- published: 23 Nov 2010
- views: 13419
- author: Jason Hinkle
11:35

Basic editing with vi (vim) text editor for Unix
Click "Show more" for the table of contents of this video with shortcut links) This is a q...
published: 23 Nov 2010
author: Jason Hinkle
Basic editing with vi (vim) text editor for Unix
Basic editing with vi (vim) text editor for Unix
Click "Show more" for the table of contents of this video with shortcut links) This is a quick vi tutorial aimed at making simple edits to files on a server...- published: 23 Nov 2010
- views: 13419
- author: Jason Hinkle
6:04

cp (Unix)
cp is a UNIX command for copying files and directories. The command has three principal mo...
published: 18 Nov 2013
cp (Unix)
cp (Unix)
cp is a UNIX command for copying files and directories. The command has three principal modes of operation, expressed by the types of arguments presented to the program for copying a file to another file, one or more files to a directory, or for copying entire directories to another directory. The utility further accepts various command line option flags to detail the operations performed. The two major specifications are POSIX cp and GNU cp. GNU cp has many additional options over the POSIX version. Operating modes Cp has three principal modes of operation. These modes are inferred from the type and count of arguments presented to the program upon invocation. When the program has two arguments of path names to files, the program copies the contents of the first file to the second file, creating the second file if necessary. When the program has one or more arguments of path names of files and following those an argument of a path to a directory, then the program copies each source file to the destination directory, creating any files not already existing. When the program's arguments are the path names to two directories, cp copies all files in the source directory to the destination directory, creating any files or directories needed. This mode of operation requires an additional option flag, typically r, to indicate the recursive copying of directories. If the destination directory already exists, the source is copied into the destination, while a new directory is created if the destination does not exist. Usage Copying a file to another file: Copying file(s) to a directory Copying a directory to a directory (-r or -R must be used) Option flags f (force) -- specifies removal of the target file if it cannot be opened for write operations. The removal precedes any copying performed by the cp command. H (dereference) -- makes the cp command follow symbolic links (symlinks) so that the destination has the target file rather than a symlink to the target. i (interactive) -- prompts you with the name of a file to be overwritten. This occurs if the TargetDirectory or TargetFile parameter contains a file with the same name as a file specified in the SourceFile or SourceDirectory parameter. If you enter y or the locale's equivalent of y, the cp command continues. Any other answer prevents the cp command from overwriting the file. p (preserve) -- the p flag preserves the following characteristics of each source path in the corresponding target: The time of the last data modification and the time of the last access, the ownership (only if it has permissions to do this), and the file permission bits. R or r (recursive) -- copy directories recursively Examples Creating a copy of a file in the current directory: This copies prog.c to prog.bak. If the prog.bak file does not already exist, the cp command creates it. If it does exist, the cp command replaces its contents with the contents of the prog.c file. Copy two files in the current directory into another directory: This copies the files jones to /home/nick/clients/jones and smith to /home/nick/clients/smith. Copy a file to a new file and preserve the modification date, time, and access control list associated with the source file: This copies the smith file to the smith.jr file. Instead of creating the file with the current date and time stamp, the system gives the smith.jr file the same date and time as the smith file. The smith.jr file also inherits the smith file's access control protection. Copy a directory, including all its files and subdirectories, to another directory: This copies the directory clients, including all its files, subdirectories, and the files in those subdirectories, to the directory customers/clients. Some Unix systems behave differently in this mode, depending on the termination of directory paths. Using cp -R /home/nick/clients/ /home/nick/customers on a GNU system it behaves as expected; however, on a BSD system, it copies all the contents of the "clients" directory, instead of the directory clients itself. The same happens in both GNU and BSD systems if the path of the source directory ends in. or.. (with or without trailing slash). The copying of a file to an existing file is performed by opening the existing file in update mode, thereby preserving the files inode, which requires write access and results in the target file retaining the permissions it had originally. Related Unix commands cpio -- copy an entire directory structure from one place to another tar -- create an archive of files link -- system call to create a link to a file or directory ln -- create a link to a file or directory mv -- move a file or directory rm -- remove a file or directory unlink -- system call to remove a file or directory chmod -- change the mode (aka permissions) on a file or directory chown -- change ownership on a file or directory Attribution: Article text available under CC-BY-SA- published: 18 Nov 2013
- views: 1
14:00

