebook: https://www.facebook.com/TopTrending Follow us on Twitter: https://twitter.com/TopTrending Commentator: http://www.youtube.com/user/BaerTaffy Music: Hacking the System http://audiojungle.net/item/hacking-the-system/8798270 5 Most Dangerous Hackers Of All Time
published: 15 Feb 2015 -

How Hackers Really Crack Your Passwords
How do computer hackers figure out our passwords? Learn about the techniques they use to crack the codes, and what systems protect us. Building Digital Labyrinths To Hide Your Password - https://youtu.be/KFPkmhcSlo4 Sign Up For The Seeker Newsletter Here - http://bit.ly/1UO1PxI Read More: Here's How to Stop Russian Cyber-Hacking http://www.seeker.com/heres-how-to-stop-russian-cyber-hacking-2149775375.html “In October, malware embedded in residential internet routers and DVRs helped orchestrate a large-scale distributed denial of service (DDOS) attack on the East Coast that shut down Amazon, Netflix, Twitter and other major websites. The following month, a ransomware hack shut down San Francisco's public transit ticketing system for a few days after Thanksgiving.” 7 sneak ...
published: 17 Dec 2016 -

Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
Everything you need to get started as a hacker and take your hacking skills to an expert level is included in this free screen capture HD video tutorial course! Begin with the basics of hacking including what is ethical hacking, introduction to hacking terms, and how hackers setup their computers. Follow along as you see exactly what software you need including VirtualBox and Kali Linux. See what to do next after you download VirtualBox, create your virtual environment, and install Kali Linux. Meet the Linux terminal you will use to do your work in including the basic functionalities and Linux Command Line Interface (CLI). See how to navigate in Kali Linux and then get started with the real hacking! Learn Tor, proxychains, Virtual Private Networks (VPN), Macchanger, Nmap, and get an introd...
published: 27 May 2015 -

Hackers Remotely Kill a Jeep on the Highway—With Me in It
Two hackers have developed a tool that can hijack a Jeep over the internet. WIRED senior writer Andy Greenberg takes the SUV for a spin on the highway while the hackers attack it from miles away. Still haven’t subscribed to WIRED on YouTube? ►► http://wrd.cm/15fP7B7 CONNECT WITH WIRED Web: http://wired.com Twitter: https://twitter.com/WIRED Facebook: https://facebook.com/WIRED Pinterest: https://pinterest.com/wired Google+: https://plus.google.com/+WIRED Instagram: http://instagram.com/WIRED Tumblr: http://WIRED.tumblr.com Want even more? Subscribe to The Scene: http://bit.ly/subthescene ABOUT WIRED WIRED is where tomorrow is realized. Through thought-provoking stories and videos, WIRED explores the future of business, innovation, and culture. Hackers Remotely ...
published: 21 Jul 2015 -

Start Hacking With Android | Best Hacking App | Hindi - White Hat
(For Beginners) Quick Hack Hacking Course: http://imojo.in/681ivb (Take This after Quick Hack) Tech Master Hacking Course: http://imojo.in/9srl0c Buy Hacking Courses With Paytm: http://technicalsagar.in/paytm/ Namaskar Dosto !!! Is video me main aapko bataunga aapko ek aisi app ke bare me jis se aap apne android phone se he hacking start kar sakte ho. Mere paas aksar yahi sawal aata hai ki kali linux ko android me kaise run karna hai kya bina root kiye kali linux ko run kar sakte hai android me. un sabhi logo ke liye ye video bohut special hone wali hai. aasha karta hu aapko ye video pasand ayegi. Is video ko like kare aur apne dosto ke sath share kare aur agar aap naye hai is channel par to subscribe kare sath he bell icon ko bhi press kare taaki aap humari aane wali video sabse pehl...
published: 06 May 2017 -

The Complete Ethical Hacking Course: Beginner to Advanced!
Get the complete hacking bundle! http://josephdelgadillo.com/product/hacking-bundle-2017/ Enroll in the FREE teachable course! https://goo.gl/em1Dg9 Enroll in the 4 courses directly on Udemy! The Complete Ethical Hacking Course for 2017! http://bit.ly/2jFrv3e Certified Ethical Hacker Boot Camp for 2017! http://bit.ly/2iZvhDS The Complete Ethical Hacker Course: Beginner to Advanced! http://bit.ly/2klAkkc Build an Advanced Keylogger for Ethical Hacking! http://bit.ly/2jqfTOE If you want to get started hacking you will LOVE The Complete Ethical Hacking Course: Beginner to Advanced! This complete course as seen on Udemy http://bit.ly/2klAkkc, and will take you from beginner to expert hacker. We will begin with the very basics showing you how to setup your environment, and move on to passwor...
published: 28 Jan 2017 -

