Marco Rubio Leaks that the Phone Dragnet Has Expanded to “A Large Number of Companies”
Last night, Marco Rubio went on Fox News to try to fear-monger over the phone dragnet again.
He repeated the claim that the AP also idiotically parroted uncritically — that the government can only get three years of records for the culprits in the San Bernardino attack.
In the case of these individuals that conducted this attack, we cannot see any phone records for the first three years in which — you can only see them up to three years. You’ll not be able to see the full five-year picture.
Again, he’s ignoring the AT&T backbone records that cover virtually all of Syed Rizwan Farook’s 28-year life that are available, that 215 phone dragnet could never have covered Tashfeen Malik’s time in Pakistan and Saudi Arabia, and that EO 12333 collection not only would cover Malik’s time before she came to the US, but would also include Farook’s international calls going back well over 5 years.
So he’s either an idiot or he’s lying on that point.
I’m more interested in what he said before that, because he appears to have leaked a classified detail about the ongoing USA Freedom dragnet: that they’ve been issuing orders to a “large and significant number of companies” under the new dragnet.
There are large and significant number of companies that either said, we are not going to collect records at all, we’re not going to have any records if you come asking for them, or we’re only going to keep them on average of 18 months. When the intelligence community or law enforcement comes knocking and subpoenas those records, in many cases there won’t be any records because some of these companies already said they’re not going to hold these records. And the result is that we will not be able in many cases to put together the full puzzle, the full picture of some of these individuals.
Let me clear: I’m certain this fact, that the IC has been asking for records from “a large number of companies,” is classified. For a guy trying to run for President as an uber-hawk, leaking such details (especially in appearance where he calls cleared people who leak like Edward Snowden “traitors”) ought to be entirely disqualifying.
But that detail is not news to emptywheel readers. As I noted in my analysis of the Intelligence Authorization the House just passed, James Clapper would be required to do a report 30 days after the authorization passes telling Congress which “telecoms” aren’t holding your call records for 18 months.
Section 307: Requires DNI to report if telecoms aren’t hoarding your call records
This adds language doing what some versions of USA Freedom tried to requiring DNI to report on which “electronic communications service providers” aren’t hoarding your call records for at least 18 months. He will have to do a report after 30 days listing all that don’t (bizarrely, the bill doesn’t specify what size company this covers, which given the extent of ECSPs in this country could be daunting), and also report to Congress within 15 days if any of them stop hoarding your records.
That there would be so many companies included Clapper would need a list surprised me, a bit. When I analyzed the House Report on the bill, I predicted USAF would pull in anything that might be described as a “call.”
We have every reason to believe the CDR function covers all “calls,” whether telephony or Internet, unlike the existing dragnet. Thus, for better and worse, far more people will be exposed to chaining than under the existing dragnet. It will catch more potential terrorists, but also more innocent people. As a result, far more people will be sucked into the NSA’s maw, indefinitely, for exploitation under all its analytical functions. This raises the chances that an innocent person will get targeted as a false positive.
At the same time, I thought that the report’s usage of “phone company” might limit collection to the providers that had been included — AT&T, Verizon, and Sprint — plus whatever providers cell companies aren’t already using their backbone, as well as the big tech companies that by dint of being handset manufacturers, that is, “phone” companies, could be obligated to turn over messaging records — things like iMessage and Skype metadata.
Nope. According to uber-hawk who believes leakers are traitors Marco Rubio, a “large number” of companies are getting requests.
From that I assume that the IC is sending requests to the entire universe of providers laid out by Verizon Associate General Counsel Michael Woods in his testimony to SSCI in 2014:
Woods describes Skype (as the application that carried 34% of international minutes in 2012), as well as applications like iMessage and smaller outlets of particular interest like Signal as well as conferencing apps.
So it appears the intelligence committees, because they’re morons who don’t understand technology (and ignored Woods) got themselves in a pickle, because they didn’t realize that if you want full coverage from all “phone” communication, you’re going to have to go well beyond even AT&T, Verizon, Sprint, Apple, Microsoft, and Google (all of which have compliance departments and the infrastructure to keep such records). They are going to try to obtain all the call records, from every little provider, whether or not they actually have the means with which to keep and comply with such requests. Some — Signal might be among them — simply aren’t going to keep records, which is what Rubio is complaining about.