vi - Wiki Article
The original code for vi was written by Bill Joy in 1976, as the visual mode for a line ed...
published: 20 May 2013
author: wikispeak10
vi - Wiki Article
vi - Wiki Article
The original code for vi was written by Bill Joy in 1976, as the visual mode for a line editor called ex that Joy had written with Chuck Haley. Bill Joy's ex...- published: 20 May 2013
- views: 14
- author: wikispeak10
11:56

umask
In computing, umask is a command that determines the settings of a mask that controls whic...
published: 16 Nov 2013
umask
umask
In computing, umask is a command that determines the settings of a mask that controls which file permissions are set for files and directories when they are created. It also refers to a function that sets the mask, and to the mask itself, which is formally known as the file mode creation mask. In UNIX, each file and directory has sets of attributes which control who is permitted access (aka modes). When a file or directory is created the permissions to be set are specified. The mask restricts which permissions are allowed. If the mask bit is set to "1", the corresponding permission will be disabled. For a bit set to "0", the corresponding permission will be determined by the program and the system. In other words, the mask acts as a last-stage filter that strips away permissions as a file or directory is created where the bit that is set to a "1". Since the permissions are categorized by owner, group and other "the mask" helps with defaulting access. The modes can be changed using chmod. Each program (technically called a process) has its own mask, which is applied whenever that process creates a new file. Each process is able to change the settings of its own mask using a function call. When the process is a shell, the mask is set with the umask command. When a shell, or any other process, launches a new process, the child process inherits the mask from its parent process. The mask does not work retroactively, that is, changes made to the mask only affect new files created after the changes are made. Generally, the mask only affects file permissions during the creation of new files and has no effect when file permissions are changed in existing files, however, in some specific cases it can help determine permissions when file permissions are changed in existing files using the chmod command. The mask is always stored as a group of bits. It may be displayed in binary, octal, or symbolic notation. Usually, it is represented in octal notation (e.g., 0754) or symbolic notation (e.g., u=wrx,g=rx,o=r) (see symbolic notation below for details). The umask command uses the same octal and symbolic notation as the chmod command. The umask command is used with Unix-like operating systems and the umask function is defined in the POSIX.1 specification. History The mask, the umask command, and the umask function were not part of the original implementation of UNIX. The operating system evolved in a relatively small computer center environment where security was not an issue. Unix eventually grew to serve hundreds of users from different organizations. At first, developers made creation modes for key files more restrictive, especially for cases of actual security breaches, but this was not a generally (or universally) workable solution. The mask and the umask command were introduced around 1978 between the sixth edition and the eighth edition of the operating system, so it could allow sites, groups, and individuals to choose their own defaults. The mask has since been implemented in most, if not all, of the contemporary implementations of UNIX-like (POSIX) operating systems. Typically for operating systems that don't support umask there is a toolkit that is available that has the command. Shell command In a shell, the mask is set by using the umask command. The syntax of the command is: (the items within the are optional) Displaying the current mask If the umask command is invoked without any arguments, it will display the current mask. The output will be in either octal or symbolic notation depending on the operating system used, however, invoking umask with the -S argument (i.e., umask -S) will force it to display the current mask in symbolic notation. For example: Setting the mask using octal notation If the umask command is invoked with an octal argument, it will directly set the bits of the mask to that argument: If fewer than 4 digits are entered, leading zeros are assumed. An error will result if the argument is not a valid octal number (or symbolic argument — see below) or if it has more than 4 digits. Octal codes used in the command Setting the mask using symbolic notation If the umask command is invoked with an argument using symbolic notation, it will add to, substract from, or directly set the bits of the mask as directed by the argument of the umask command. The symbolic notation is composed of permission-symbols, user-class-letters, and operators. The syntax of the in the umask command looks like this: There are no spaces allowed between the arguments. The only space is between the umask command itself and the arguments. Attribution: Article text available under CC-BY-SA- published: 16 Nov 2013
- views: 3
5:16