Introduction to Hacking
Attend Question/ Answer MEETUP: http://goo.gl/kPHGFw Schedule a Skype Meeting with Eli: https://silicondiscourse.com Info Level: Beginner Presenter: Eli the Computer Guy Date Created: November 3, 2010 Length of Class: 68 Minutes Tracks Hacking Prerequisites None Purpose of Class This class gives an overview of what hacking is and what hackers do. Topics Covered What is Hacking and Who are Hackers Legal Questions for "Ethical Hackers" Planning an Attack Ways to Attack Protecting Yourself from Discovery Class Notes What is Hacking and Who are Hackers Hacking is Non Convenenal Ways of Interacting with Systems Hats -- Black is Bad, White is Good, Grey Depends on Who You Ask "Ethical Hacking" -- is more a marketing term then anything else. Reasons Acquire Data Impersonation Destruction ...
published: 12 Dec 2010 -

Top hacker shows us how it's done | Pablos Holman | TEDxMidwest
Never miss a talk! SUBSCRIBE to the TEDx channel: http://bit.ly/1FAg8hB You think your wireless and other technology is safe? From Blue Tooth to automobile remotes, PCs, and "secure" credit cards, Hacker extraordinaire shows how nearly every secure system is vulnerable. In the spirit of ideas worth spreading, TEDx is a program of local, self-organized events that bring people together to share a TED-like experience. At a TEDx event, TEDTalks video and live speakers combine to spark deep discussion and connection in a small group. These local, self-organized events are branded TEDx, where x = independently organized TED event. The TED Conference provides general guidance for the TEDx program, but individual TEDx events are self-organized.* (*Subject to certain rules and regulations)
published: 30 Aug 2012 -

Watch hackers break into the US power grid
A power company in the Midwest hired a group of white hat hackers known as RedTeam Security to test its defenses. We followed them around for 3 days, as they attempted to break into buildings and hack into its network, with the goal of gaining full access. And it was all much easier than you might think. Based on our experiences, it would seem that power companies need to step up their game in the fight against cyber attackers or it could be "lights out." Produced by Chris Snyder and Paul Szoldra Read more: http://www.techinsider.io/ FACEBOOK: https://www.facebook.com/techinsider TWITTER: https://twitter.com/techinsider INSTAGRAM: https://instagram.com/tech_insider/ TUMBLR: http://techinsider.tumblr.com/
published: 11 May 2016
Hacking demo(messing with loud neighbors)
- Order: Reorder
- Duration: 2:59
- Updated: 08 Jun 2015
- views: 4233171
- published: 08 Jun 2015
- views: 4233171
5 Most Dangerous Hackers Of All Time
- Order: Reorder
- Duration: 4:32
- Updated: 15 Feb 2015
- views: 15816252
- published: 15 Feb 2015
- views: 15816252
How Hackers Really Crack Your Passwords
- Order: Reorder
- Duration: 5:01
- Updated: 17 Dec 2016
- views: 1429030
- published: 17 Dec 2016
- views: 1429030
Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
- Order: Reorder
- Duration: 4:51:54
- Updated: 27 May 2015
- views: 3165733
- published: 27 May 2015
- views: 3165733
Hackers Remotely Kill a Jeep on the Highway—With Me in It
- Order: Reorder
- Duration: 5:07
- Updated: 21 Jul 2015
- views: 2074130
- published: 21 Jul 2015
- views: 2074130
Start Hacking With Android | Best Hacking App | Hindi - White Hat
- Order: Reorder
- Duration: 6:20
- Updated: 06 May 2017
- views: 625000
- published: 06 May 2017
- views: 625000
The Complete Ethical Hacking Course: Beginner to Advanced!
- Order: Reorder
- Duration: 15:55:20
- Updated: 28 Jan 2017
- views: 1130633
- published: 28 Jan 2017
- views: 1130633
Introduction to Hacking
- Order: Reorder
- Duration: 1:09:40
- Updated: 12 Dec 2010
- views: 2844768
- published: 12 Dec 2010
- views: 2844768
Top hacker shows us how it's done | Pablos Holman | TEDxMidwest
- Order: Reorder
- Duration: 17:50
- Updated: 30 Aug 2012
- views: 14984769
- published: 30 Aug 2012
- views: 14984769
Watch hackers break into the US power grid
- Order: Reorder
- Duration: 15:51
- Updated: 11 May 2016
- views: 4680678
- published: 11 May 2016
- views: 4680678
-