That’s a daunting task — and I can see why Rubio, if he believes that’s what needs to happen, is flustered by it. But, of course, it has nothing to do with the end of the old gap-filled dragnet. Indeed, that daunting problem arises because the new program aspires to be more comprehensive.
In any case, I’m grateful Rubio has done us the favor of laying out precisely what gaps the IC is currently trying to fill, but hawks like Rubio will likely call him a traitor for doing so.
The Reasons to Shut Down the (Domestic) Internet Dragnet: Purpose and Dissemination Limits, Correlations, and Functionality
Charlie Savage has a story that confirms (he linked some of my earlier reporting) something I’ve long argued: NSA was willing to shut down the Internet dragnet in 2011 because it could do what it wanted using other authorities. In it, Savage points to an NSA IG Report on its purge of the PRTT data that he obtained via FOIA. The document includes four reasons the government shut the program down, just one of which was declassified (I’ll explain what is probably one of the still-classified reasons probably in a later post). It states that SPCMA and Section 702 can fulfill the requirements that the Internet dragnet was designed to meet. The government had made (and I had noted) a similar statement in a different FOIA for PRTT materials in 2014, though this passage makes it even more clear that SPCMA — DOD’s self-authorization to conduct analysis including US persons on data collected overseas — is what made the switch possible.
It’s actually clear there are several reasons why the current plan is better for the government than the previous dragnet, in ways that are instructive for the phone dragnet, both retrospectively for the USA F-ReDux debate and prospectively as hawks like Tom Cotton and Jeb Bush and Richard Burr try to resuscitate an expanded phone dragnet. Those are:
- Purpose and dissemination limits
- Correlations
- Functionality
Purpose and dissemination limits
Both the domestic Internet and phone dragnet limited their use to counterterrorism. While I believe the Internet dragnet limits were not as stringent as the phone ones (at least in pre 2009 shutdown incarnation), they both required that the information only be disseminated for a counterterrorism purpose. The phone dragnet, at least, required someone sign off that’s why information from the dragnet was being disseminated.
Admittedly, when the FISC approved the use of the phone dragnet to target Iran, it was effectively authorizing its use for a counterproliferation purpose. But the government’s stated admissions — which are almost certainly not true — in the Shantia Hassanshahi case suggest the government would still pretend it was not using the phone dragnet for counterproliferation purposes. The government now claims it busted Iranian-American Hassanshahi for proliferating with Iran using a DEA database rather than the NSA one that technically would have permitted the search but not the dissemination, and yesterday Judge Rudolph Contreras ruled that was all kosher.
But as I noted in this SPCMA piece, the only requirement for accessing EO 12333 data to track Americans is a foreign intelligence purpose.
Additionally, in what would have been true from the start but was made clear in the roll-out, NSA could use this contact chaining for any foreign intelligence purpose. Unlike the PATRIOT-authorized dragnets, it wasn’t limited to al Qaeda and Iranian targets. NSA required only a valid foreign intelligence justification for using this data for analysis.
The primary new responsibility is the requirement:
- to enter a foreign intelligence (FI) justification for making a query or starting a chain,[emphasis original]
Now, I don’t know whether or not NSA rolled out this program because of problems with the phone and Internet dragnets. But one source of the phone dragnet problems, at least, is that NSA integrated the PATRIOT-collected data with the EO 12333 collected data and applied the protections for the latter authorities to both (particularly with regards to dissemination). NSA basically just dumped the PATRIOT-authorized data in with EO 12333 data and treated it as such. Rolling out SPCMA would allow NSA to use US person data in a dragnet that met the less-restrictive minimization procedures.
That means the government can do chaining under SPCMA for terrorism, counterproliferation, Chinese spying, cyber, or counter-narcotic purposes, among others. I would bet quite a lot of money that when the government “shut down” the DEA dragnet in 2013, they made access rules to SPCMA chaining still more liberal, which is great for the DEA because SPCMA did far more than the DEA dragnet anyway.
So one thing that happened with the Internet dragnet is that it had initial limits on purpose and who could access it. Along the way, NSA cheated those open, by arguing that people in different function areas (like drug trafficking and hacking) might need to help out on counterterrorism. By the end, though, NSA surely realized it loved this dragnet approach and wanted to apply it to all NSA’s functional areas. A key part of the FISC’s decision that such dragnets were appropriate is the special need posed by counterterrorism; while I think they might well buy off on drug trafficking and counterproliferation and hacking and Chinese spying as other special needs, they had not done so before.