Vim Mode With Status Widget - Linux ZSH
https://github.com/gotbletu/shownotes/blob/master/zsh_vim_mode.txt Name : zsh Version : 5....
published: 27 Apr 2013
author: gotbletu
Vim Mode With Status Widget - Linux ZSH
Vim Mode With Status Widget - Linux ZSH
https://github.com/gotbletu/shownotes/blob/master/zsh_vim_mode.txt Name : zsh Version : 5.0.2-1 URL : http://www.zsh.org/ Description : A very advanced and p...- published: 27 Apr 2013
- views: 834
- author: gotbletu
31:15

Ms.Moda's Unisex Salon
More Video click link here http://www.damillproductions.com/ This screenplay is done in th...
published: 22 Nov 2012
author: Da Mill
Ms.Moda's Unisex Salon
Ms.Moda's Unisex Salon
More Video click link here http://www.damillproductions.com/ This screenplay is done in the description of a Unisex Salon which is a barber shop and a beauty...- published: 22 Nov 2012
- views: 305825
- author: Da Mill
17:50
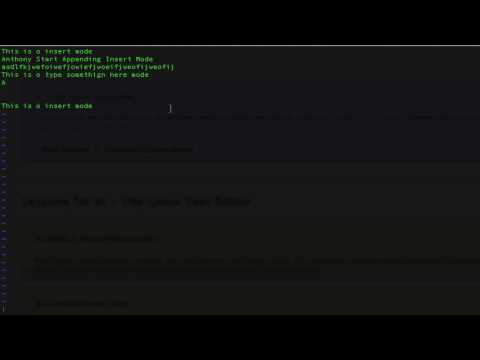
Learn Linux | Lesson: Vi Commands and Usage
Lesson 2 of the course working with Vi from linuxacademy.tv. Learn how to use Vi in differ...
published: 22 Jun 2012
author: pineheadtv
Learn Linux | Lesson: Vi Commands and Usage
Learn Linux | Lesson: Vi Commands and Usage
Lesson 2 of the course working with Vi from linuxacademy.tv. Learn how to use Vi in different modes. Learn the command line tools for each mode and see how f...- published: 22 Jun 2012
- views: 2857
- author: pineheadtv
5:35

grep - Wiki Article
Grep is a command-line utility for searching plain-text data sets for lines matching a reg...
published: 23 May 2013
author: wikispeak10
grep - Wiki Article
grep - Wiki Article
Grep is a command-line utility for searching plain-text data sets for lines matching a regular expression. Grep was originally developed for the Unix operati...- published: 23 May 2013
- views: 43
- author: wikispeak10
3:30

John the ripper tutorial
John the ripper tutorial, showing some of the modes and possibilities with john. John the ...
published: 08 Jun 2013
author: Webbh4tt
John the ripper tutorial
John the ripper tutorial
John the ripper tutorial, showing some of the modes and possibilities with john. John the Ripper is a fast password cracker, currently available for many fla...- published: 08 Jun 2013
- views: 463
- author: Webbh4tt
35:35
Quick Test Professional (QTP/UFT) Recording Modes
WELCOME TO H2K INFOSYS IT Staff Augmentation, Job placement assistance, Tech Support IT Tr...
published: 03 May 2013
author: Rao HTwoKInfosys
Quick Test Professional (QTP/UFT) Recording Modes
Quick Test Professional (QTP/UFT) Recording Modes
WELCOME TO H2K INFOSYS IT Staff Augmentation, Job placement assistance, Tech Support IT Training for corporate & Individuals, Fas...- published: 03 May 2013
- views: 262
- author: Rao HTwoKInfosys
15:17