Hacking demo(messing with loud neighbors)
http://www.facebook.com/JoseIsFunny To use this video in a commercial player or in broadcasts, please email licensing@storyful.com If you didn't see the original here it is: https://www.youtube.com/watch?v=csgrXFCtPqI This is not a how to, but a demo. I'll be hacking into the computers in the back, that are on their own network. if you google the tools below you could certainly figure out how to do this yourself. I did my best to edit out my hashes, and waiting time. Entire hack from beginning to end took about 2 hours. Once inside you have as much control as the owner of the computer. Tools used: Kali Linux *Aircrack-ng suite *Responder.py *Metasploit (Armitage) for brevity and aesthetic purposes *Veil-Evasion *BeEF *Meterpreter (Payload) 'The Complex' Kevin MacLeod (incompetech.com...
published: 08 Jun 2015 -

5 Most Dangerous Hackers Of All Time
Here are 5 of the most dangerous hackers to ever walk the streets of the Internet. Visit our site: http://TopTrending.com Like us on Facebook: https://www.facebook.com/TopTrending Follow us on Twitter: https://twitter.com/TopTrending Commentator: http://www.youtube.com/user/BaerTaffy Music: Hacking the System http://audiojungle.net/item/hacking-the-system/8798270 5 Most Dangerous Hackers Of All Time
published: 15 Feb 2015 -

How Hackers Really Crack Your Passwords
How do computer hackers figure out our passwords? Learn about the techniques they use to crack the codes, and what systems protect us. Building Digital Labyrinths To Hide Your Password - https://youtu.be/KFPkmhcSlo4 Sign Up For The Seeker Newsletter Here - http://bit.ly/1UO1PxI Read More: Here's How to Stop Russian Cyber-Hacking http://www.seeker.com/heres-how-to-stop-russian-cyber-hacking-2149775375.html “In October, malware embedded in residential internet routers and DVRs helped orchestrate a large-scale distributed denial of service (DDOS) attack on the East Coast that shut down Amazon, Netflix, Twitter and other major websites. The following month, a ransomware hack shut down San Francisco's public transit ticketing system for a few days after Thanksgiving.” 7 sneak ...
published: 17 Dec 2016 -

Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
Everything you need to get started as a hacker and take your hacking skills to an expert level is included in this free screen capture HD video tutorial course! Begin with the basics of hacking including what is ethical hacking, introduction to hacking terms, and how hackers setup their computers. Follow along as you see exactly what software you need including VirtualBox and Kali Linux. See what to do next after you download VirtualBox, create your virtual environment, and install Kali Linux. Meet the Linux terminal you will use to do your work in including the basic functionalities and Linux Command Line Interface (CLI). See how to navigate in Kali Linux and then get started with the real hacking! Learn Tor, proxychains, Virtual Private Networks (VPN), Macchanger, Nmap, and get an introd...
published: 27 May 2015 -

Hackers Remotely Kill a Jeep on the Highway—With Me in It
Two hackers have developed a tool that can hijack a Jeep over the internet. WIRED senior writer Andy Greenberg takes the SUV for a spin on the highway while the hackers attack it from miles away. Still haven’t subscribed to WIRED on YouTube? ►► http://wrd.cm/15fP7B7 CONNECT WITH WIRED Web: http://wired.com Twitter: https://twitter.com/WIRED Facebook: https://facebook.com/WIRED Pinterest: https://pinterest.com/wired Google+: https://plus.google.com/+WIRED Instagram: http://instagram.com/WIRED Tumblr: http://WIRED.tumblr.com Want even more? Subscribe to The Scene: http://bit.ly/subthescene ABOUT WIRED WIRED is where tomorrow is realized. Through thought-provoking stories and videos, WIRED explores the future of business, innovation, and culture. Hackers Remotely ...
published: 21 Jul 2015 -

Start Hacking With Android | Best Hacking App | Hindi - White Hat
(For Beginners) Quick Hack Hacking Course: http://imojo.in/681ivb (Take This after Quick Hack) Tech Master Hacking Course: http://imojo.in/9srl0c Buy Hacking Courses With Paytm: http://technicalsagar.in/paytm/ Namaskar Dosto !!! Is video me main aapko bataunga aapko ek aisi app ke bare me jis se aap apne android phone se he hacking start kar sakte ho. Mere paas aksar yahi sawal aata hai ki kali linux ko android me kaise run karna hai kya bina root kiye kali linux ko run kar sakte hai android me. un sabhi logo ke liye ye video bohut special hone wali hai. aasha karta hu aapko ye video pasand ayegi. Is video ko like kare aur apne dosto ke sath share kare aur agar aap naye hai is channel par to subscribe kare sath he bell icon ko bhi press kare taaki aap humari aane wali video sabse pehl...
published: 06 May 2017 -