The other thing that happened is that, starting in 2008, the government started putting FBI in a more central role in this process, meaning FBI’s promiscuous sharing rules would apply to anything FBI touched first. That came with two benefits. First, the FBI can do back door searches on 702 data (NSA’s ability to do so is much more limited), and it does so even at the assessment level. This basically puts data collected under the guise of foreign intelligence at the fingertips of FBI Agents even when they’re just searching for informants or doing other pre-investigative things.
In addition, the minimization procedures permit the FBI (and CIA) to copy entire metadata databases.
FBI can “transfer some or all such metadata to other FBI electronic and data storage systems,” which seems to broaden access to it still further.
Users authorized to access FBI electronic and data storage systems that contain “metadata” may query such systems to find, extract, and analyze “metadata” pertaining to communications. The FBI may also use such metadata to analyze communications and may upload or transfer some or all such metadata to other FBI electronic and data storage systems for authorized foreign intelligence or law enforcement purposes.
In this same passage, the definition of metadata is curious.
For purposes of these procedures, “metadata” is dialing, routing, addressing, or signaling information associated with a communication, but does not include information concerning the substance, purport, or meaning of the communication.
I assume this uses the very broad definition John Bates rubber stamped in 2010, which included some kinds of content. Furthermore, the SMPs elsewhere tell us they’re pulling photographs (and, presumably, videos and the like). All those will also have metadata which, so long as it is not the meaning of a communication, presumably could be tracked as well (and I’m very curious whether FBI treats location data as metadata as well).
Whereas under the old Internet dragnet the data had to stay at NSA, this basically lets FBI copy entire swaths of metadata and integrate it into their existing databases. And, as noted, the definition of metadata may well be broader than even the broadened categories approved by John Bates in 2010 when he restarted the dragnet.
So one big improvement between the old domestic Internet dragnet and SPCMA (and 702 to a lesser degree, and I of course, improvement from a dragnet-loving perspective) is that the government can use it for any foreign intelligence purpose.
At several times during the USA F-ReDux debate, surveillance hawks tried to use the “reform” to expand the acceptable uses of the dragnet. I believe controls on the new system will be looser (especially with regards to emergency searches), but it is, ostensibly at least, limited to counterterrorism.
One way USA F-ReDux will be far more liberal, however, is in dissemination. It’s quite clear that the data returned from queries will go (at least) to FBI, as well as NSA, which means FBI will serve as a means to disseminate it promiscuously from there.
Correlations
Another thing replacing the Internet dragnet with 702 access does it provide another way to correlate multiple identities, which is critically important when you’re trying to map networks and track all the communication happening within one. Under 702, the government can obtain not just Internet “call records” and the content of that Internet communication from providers, but also the kinds of thing they would obtain with a subpoena (and probably far more). As I’ve shown, here are the kinds of things you’d almost certainly get from Google (because that’s what you get with a few subpoenas) under 702 that you’d have to correlate using algorithms under the old Internet dragnet.
- a primary gmail account
- two secondary gmail accounts
- a second name tied to one of those gmail accounts
- a backup email (Yahoo) address
- a backup phone (unknown provider) account
- Google phone number
- Google SMS number
- a primary login IP
- 4 other IP logins they were tracking
- 3 credit card accounts
- Respectively 40, 5, and 11 Google services tied to the primary and two secondary Google accounts, much of which would be treated as separate, correlated identifiers
Every single one of these data points provides a potentially new identity that the government can track on, whereas the old dragnet might only provide an email and IP address associated with one communication. The NSA has a great deal of ability to correlate those individual identifiers, but — as I suspect the Paris attack probably shows — that process can be thwarted somewhat by very good operational security (and by using providers, like Telegram, that won’t be as accessible to NSA collection).
This is an area where the new phone dragnet will be significantly better than the existing phone dragnet, which returns IMSI, IMEI, phone number, and a few other identifiers. But under the new system, providers will be asked to identify “connected” identities, which has some limits, but will nonetheless pull some of the same kind of data that would come back in a subpoena.
Functionality
While replacing the domestic Internet dragnet with SPCMA provides additional data with which to do correlations, much of that might fall under the category of additional functionality. There are two obvious things that distinguish the old Internet dragnet from what NSA can do under SPCMA, though really the possibilities are endless.
