In a matter of days, a new form of ransomware known as WannaCrypt (or WannaCry) has crippled thousands of computers and locked up essential services including hospitals in Britain, FedEx in the US and Telefonica in Spain.
Using the long-established strategy of encrypting a computer's contents and then demanding a payment for the decryption key (in this case around $400 worth of Bitcoin), WannaCrypt is notable for the incredible speed with which it has spread and the high profile targets it's hit.
More National News Videos
How to protect yourself from WannaCrypt
WannaCrypt ransomeware has infected hundreds of thousands of computers worldwide, don't let yours become one of them.
Why did this ransomware spread so much faster than others?
Ordinarily ransomware is spread in the same way as other malware: users are asked to click a link in an email or website to unknowingly install the software, or computers are scanned for potential vulnerabilities that the software can use to slip in.
The exploit used by WannaCrypt however is a special case. In January a hacking group calling itself The Shadow Brokers listed for sale a series of tools it claimed to have stolen from the NSA. It was claimed these included "zero day" exploits for Windows, i.e. exploits that the NSA knew about that Microsoft did not. Once these exploits were in the hands of criminals, it was only a matter of time before an attack was developed.
Last month The Shadow Brokers dumped the tools publicly, and among them was the exact exploit that WannaCrypt is now using. Microsoft had apparently been informed of the exploit sometime previously, as it released security updates to combat it in March, but any computer not up to date is potentially at risk.
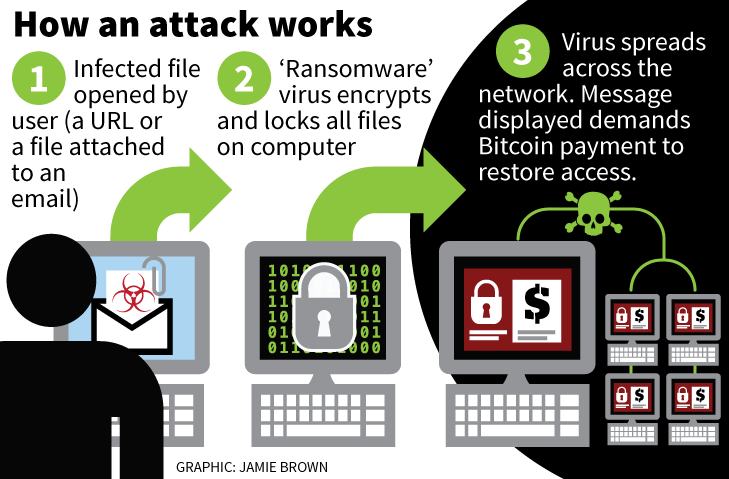
The way WannaCrypt spreads puts businesses at greater risk than individuals, as it uses a protocol called Server Message Block (SMB) which Windows uses to connect machines to file systems over a network. This was seen in practice when the software got into Britain's National Health Service and began to spread to the machines of hospitals and GPs.
Russian railway ops centre Wanna Cry. pic.twitter.com/Xc3eibMOf1
— Kevin Beaumont (@GossiTheDog) May 14, 2017
An early report from Cisco's Talos suggests some affected organisations were not only behind on security updates but were also exposing themselves unnecessarily by having their machines' SMB ports open to the public internet.
How do I make sure my computer is not at risk?
If your computer is running Windows 10, you're safe from this ransomware. The particular vulnerability WannaCrypt targets only exists in older versions of Windows.
If you're running Windows 8.1, Windows 7 or Windows Vista and you have automatic updates enabled, your computer will have downloaded protection against this vulnerability in March. Ditto for enterprise machines running Windows Server 2016, 2012 R2, 2012, 2008 R2 or 2008. If for some reason you have updates turned off, you should find and install this software immediately. The one you're looking for is called MS17-010.
Other Windows operating systems are no longer supported and are, generally speaking, dangerous to run in an online context. Something like Windows XP, for example, has been unsupported for years and has many vulnerabilities for cybercriminals to exploit. In this particular case, Microsoft has made software available that can protect machines using these unsupported systems. If you are running Windows XP, Windows 8 or an older version of Windows Server, you can get the updates here.
Businesses that for whatever reason are unable to install the updates can prevent the software from spreading to their systems by temporarily shutting down all SMB protocols.
Turning off all the SMB1 settings like #wannacry pic.twitter.com/2qHyvLR6tK
— Adam Holthouse (@AdamHolthouse) May 15, 2017
Anything else I should be doing?
In a comprehensive blog post on Wannacrypt, Australian security expert Troy Hunt says the ransomware's unprecedented impact only reinforces what the security community has been advising for years.
Individuals should use the newest operating system they can and just leave Windows Update enabled, in order to get protection against exploits like this, he says.
"The eternal problem is that for individuals, there's often the attitude of 'well it works fine, why should I change it?', and this is enormously dangerous".
The biggest lesson though is for organisations and businesses. Upgrading operating systems and software can be costly and difficult at a large scale, especially when upgrades can conflict with specialised software that organisations rely on.
Yet businesses need to budget for the cost of keeping up to date, and put resources behind making sure they follow industry standard security hygiene practices like restricting access to important files and processes from outside.
"Organisations need to be proactive in monitoring for, testing and rolling out these patches. It's not fun, it costs money and it can still break other dependencies, but the alternative is quite possibly ending up like the NHS or even worse. Bottom line is that it's an essential part of running a desktop environment in a modern business", Hunt says.
And, as always, a comprehensive backup strategy doesn't hurt.


















0 comments
New User? Sign up