The Complete Ethical Hacking Course: Beginner to Advanced!
Get the complete hacking bundle! http://josephdelgadillo.com/product/hacking-bundle-2017/ Enroll in the FREE teachable course! https://goo.gl/em1Dg9 Enroll in the 4 courses directly on Udemy! The Complete Ethical Hacking Course for 2017! http://bit.ly/2jFrv3e Certified Ethical Hacker Boot Camp for 2017! http://bit.ly/2iZvhDS The Complete Ethical Hacker Course: Beginner to Advanced! http://bit.ly/2klAkkc Build an Advanced Keylogger for Ethical Hacking! http://bit.ly/2jqfTOE If you want to get started hacking you will LOVE The Complete Ethical Hacking Course: Beginner to Advanced! This complete course as seen on Udemy http://bit.ly/2klAkkc, and will take you from beginner to expert hacker. We will begin with the very basics showing you how to setup your environment, and move on to passwor...
published: 28 Jan 2017 -

Introduction to Hacking
Attend Question/ Answer MEETUP: http://goo.gl/kPHGFw Schedule a Skype Meeting with Eli: https://silicondiscourse.com Info Level: Beginner Presenter: Eli the Computer Guy Date Created: November 3, 2010 Length of Class: 68 Minutes Tracks Hacking Prerequisites None Purpose of Class This class gives an overview of what hacking is and what hackers do. Topics Covered What is Hacking and Who are Hackers Legal Questions for "Ethical Hackers" Planning an Attack Ways to Attack Protecting Yourself from Discovery Class Notes What is Hacking and Who are Hackers Hacking is Non Convenenal Ways of Interacting with Systems Hats -- Black is Bad, White is Good, Grey Depends on Who You Ask "Ethical Hacking" -- is more a marketing term then anything else. Reasons Acquire Data Impersonation Destruction ...
published: 12 Dec 2010 -

Top hacker shows us how it's done | Pablos Holman | TEDxMidwest
Never miss a talk! SUBSCRIBE to the TEDx channel: http://bit.ly/1FAg8hB You think your wireless and other technology is safe? From Blue Tooth to automobile remotes, PCs, and "secure" credit cards, Hacker extraordinaire shows how nearly every secure system is vulnerable. In the spirit of ideas worth spreading, TEDx is a program of local, self-organized events that bring people together to share a TED-like experience. At a TEDx event, TEDTalks video and live speakers combine to spark deep discussion and connection in a small group. These local, self-organized events are branded TEDx, where x = independently organized TED event. The TED Conference provides general guidance for the TEDx program, but individual TEDx events are self-organized.* (*Subject to certain rules and regulations)
published: 30 Aug 2012 -

Watch hackers break into the US power grid
A power company in the Midwest hired a group of white hat hackers known as RedTeam Security to test its defenses. We followed them around for 3 days, as they attempted to break into buildings and hack into its network, with the goal of gaining full access. And it was all much easier than you might think. Based on our experiences, it would seem that power companies need to step up their game in the fight against cyber attackers or it could be "lights out." Produced by Chris Snyder and Paul Szoldra Read more: http://www.techinsider.io/ FACEBOOK: https://www.facebook.com/techinsider TWITTER: https://twitter.com/techinsider INSTAGRAM: https://instagram.com/tech_insider/ TUMBLR: http://techinsider.tumblr.com/
published: 11 May 2016
Hacking demo(messing with loud neighbors)
- Order: Reorder
- Duration: 2:59
- Updated: 08 Jun 2015
- views: 4233171
- published: 08 Jun 2015
- views: 4233171
5 Most Dangerous Hackers Of All Time
- Order: Reorder
- Duration: 4:32
- Updated: 15 Feb 2015
- views: 15816252
- published: 15 Feb 2015
- views: 15816252
How Hackers Really Crack Your Passwords
- Order: Reorder
- Duration: 5:01
- Updated: 17 Dec 2016
- views: 1429030
- published: 17 Dec 2016
- views: 1429030
Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
- Order: Reorder
- Duration: 4:51:54
- Updated: 27 May 2015
- views: 3165733
- published: 27 May 2015
- views: 3165733
Hackers Remotely Kill a Jeep on the Highway—With Me in It
- Order: Reorder
- Duration: 5:07
- Updated: 21 Jul 2015
- views: 2074130
- published: 21 Jul 2015
- views: 2074130
Start Hacking With Android | Best Hacking App | Hindi - White Hat
- Order: Reorder
- Duration: 6:20
- Updated: 06 May 2017
- views: 625000
- published: 06 May 2017
- views: 625000
The Complete Ethical Hacking Course: Beginner to Advanced!
- Order: Reorder
- Duration: 15:55:20
- Updated: 28 Jan 2017
- views: 1130633
- published: 28 Jan 2017
- views: 1130633
Introduction to Hacking
- Order: Reorder
- Duration: 1:09:40
- Updated: 12 Dec 2010
- views: 2844768
- published: 12 Dec 2010
- views: 2844768
Top hacker shows us how it's done | Pablos Holman | TEDxMidwest
- Order: Reorder
- Duration: 17:50
- Updated: 30 Aug 2012
- views: 14984769
- published: 30 Aug 2012
- views: 14984769
Watch hackers break into the US power grid
- Order: Reorder
- Duration: 15:51
- Updated: 11 May 2016
- views: 4680678
- published: 11 May 2016
- views: 4680678
-

