Cloud security at AWS is the highest priority. As an AWS customer, you will benefit from a data center and network architecture built to meet the requirements of the most security-sensitive organizations.
An advantage of the AWS cloud is that it allows customers to scale and innovate, while maintaining a secure environment. Customers pay only for the services they use, meaning that you can have the security you need, but without the upfront expenses, and at a lower cost than in an on-premises environment.
Interested in bringing your skills to the cloud? Check out our open Security Careers »

More controls and increased privacy - all at a lower cost

Keep Your Data Safe
The AWS infrastructure puts strong safeguards in place to help protect customer privacy. All data is stored in highly secure AWS data centers.

Meet Compliance Requirements
AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed.

Save Money
Cut costs by using AWS data centers. Maintain the highest standard of security without having to manage your own facility.

Scale Quickly
Security scales with your AWS cloud usage. No matter the size of your business the AWS infrastructure is designed to keep data safe.
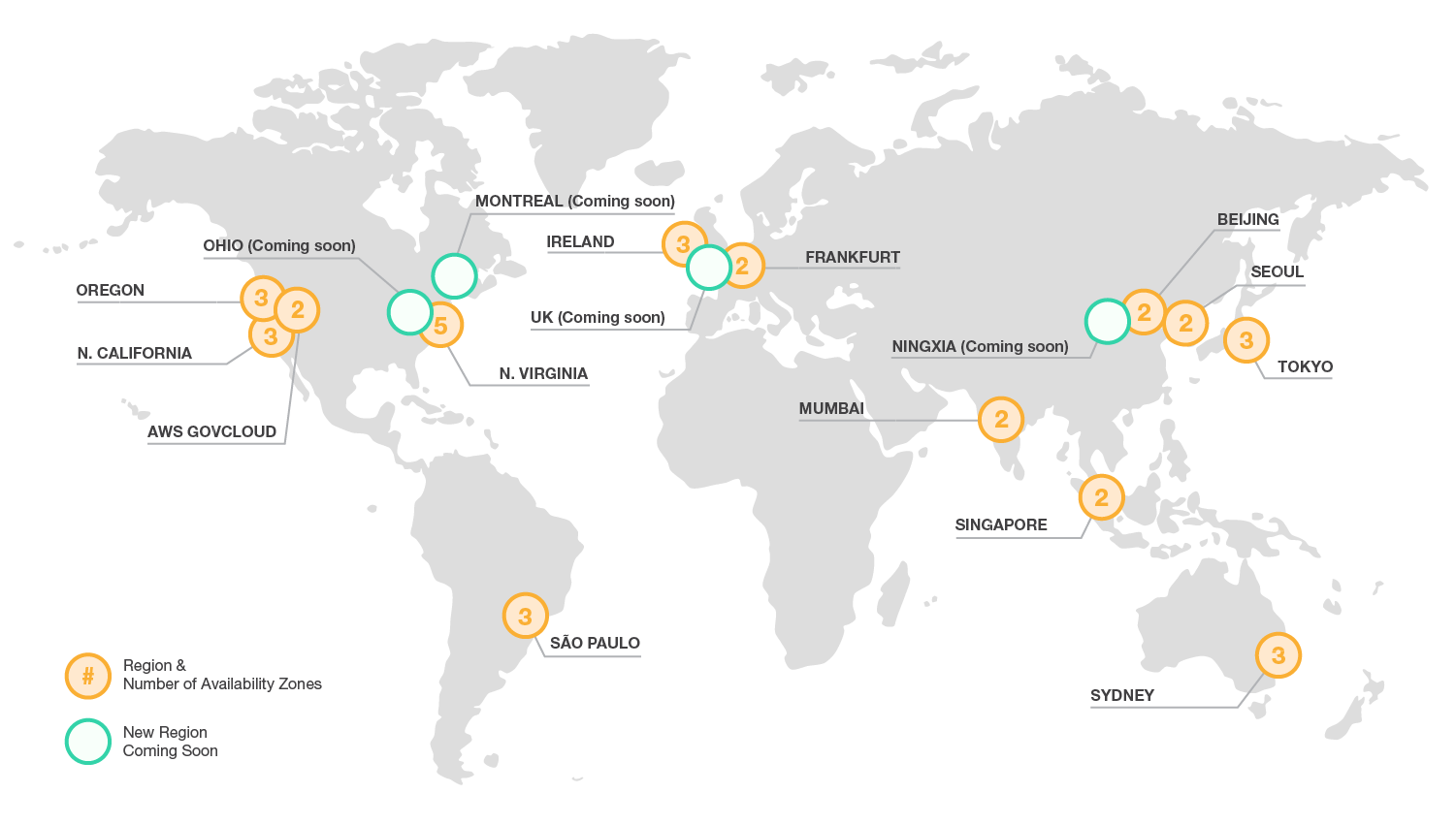
Improving Continuity With Replication Between Regions
Meeting Compliance and Data Residency Requirements
Geographic Expansion
In addition to replicating applications and data across multiple data centers in the same region using Availability Zones, you can also choose to increase redundancy and fault tolerance further by replicating data between geographic regions.
You retain complete control and ownership over the region in which your data is physically located, making it easy to meet regional compliance and data residency requirements.
Throughout the next year, the AWS Global Infrastructure will expand with at least 11 new Availability Zones in new geographic regions: Montreal in Canada, Ningxia in China, Ohio in North America, and the United Kingdom.
Spend less time on compliance and more time running your business
Have the backing of our extensive support network every step of the way
Real-time insight through AWS Trusted Advisor
Proactive support and advocacy with a Technical Account Manager (TAM)
Strategic advice to create In-Depth Security Solutions
Detect and respond to security issues with the Security Operations Playbook
APN Partners offer hundreds of industry-leading products that are equivalent, identical to, or integrate with existing controls in your on-premises environments. These products complement the existing AWS services to enable you to deploy a comprehensive security architecture and a more seamless experience across your cloud and on-premises environments.