Spam is unsolicited bulk email. The key term is “unsolicited” — if you signed up for a mailing list (commercial or otherwise) which you no longer wish to receive, that is not spam. The easy differentiation is that legitimate businesses will have a mailing policy posted on the site where you sign up for the mail, and will give you correct information about how to unsubscribe. NYU Email powered by Google features built-in spam filtering. For more information on spam, please see our NYU Email: Removing spam from your inbox.
NYU Email, powered by Google, features built-in spam filtering. To read more about how it works and how to use it, see the ServiceLink knowledge base.
NYU recommends that you use the NYU Email web interface instead of email programs (Outlook, iPhone Mail, etc.). However, if you choose to use a desktop email client, you must create a filtering rule based on specific spam rating levels. Mail that matches the rule is then redirected into a folder of your choice and you can decide how you wish to handle the redirected messages. The filter level you select will determine the amount of spam you receive. If you find that you are receiving too much spam in your Inbox, try adjusting the level of filtering to be more strict. If you find that desired mail is being filtered, select a level that is less strict.
IMPORTANT: Keep in mind that some legitimate messages will end up in your spam folder if they exhibit characteristics of spam, for example, lots of capital letters, many exclamation points, or phrases such as “click here.” Therefore, it is important to check your spam folder regularly to ensure that you receive messages that may have been inadvertently flagged as spam.
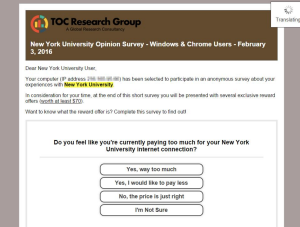
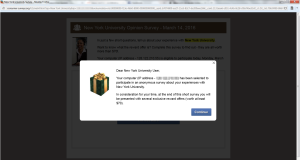
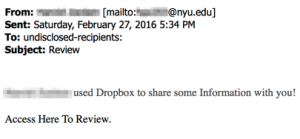
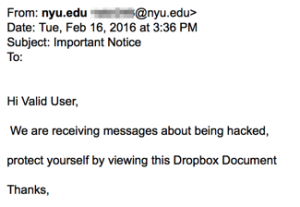
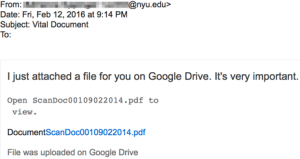
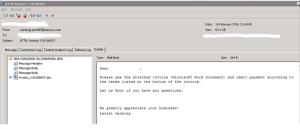
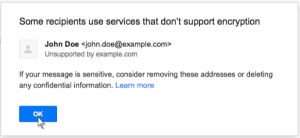
Phishing messages appear to be sent from NYU, NYU IT, or other organizations affiliated with NYU requesting your personal information such as name, date of birth, password, etc. Do not reply to these messages. NYU IT will never request your password information. If a message informs you of an impending account closure or similar action unless you comply with its demands, it is often a sign that the message is a phishing scam. Do not comply with the request. To report phishing or spam attempts, please follow the instructions in the ServiceLink knowledge base.
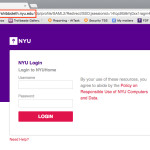
This is an example of a Phishing email:
*From:* Abul Mohammed, Majeed (2014) [mailto: Majeed.AbulMohammed.2014@live.rhul.ac.uk]
*Sent:* Thursday, October 08, 2015 12:10 PM
*Subject:* NEW YORK UNIVERSITY.
Access to your e-mail account is about to expired.
Please Click here <http://maillonyuedu.weebly.com/> to restore access to
your e-mail account.
We apologize for any inconvenience and appreciate your understanding.
Regards.
New York University
70 Washington Square South
New York, NY 10012 (This is NOT our zipcode)
212.998.1212
To report phishing or spam attempts and for security tips for using email, see:
www.nyu.edu/servicelink/041202716305490