The Russian Hacking Myth Just Got Obliterated!
On June 12 last year, Julian Assange announced that WikiLeaks had and would publish documents pertinent to Hillary Clinton’s presidential campaign. On June 14, CrowdStrike, a cyber-security firm hired by the DNC, announced, without providing evidence, that it had found malware on DNC servers and had evidence that Russians were responsible for planting it. On June 15, Guccifer 2.0 first appeared, took responsibility for the “hack” reported on June 14 and claimed to be a WikiLeaks source. It then posted the adulterated documents just described. On July 5, Guccifer again claimed he had remotely hacked DNC servers, and the operation was instantly described as another intrusion attributable to Russia. Virtually no media questioned this account. The Nation: https://www.thenation.com/article/a-n...
published: 10 Aug 2017 -

Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
Everything you need to get started as a hacker and take your hacking skills to an expert level is included in this free screen capture HD video tutorial course! Begin with the basics of hacking including what is ethical hacking, introduction to hacking terms, and how hackers setup their computers. Follow along as you see exactly what software you need including VirtualBox and Kali Linux. See what to do next after you download VirtualBox, create your virtual environment, and install Kali Linux. Meet the Linux terminal you will use to do your work in including the basic functionalities and Linux Command Line Interface (CLI). See how to navigate in Kali Linux and then get started with the real hacking! Learn Tor, proxychains, Virtual Private Networks (VPN), Macchanger, Nmap, and get an introd...
published: 27 May 2015 -

The Complete Ethical Hacking Course: Beginner to Advanced!
Get the complete hacking bundle! http://josephdelgadillo.com/product/hacking-bundle-2017/ Enroll in the FREE teachable course! https://goo.gl/em1Dg9 Enroll in the 4 courses directly on Udemy! The Complete Ethical Hacking Course for 2017! http://bit.ly/2jFrv3e Certified Ethical Hacker Boot Camp for 2017! http://bit.ly/2iZvhDS The Complete Ethical Hacker Course: Beginner to Advanced! http://bit.ly/2klAkkc Build an Advanced Keylogger for Ethical Hacking! http://bit.ly/2jqfTOE If you want to get started hacking you will LOVE The Complete Ethical Hacking Course: Beginner to Advanced! This complete course as seen on Udemy http://bit.ly/2klAkkc, and will take you from beginner to expert hacker. We will begin with the very basics showing you how to setup your environment, and move on to passwor...
published: 28 Jan 2017 -

Introduction to Hacking
Attend Question/ Answer MEETUP: http://goo.gl/kPHGFw Schedule a Skype Meeting with Eli: https://silicondiscourse.com Info Level: Beginner Presenter: Eli the Computer Guy Date Created: November 3, 2010 Length of Class: 68 Minutes Tracks Hacking Prerequisites None Purpose of Class This class gives an overview of what hacking is and what hackers do. Topics Covered What is Hacking and Who are Hackers Legal Questions for "Ethical Hackers" Planning an Attack Ways to Attack Protecting Yourself from Discovery Class Notes What is Hacking and Who are Hackers Hacking is Non Convenenal Ways of Interacting with Systems Hats -- Black is Bad, White is Good, Grey Depends on Who You Ask "Ethical Hacking" -- is more a marketing term then anything else. Reasons Acquire Data Impersonation Destruction ...
published: 12 Dec 2010 -