Using vi The basics
More videos like this online at http://www.theurbanpenguin.com This video woll get you sta...
published: 23 May 2013
author: theurbanpenguin
Using vi The basics
Using vi The basics
More videos like this online at http://www.theurbanpenguin.com This video woll get you started with the basics and beyond on vi, the Linux text editor. First...- published: 23 May 2013
- views: 336
- author: theurbanpenguin
3:20

Piano Solo Unix Guitar & Piano Lesson Jazz
Belajar bermain Jazz....
published: 11 Mar 2013
author: arif budiono
Piano Solo Unix Guitar & Piano Lesson Jazz
Piano Solo Unix Guitar & Piano Lesson Jazz
Belajar bermain Jazz.- published: 11 Mar 2013
- views: 19
- author: arif budiono
1:32

Minimize to System Tray - AllTray - Ubuntu 8.10
NAME alltray -- Dock any program into the system tray on GTK2-based systems DESCRIPTION St...
published: 12 Jan 2009
author: gotbletu
Minimize to System Tray - AllTray - Ubuntu 8.10
Minimize to System Tray - AllTray - Ubuntu 8.10
NAME alltray -- Dock any program into the system tray on GTK2-based systems DESCRIPTION Start program with optional arguments provided in args and dock it to...- published: 12 Jan 2009
- views: 2767
- author: gotbletu
35:11

Recording Modes in QTP | UFT
===========================
WELCOME TO H2K INFOSYS
IT Staff Augmentation, Job placement as...
published: 12 Sep 2013
Recording Modes in QTP | UFT
Recording Modes in QTP | UFT
=========================== WELCOME TO H2K INFOSYS IT Staff Augmentation, Job placement assistance, Tech Support IT Training for corporate & Individuals, Fast track IT Training & Job placement assistance for OPT / MS graduates in USA Software Design, Development, QA Testing, Performance Testing & Support H2K Infosys is a one stop global online software training institution that offers a huge portfolio of software online training and onsite training in technological areas such as Software QA Testing (QA), Business Analysis (BA), HP QTP, HP LoadRunner, WebServices, Java, J2EE, Microsoft C# and ASP .NET, Oracle DBA to name a few. These online software training courses are designed for Individuals, and employees of forward thinking companies and other organizations to acquire, maintain, optimize and validate their IT skills. "With the changing trends in the market, innovation is the key to stay ahead" - H2Kinfosys provides software training with latest technologies to meet the current job market. H2Kinfosys is developing software projects for the current and future generations in Education, Healthcare, Finance, Supply chain, CRM, Hospitality, Cloud and Telecom domains. Why H2K..? 100% Job Oriented Instructor Led Face2Face True Live online Software Training with Cloud Test Lab to practice on Software Tools and Live Project work. Resume Prep & Review, Mock Interviews and Job Placement assistance. More interaction with student to faculty and student to student. Detailed presentations. Soft copy of Materiel to refer any time. Practical oriented / Job oriented Training. Practice on Software Tools & Real Time project scenarios. Weekly mock interviews / group discussions / interview related questions. Test Lab is in Cloud Technology - to practice on software tools. Pay onetime fee & repeat / re attending classes multiple times until student is comfortable with every topic. This feature is helpful to students who are new to I.T. Field. Depends on the batch schedule and student convenient, Student can repeat Weekend or Weekday batches and review the topic multiple times. QA Testing training is 80+ hours. We discuss about the real time project domains in Banking/Financial, Telecom, Supply Chain Management, CRM, Health care and other domains. We provide Recorded Videos for every class to review before and after the live class. The teaching methods / tools / topics we chosen are based on the current competitive job market. Visit http://www.h2kinfosys.com/advantages. QA Testing Training Course Highlights Module 1:Manual Testing Software Testing Life Cycle,SDLC,Waterfall vs. Agile QA Tester Role,Test Metrics,Types of Testing Software Testing Life Cycle,STLC,Defect Life Cycle Testing Methodologies,Software Testing process Test case,Test plan,RTM,Defect tracking Home works,Telecom,Banking,HealthCare,Supply chain domains. Role of QA,BA,Developer,Technical Architects etc. Module 2:HP Quality Center - ALM for Test management/ Defect Tracking Module 3:SQL (Database/Back End Testing) Module 4:UNIX / Linux Operating System/Backend Testing Module 5:HP QTP (Quick Test Professional) for Automation Testing Module 6:HP Loadrunner for Performance Testing Module 7:Review & questions on all topics,Configuration Management,CMMI,Six Sigma principles,Requirement (e.g. Sarbanes Oxley,HIPPA-Medical related),Interview Questions. How to prepare professional resume? Module 8: IBM Mainframe Testing Module 9: SAP Testing (Sales & Distribution (SD),Production Planning or CRM Or any one of the SAP) Module 10: WebServices (SOA) Testing using SoapUI tool Module 11: ETL and Data warehouse Testing Module 12: IBM Rational Quality Manager (RQM) Tool (It was Rational Test Manager)- published: 12 Sep 2013
- views: 17
Youtube results:
15:40

