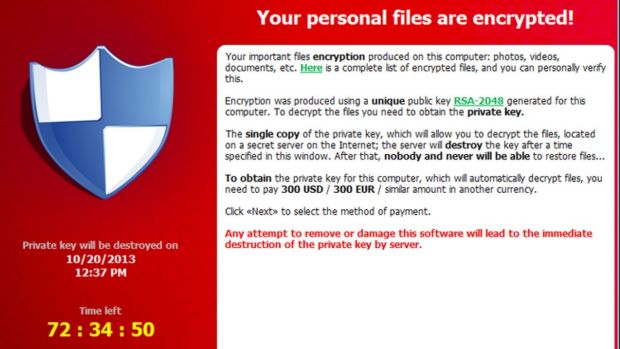
The Cryptolocker software.
Thousands of Australian computers are being locked up by hackers using malicious software that encrypts files and asks for a ransom to make them available again.
Fairfax Media understands Australian government agencies and a number of large enterprises and individuals have been successfully targeted by the scam.
Called "Cryptolocker" and "CryptoWall", the "ransomware" comes in various forms with the CryptoWall version estimated by the government e-safety alert service Stay Smart Online to have infected approximately 20,000 Australian computers.

Accused Russian hacker Evgeniy Mikhailovich Bogachev faces US charges over his suspected development of Cryptolocker. Photo: FBI/AFP
Computers are typically infected after victims click on a malicious link in an email purporting to be from Australia Post or Telstra. Files on their computer and network drives are then encrypted and a ransom demanded within a certain timeframe before a decryption key is supplied to unlock files. If no ransom is paid, the hackers threaten to never allow access to the files.
Cryptolocker was first observed in November. In June it hit Australian computer users via fake Energy Australia emails. Attempts were made to stop it spreading as alleged Russian hacker Evgeniy Mikhailovich Bogachev, 30, was charged as the leader of a criminal ring responsible for the malware and another known as Gameover Zeus.
The US Federal Bureau of Investigation estimated Bogachev made $US100 million from his activities.

The CryptoWall software.
But new variants of the software have popped up since, making it difficult for authorities to stop it and for anti-virus and malware protection software makers to detect it on victim computers.
"We've spoken to at least a dozen or so organisations, many of which already have traditional signature-based [malware detection] technologies of various flavours and vendor solutions ... that didn't detect the virus," said Aaron Bailey, security manager at Australian firm Missing Link Security.
"We believe that each iteration has been modified just enough to escape signature-based [malware] detection, even though the action of the virus is similar and the result is the same."
Mr Bailey said since late May his firm had been contacted by clients requesting assistance due to infections.
"Each [was] delivered via a spearfishing email that poses as a credible Australian company (Energy Australia, Australia Post, Telstra, etc)," he said.
It's been reported some victims have been charged as much as $700 to unlock their files. They were often asked to pay in the virtual currency bitcoin. Even a US police department had to pay a ransom to unlock its files.
In order to help victims, two security firms have collaborated on a service called Decrypt Cryptolocker, which claims to decrypt files for free and has been hailed by Stay Smart Online. But Mr Bailey said the site didn't always work.
"We have seen this [website] work in some cases to be able to decrypt files and not for others," Mr Bailey said.
Stay Smart Online said paying criminals was not the best idea.
"It is important to note that for many victims, paying the ransom may lead to files being returned to normal. However, because you are dealing with criminals, you should be aware this is extortion and there are no guarantees you will regain access to your data."
Mr Bailey said the best advice was to restore from a back-up, if available.
Fairfax has previously reported on other types of ransomware infecting Australians and small businesses. Miami Family Medical Centre, Byron Bay Community School in NSW and Northern Territory business TDC Refrigeration and Electrical were among the victims.
A survey released in March by researchers at the University of Kent found that 41 per cent of British victims decided to pay the Cryptolocker ransom.
Security firm Symantec previously believed 3 per cent paid, while Dell SecureWorks thought only 0.4 per cent had.
CERT Australia, the federal government's computer emergency response team, confirmed to Fairfax that it had been contacted by a number of organisations that have been affected by CryptoLocker. Advice on it website suggests, among other things, that backups be kept.
In order to reduce the attractiveness of the ransomware business model, CERT Australia recommended against payments of any amount.
The Department of Defence would not comment on whether any government agencies were affected. "Discussing these could jeopardise ongoing investigations, monitoring of incidents and our ability to protect information and networks," it said.
Has your computer been infected? How did you recover your files?


















25 comments so far
More comments
New user? Sign up
Make a comment
You are logged in as [Logout]
All information entered below may be published.
Thank you
Your comment has been submitted for approval.
Comments are moderated and are generally published if they are on-topic and not abusive.