The first of those is content scraping. As the Intercept recently described in a piece on the breathtaking extent of metadata collection, the NSA (and GCHQ) will scrape content for metadata, in addition to collecting metadata directly in transit. This will get you to different kinds of connection data. And particularly in the wake of John Bates’ October 3, 2011 opinion on upstream collection, doing so as part of a domestic dragnet would be prohibitive.
In addition, it’s clear that at least some of the experimental implementations on geolocation incorporated SPCMA data.
I’m particularly interested that one of NSA’s pilot co-traveler programs, CHALKFUN, works with SPCMA.
Chalkfun’s Co-Travel analytic computes the date, time, and network location of a mobile phone over a given time period, and then looks for other mobile phones that were seen in the same network locations around a one hour time window. When a selector was seen at the same location (e.g., VLR) during the time window, the algorithm will reduce processing time by choosing a few events to match over the time period. Chalkfun is SPCMA enabled1.
1 (S//SI//REL) SPCMA enables the analytic to chain “from,” “through,” or “to” communications metadata fields without regard to the nationality or location of the communicants, and users may view those same communications metadata fields in an unmasked form. [my emphasis]
Now, aside from what this says about the dragnet database generally (because this makes it clear there is location data in the EO 12333 data available under SPCMA, though that was already clear), it makes it clear there is a way to geolocate US persons — because the entire point of SPCMA is to be able to analyze data including US persons, without even any limits on their location (meaning they could be in the US).
That means, in addition to tracking who emails and talks with whom, SPCMA has permitted (and probably still does) permit NSA to track who is traveling with whom using location data.
Finally, one thing we know SPCMA allows is tracking on cookies. I’m of mixed opinion on whether the domestic Internet ever permitted this, but tracking cookies is not only nice for understanding someone’s browsing history, it’s probably critical for tracking who is hanging out in Internet forums, which is obviously key (or at least used to be) to tracking aspiring terrorists.
Most of these things shouldn’t be available via the new phone dragnet — indeed, the House explicitly prohibited not just the return of location data, but the use of it by providers to do analysis to find new identifiers (though that is something AT&T does now under Hemisphere). But I would suspect NSA either already plans or will decide to use things like Supercookies in the years ahead, and that’s clearly something Verizon, at least, does keep in the course of doing business.
All of which is to say it’s not just that the domestic Internet dragnet wasn’t all that useful in its current form (which is also true of the phone dragnet in its current form now), it’s also that the alternatives provided far more than the domestic Internet did.
Jim Comey recently said he expects to get more information under the new dragnet — and the apparent addition of another provider already suggests that the government will get more kinds of data (including all cell calls) from more kinds of providers (including VOIP). But there are also probably some functionalities that will work far better under the new system. When the hawks say they want a return of the dragnet, they actually want both things: mandates on providers to obtain richer data, but also the inclusion of all Americans.
It’s Not Just the FISA Court, It’s the Game of Surveillance Whack-a-Mole
In response to this post from Chelsea Manning, the other day I did the first in what seems to have become a series of posts arguing that we should eliminate the FISA Court, but that the question is not simple. In that post, I laid out the tools the FISC has used, with varying degrees of success, in reining in Executive branch spying, especially in times of abuse.
In this post, I want to lay out how reining in surveillance isn’t just about whether the secret approval of warrants and orders would be better done by the FISC or a district court. It’s about whack-a-mole.
That’s because, right now, there are four ways the government gives itself legal cover for expansive surveillance:
- FISC, increasingly including programs
- EO 12333, including SPCMA
- Magistrate warrants and orders without proper briefing
- Administrative orders and/or voluntary cooperation
FISA Court
The government uses the FISA court to get individualized orders for surveillance in this country and, to a less clear extent, surveillance of Americans overseas. That’s the old-fashioned stuff that could be done by a district court. But it’s also one point where egregious source information — be it a foreign partner using dubious spying techniques, or, as John Brennan admitted in his confirmation hearing, torture — gets hidden. No defendant has ever been able to challenge the basis for the FISA warrant used against them, which is clearly not what Congress said it intended in passing FISA. But given that’s the case, it means a lot of prosecutions that might not pass constitutional muster, because of that egregious source information, get a virgin rebirth in the FISC.