Horrifying Deep Web Stories "Why I Quit Hacking.." (Graphic) A Scary Hacker Story
WARNING, GRAPHIC CONTENT AND LANGUAGE. YOU HAVE BEEN WARNED. The Deep Web / Dark Web is a very real and scary place.. Let me know what you guys thought of this one, if you enjoyed this video please "like" or comment that you want more like this so I know! If you have any stories to get POSSIBLY read by me on my channel, art, or general nice things you want to say to me my email is Corpsehusbandstories@gmail.com ► Merch and T-Shirts: http://shop.spreadshirt.com/Corpsey ► Snapchat, Twitter, and Instagram: Corpse_Husband ► Music credit to : Kevin MacLeod (incompetech.com) Licensed under Creative Commons: By Attribution 3.0 ► And "Myuuji" found here https://www.youtube.com/user/myuuji ►Outro music credit to: https://www.youtube.com/user/naraklash ►Outro video credit: https://www.youtube...
published: 28 Oct 2015 -

Minecraft: SHE IS HACKING THE SERVER!! SO FREAKING LUCKY!! PokeFind EP: 05
Thank you guys for all of the support, you are the best!! ► New Merch - http://bit.ly/2vF2sV4 ► PokeFind Playlist: https://www.youtube.com/playlist?list=PLgeJxxybW8ZtgvKT57S3Ts66Hgl9plnYD ► Server IP - play.pokefind.co ----------------------------------------------------------- ► Subscribe to us: http://bit.ly/Sub2TheaAndCrainer ----------------------------------------------------------- ► Thea's Social Media: • Instagram: http://instagram.com/theanicka • Twitter: http://www.twitter.com/thea_nicka ----------------------------------------------------------- ► Crainer's Social Media: • Instagram: http://instagram.com/mrcrainer • Twitter: http://www.twitter.com/mrcrainer • Facebook: http://bit.ly/CrainerFacebook ----------------------------------------------------------- ► Intro Music by JFA...
published: 08 Aug 2017 -

-

HACKING THECAMPINGRUSHER! TROLLING PLAYERS (Minecraft Trolling)
Hacking TheCampingRusher and trolling players on TheArchon and Hypixel! We also make TheCampingRusher millions... pvp.thearchon.net www.youtube.com/TheCampingRusher Follow my Twitter :D - www.twitter.com/Curtis3321 Here we Troll users in Minecraft, I currently am on the Minecraft account TheCampingRusher. TheCampingRusher is a YouTuber who plays on the Minecraft Faction server TheArchon. The Minecraft Faction server has many awesome gamemodes such as regular Factions, Custom Enchantment Factions and much more. We also login to Hypixel with the YouTuber rank (YT Rank Hypixel).
published: 10 Aug 2017 -

HACKING ARCADE MACHINES
YESTERDAYS EPISODE: https://www.youtube.com/watch?v=6YAcvDDiDRQ SUBSCRIBE: https://www.youtube.com/adventureswithdan MAIN CHANNEL: https://www.youtube.com/user/ItsDanHill *MAKE SURE TO TURN ON MY POST NOTIFICATIONS SO YOU NEVER MISS WHEN I POST A VIDEO!* Follow me: YouNow: http://younow.com/imdanhill Twitter: http://Twitter.com/DanRelates Instagram: http://Instagram.com/DanRelates Snapchat: WeeklyDan Musical.ly: Dan_Hill Make sure to LIKE and SUBSCRIBE if you enjoyed this video (:
published: 21 Nov 2016 -