File Transfer Protocol - Wiki Article
File Transfer Protocol is a standard network protocol used to transfer files from one host...
published: 16 May 2013
author: wikispeak10
File Transfer Protocol - Wiki Article
File Transfer Protocol - Wiki Article
File Transfer Protocol is a standard network protocol used to transfer files from one host to another host over a TCP-based network, such as the Internet. FT...- published: 16 May 2013
- views: 24
- author: wikispeak10
1:21

sniffing passwords with intercepter-ng, backtrack 5 R3.
Firstly execute the program interceptor-ng, it is found on backtrack. also you can get it ...
published: 24 Mar 2013
author: HACKRICE
sniffing passwords with intercepter-ng, backtrack 5 R3.
sniffing passwords with intercepter-ng, backtrack 5 R3.
Firstly execute the program interceptor-ng, it is found on backtrack. also you can get it online for linux and windows. interceptor-ng is located in backtrac...- published: 24 Mar 2013
- views: 3026
- author: HACKRICE
18:04

3. SFU CMPT 300: User mode / kernel mode / hardware hierarchy: from machine language to applications
Episode 3 of the lecture series "Introduction to Operating Systems" course by Arrvindh Shr...
published: 26 Nov 2012
author: CMPT300 Videos
3. SFU CMPT 300: User mode / kernel mode / hardware hierarchy: from machine language to applications
3. SFU CMPT 300: User mode / kernel mode / hardware hierarchy: from machine language to applications
Episode 3 of the lecture series "Introduction to Operating Systems" course by Arrvindh Shriraman Topics highlighted in the episode: ๏ From machine languages ...- published: 26 Nov 2012
- views: 381
- author: CMPT300 Videos
4:05
Text mode box and comment drawing filter for vim / *nix command line
http://io9.in/i8 - boxes is a text filter which can draw any kind of ASCII art box around ...
published: 11 Jun 2012
author: nixcraftcom
Text mode box and comment drawing filter for vim / *nix command line
Text mode box and comment drawing filter for vim / *nix command line
http://io9.in/i8 - boxes is a text filter which can draw any kind of ASCII art box around its input text. A box can also be removed, even if it has been badl...- published: 11 Jun 2012
- views: 1441
- author: nixcraftcom



![#82 Battlefield 3 Knife Only Messerduell 2on2 [Let's Play Together | HD] #82 Battlefield 3 Knife Only Messerduell 2on2 [Let's Play Together | HD]](http://web.archive.org./web/20131130053922im_/http://i.ytimg.com/vi/F7xnOw6r4RE/0.jpg)