In addition, starting 2004, the government started using the FISA Court to coerce corporations to continue domestic collection programs they had previously done voluntarily. As I noted, while I think the FISC’s oversight of these programs has been mixed, the FISC has forced the government to hew closer (though not at) the law.
EO 12333, including SPCMA
The executive branch considers FISA just a subset of EO 12333, the Reagan Executive Order governing the intelligence community — a carve out of collection requiring more stringent rules. At times, the Intelligence Community have operated as if EO 12333 is the only set of rules they need to follow — and they’ve even secretly rewritten it at least once to change the rules. The government will always assert the right to conduct spying under EO 12333 if it has a technical means to bypass that carve out. That’s what the Bush Administration claimed Stellar Wind operated under. And at precisely the time the FISC was imposing limits on the Internet dragnet, the Executive Brach was authorizing analysis of Americans’ Internet metadata collected overseas under SPCMA.
EO 12333 derived data does get used against defendants in the US, though it appears to be laundered through the FISC and/or parallel constructed, so defendants never get the opportunity to challenge this collection.
Magistrate warrants and orders
Even when the government goes to a Title III court — usually a magistrate judge — to get an order or warrant for surveillance, that surveillance often escapes real scrutiny. We’ve seen this happen with Stingrays and other location collection, as well as FBI hacking; in those cases, the government often didn’t fully brief magistrates about what they’re approving, so the judges didn’t consider the constitutional implications of it. There are exceptions, however (James Orenstein, the judge letting Apple challenge the use of an All Writs Act to force it to unlock a phone, is a notable one), and that has provided periodic checks on collection that should require more scrutiny, as well as public notice of those methods. That’s how, a decade after magistrates first started to question the collection of location data using orders, we’re finally getting circuit courts to review the issue. Significantly, these more exotic spying techniques are often repurposed foreign intelligence methods, meaning you’ll have magistrates and other TIII judges weighing in on surveillance techniques being used in parallel programs under FISA. At least in the case of Internet data, that may even result in a higher standard of scrutiny and minimization being applied to the FISA collection than the criminal investigation collection.
Administrative orders and/or voluntary cooperation
Up until 2006, telecoms willing turned over metadata on Americans’ calls to the government under Stellar Wind. Under Hemisphere, AT&T provides the government call record information — including results of location-based analysis, on all the calls that used its networks, not just AT&T customers — sometimes without an order. For months after Congress was starting to find a way to rein in the NSA phone dragnet with USA Freedom Act, the DEA continued to operate its own dragnet of international calls that operated entirely on administrative orders. Under CISA, the government will obtain and disseminate information on cybersecurity threats that it wouldn’t be able to do under upstream 702 collection; no judge will review that collection. Until 2009, the government was using NSLs to get all the information an ISP had on a user or website, including traffic information. AT&T still provides enhanced information, including the call records of friends and family co-subscribers and (less often than in the past) communities of interest.
These six examples make it clear that, even with Americans, even entirely within the US, the government conducts a lot of spying via administrative orders and/or voluntary cooperation. It’s not clear this surveillance had any but internal agency oversight, and what is known about these programs (the onsite collaboration that was probably one precursor to Hemisphere, the early NSL usage) makes it clear there have been significant abuses. Moreover, a number of these programs represent individual (the times when FBI used an NSL to get something the FISC had repeatedly refused to authorize under a Section 215 order) or programmatic collection (I suspect, CISA) that couldn’t be approved under the auspices of the FISC.
All of which is to say the question of what to do to bring better oversight over expansive surveillance is not limited to the short-comings of the FISC. It also must contend with the way the government tends to move collection programs when one method proves less than optimal. Where technologically possible, it has moved spying offshore and conducted it under EO 12333. Where it could pay or otherwise bribe and legally shield providers, it moved to voluntary collection. Where it needed to use traditional courts, it often just obfuscated about what it was doing. The primary limits here are not legal, except insofar as legal niceties and the very remote possibility of transparency raise corporate partner concerns.
We need to fix or eliminate the FISC. But we need to do so while staying ahead of the game of whack-a-mole.
Could Corporations Include CISA Non-Participation in Transparency Reports? Would It Even Mean Anything?
I confess I don’t know the answer to this question, but I’m going to pose it anyway. Could companies report non-participation in CISA — or whatever the voluntary cyber information sharing program that will soon roll out is eventually called — in their transparency reports?