Hacking Tutorial #001 deutsch - Grundlagen
Heute gibt es von mir eine neue Tutorial Reihe zum Thema "Hacking". Im ersten Video dazu beschäftigen wir uns mit den Grundlagen zu diesem Thema. Praxisvideos folgen! Bitte entschuldigt die Sound-Qualität. Ich bin leider noch nicht dazu gekommen mir ein neues Mic anzuschaffen. ;)
published: 11 Mar 2016
The Russian Hacking Myth Just Got Obliterated!
- Order: Reorder
- Duration: 39:31
- Updated: 10 Aug 2017
- views: 1414
- published: 10 Aug 2017
- views: 1414
Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
- Order: Reorder
- Duration: 4:51:54
- Updated: 27 May 2015
- views: 3165733
- published: 27 May 2015
- views: 3165733
The Complete Ethical Hacking Course: Beginner to Advanced!
- Order: Reorder
- Duration: 15:55:20
- Updated: 28 Jan 2017
- views: 1130633
- published: 28 Jan 2017
- views: 1130633
Introduction to Hacking
- Order: Reorder
- Duration: 1:09:40
- Updated: 12 Dec 2010
- views: 2844768
- published: 12 Dec 2010
- views: 2844768
Horrifying Deep Web Stories "Why I Quit Hacking.." (Graphic) A Scary Hacker Story
- Order: Reorder
- Duration: 27:06
- Updated: 28 Oct 2015
- views: 7881046
- published: 28 Oct 2015
- views: 7881046
Minecraft: SHE IS HACKING THE SERVER!! SO FREAKING LUCKY!! PokeFind EP: 05
- Order: Reorder
- Duration: 32:55
- Updated: 08 Aug 2017
- views: 20296
- published: 08 Aug 2017
- views: 20296
Untraceable Hacking Full HD Movie By -Tuner Himu
- Order: Reorder
- Duration: 1:37:01
- Updated: 13 Jul 2015
- views: 391570
HACKING THECAMPINGRUSHER! TROLLING PLAYERS (Minecraft Trolling)
- Order: Reorder
- Duration: 24:16
- Updated: 10 Aug 2017
- views: 863
- published: 10 Aug 2017
- views: 863
HACKING ARCADE MACHINES
- Order: Reorder
- Duration: 22:29
- Updated: 21 Nov 2016
- views: 612031
- published: 21 Nov 2016
- views: 612031
Hacking Tutorial #001 deutsch - Grundlagen
- Order: Reorder
- Duration: 40:17
- Updated: 11 Mar 2016
- views: 27064
- published: 11 Mar 2016
- views: 27064


- Playlist
- Chat

Hacking demo(messing with loud neighbors)
- Report rights infringement
- published: 08 Jun 2015
- views: 4233171

5 Most Dangerous Hackers Of All Time
- Report rights infringement
- published: 15 Feb 2015
- views: 15816252

How Hackers Really Crack Your Passwords
- Report rights infringement
- published: 17 Dec 2016
- views: 1429030

Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
- Report rights infringement
- published: 27 May 2015
- views: 3165733

Hackers Remotely Kill a Jeep on the Highway—With Me in It
- Report rights infringement
- published: 21 Jul 2015
- views: 2074130

Start Hacking With Android | Best Hacking App | Hindi - White Hat
- Report rights infringement
- published: 06 May 2017
- views: 625000

The Complete Ethical Hacking Course: Beginner to Advanced!
- Report rights infringement
- published: 28 Jan 2017
- views: 1130633

Introduction to Hacking
- Report rights infringement
- published: 12 Dec 2010
- views: 2844768

Top hacker shows us how it's done | Pablos Holman | TEDxMidwest
- Report rights infringement
- published: 30 Aug 2012
- views: 14984769

Watch hackers break into the US power grid
- Report rights infringement
- published: 11 May 2016
- views: 4680678

- Playlist
- Chat

Hacking demo(messing with loud neighbors)
- Report rights infringement
- published: 08 Jun 2015
- views: 4233171

5 Most Dangerous Hackers Of All Time
- Report rights infringement
- published: 15 Feb 2015
- views: 15816252

How Hackers Really Crack Your Passwords
- Report rights infringement
- published: 17 Dec 2016
- views: 1429030

Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
- Report rights infringement
- published: 27 May 2015
- views: 3165733

Hackers Remotely Kill a Jeep on the Highway—With Me in It
- Report rights infringement
- published: 21 Jul 2015
- views: 2074130

Start Hacking With Android | Best Hacking App | Hindi - White Hat
- Report rights infringement
- published: 06 May 2017
- views: 625000

The Complete Ethical Hacking Course: Beginner to Advanced!
- Report rights infringement
- published: 28 Jan 2017
- views: 1130633

Introduction to Hacking
- Report rights infringement
- published: 12 Dec 2010
- views: 2844768

Top hacker shows us how it's done | Pablos Holman | TEDxMidwest
- Report rights infringement
- published: 30 Aug 2012
- views: 14984769

Watch hackers break into the US power grid
- Report rights infringement
- published: 11 May 2016
- views: 4680678

- Playlist
- Chat

The Russian Hacking Myth Just Got Obliterated!
- Report rights infringement
- published: 10 Aug 2017
- views: 1414

Complete Free Hacking Course: Go from Beginner to Expert Hacker Today!
- Report rights infringement
- published: 27 May 2015
- views: 3165733

The Complete Ethical Hacking Course: Beginner to Advanced!
- Report rights infringement
- published: 28 Jan 2017
- views: 1130633

Introduction to Hacking
- Report rights infringement
- published: 12 Dec 2010
- views: 2844768

Horrifying Deep Web Stories "Why I Quit Hacking.." (Graphic) A Scary Hacker Story
- Report rights infringement
- published: 28 Oct 2015
- views: 7881046

Minecraft: SHE IS HACKING THE SERVER!! SO FREAKING LUCKY!! PokeFind EP: 05
- Report rights infringement
- published: 08 Aug 2017
- views: 20296


HACKING THECAMPINGRUSHER! TROLLING PLAYERS (Minecraft Trolling)
- Report rights infringement
- published: 10 Aug 2017
- views: 863

HACKING ARCADE MACHINES
- Report rights infringement
- published: 21 Nov 2016
- views: 612031

Hacking Tutorial #001 deutsch - Grundlagen
- Report rights infringement
- published: 11 Mar 2016
- views: 27064
-
Lyrics list:lyrics
-
Hawking, Todd Rundgren
-
Hawking, Paul Gilbert
-
Hawking, Quitter
Hawking
Whenever I
I close my eyes
Then I don't mind being the way I am
But whenever I try
Explaining why
I know I never can
Now that it's
Gone, paths I used to travel
Gone, things I used to handle
Gone, once I had a choice what to be
But then god kissed me
And I lost it when I fainted in his arms
Have pity on me brother
I'm trapped behind the mirror
I'm out here on the border
Wondering why
Why was it I?
Maybe my mind wouldn't have come this way
If I'd taken my time
Answers only unwind
When you can't look away
Maybe 'cause
I want the secret broken
I want the casket open
I need to see what no eyes can seeAnd when god kissed me
Then I dreamed them when I fainted in her arms
Now I've got to go on sleeping
Lean in a little closer
And I'll tell you what I'm dreaming
I'll tell you what I'm dreaming
I see time without beginning
Space without an ending
I see bodies strong and running
With minds not comprehending
Have pity on your brother
Please have pity on your sister
Take pity on each other
And on every living creature
Whenever I
Open my eyes
I can't believe it's real
It's a jungle outside
People just survive
They can't reach the high ideal
But I
Know if I can't recover, at least I
Know, I know the book from cover to cover, and who
Knows, I might dream forever
Since I've met the world's greatest lover
When god kissed me
And I knew it when I fainted in his arms
Let's dream together people
Gorakhpur: Encephalitis snuffs out another life today, death toll crosses 70
Edit Yahoo Daily News 13 Aug 2017India deploys more troops along China border, raises ‘caution level’
Edit The Siasat Daily 12 Aug 2017Guam, Japan prepare for possible North Korea missile launch
Edit CNN 13 Aug 2017Usain Bolt collapses in final race, Great Britain seal 4x100m relay gold
Edit Hindustan Times 13 Aug 2017No 'Game of Thrones' in latest HBO hacker leak
Edit Fayetteville Observer 14 Aug 2017Curb Your Enthusiasm new episodes leaked online by hacker
Edit Entertainment Weekly 14 Aug 2017HBO Hackers Leak 'Curb' Episodes
Edit The Hollywood Reporter 14 Aug 2017Cyber attacks on online retailers double in a year as hackers try to steal shoppers' details
Edit The Daily Telegraph 14 Aug 2017Farmer hacked dead by friend
Edit Sun Star 13 Aug 2017Another report: That Russian hack of the DNC probably… wasn’t
Edit Hot Air 13 Aug 2017Pune: Juvenile accused of rape hacked to death by victim's father
Edit Mid Day 13 Aug 2017What the Heck Is Going on With the HBO Game of Thrones Hack?
Edit Gizmodo 13 Aug 2017Iron Blade: Medieval RPG Hack Cheat Tool Generator
Edit Community news 13 Aug 2017Hacking Shadowplay: ‘Guccifer’ Claims ‘Guccifer 2.0’ is US Government Entity
Edit Sputnik 13 Aug 2017Murder, Fake News, And Hacking Concerns Cloud Disputed Kenyan Election
Edit Topix 13 Aug 2017Leaked Files From The HBO Hack Suggest Rhaegar Targaryen Will Appear on Game of Thrones ...
Edit Gizmodo 13 Aug 2017"Game of Thrones" not among episodes in latest HBO hack
Edit CBS News 13 Aug 2017- 1
- 2
- 3
- 4
- 5
- Next page »