I ask in part because there’s great uncertainty about whether tech companies support or oppose the measure. The Business Software Alliance suggested they supported a data sharing bill, until Fight for the Future made a stink, when at least some of them pulled off (while a number of other BSA members, like Adobe, IBM, and Siemens, will surely embrace the bill). A number of companies have opposed CISA, either directly (like Apple) or via the Computer and Communications Industry Association. But even Google, which is a CCIA member, still wants a way to share information even if they express concerns about CISA’s current form. Plus, there some indication that some of the companies claiming to oppose CISA — most notably, Facebook — are secretly lobbying in favor of it.
In the wake of CISA passing, activists are wondering if companies would agree not to participate (because participation is, as Richard Burr reminded over and over, voluntary, even if the key voluntary participants will also be bidding on a $50 billion contract as CISA rolls out). But I’m not sure what that would even mean.
So, first, would companies legally be permitted to claim in their transparency reports that they did not voluntarily participate in CISA? There are a lot of measures that prohibit the involuntary release of information about companies’ voluntary participation in CISA. But nothing in the bill that seems to prohibit the voluntary release of information about companies’ voluntary non-participation.
But even if a company made such a claim — or claimed that they only share cyber indicators with legal process — would it even be meaningful? Consider: Most of the companies that might make such a claim get hacked. Even Apple, the company that has taken the lead on pushing back against the government, has faced a series of attacks and/or vulnerabilities of late, both in its code and its app store. Both any disclosures it made to the Federal government and to its app vendors would be covered by CISA unless Apple deliberately disclosed that information outside the terms of CISA — for example, by deliberately leaving personally identifiable information in any code it shared, which it’s not about to do. Apple will enjoy the protections in CISA whether it asked for them or not. I can think of just two ways to avoid triggering the protections of CISA: either to only report such vulnerabilities as a crime report to FBI (which, because it bypassed the DHS, would not get full protection, and which would be inappropriate for most kinds of vulnerability disclosures), or to publicly disclose everything to the public. And that’s assuming there aren’t more specific disclosures — such as attempts to attack specific iCloud accounts — that would legitimately be intelligence reports. Google tells users if they think state actors are trying to compromise their accounts; is this appropriate to share with the government without process? Moreover, most of the companies that would voluntarily not participate already have people with clearance who can and do receive classified intelligence from the government. Plus, these companies can’t choose not to let their own traffic that transits communications backbone be scanned by the backbone owners.
In other words, I’m not sure how a company can claim not to participate in CISA once it goes into effect unless it doesn’t share any information. And most of the big tech companies are already sharing this information among themselves, they want to continue to do that sharing, and that sharing would get CISA protections.
The problem is, there are a number of kinds of information sharing that will get the permission of CISA, all of which would count as “participating in it.” Anything Apple shared with the government or other companies would get CISA protection. But that’s far different than taking a signature the government shares and scanning all backbone traffic for instances of it, which is what Verizon and AT&T will almost certainly be doing under CISA. That is, there are activities that shouldn’t require legal process, and activities that currently do but will not under CISA. And to get a meaningful sense of whether someone is “participating” in CISA by performing activities that otherwise would require legal process, you’d need a whole lot of details about what they were doing, details that not even criminal defendants will ever get. You’d even need to distinguish activities companies would do on their own accord (Apple’s own scans of its systems for known vulnerabilities) from things that came pursuant to information received from the federal government (a scan on a vulnerability Apple learned about from the government).
We’re never going to get that kind of information from a transparency report, except insofar as companies detail the kinds of things they require legal process for in spite of CISA protection for doing them without legal process. That would not be the same thing as non-participation in CISA — because, again, most of the companies that have raised objections already share information at least with industry partners. But that’s about all we’d get short of really detailed descriptions of any scrubbing that goes on during such information sharing.
What’s a Little (or a Lot) Cooperation Among Spies?
 A key point in the ProPublica/NYT piece on AT&T’s close cooperation with the NSA (and, though not stated explicitly, other agencies) on spying is that AT&T was the telecom that helped NSA spy on the UN.
A key point in the ProPublica/NYT piece on AT&T’s close cooperation with the NSA (and, though not stated explicitly, other agencies) on spying is that AT&T was the telecom that helped NSA spy on the UN.
It provided technical assistance in carrying out a secret court order permitting the wiretapping of all Internet communications at the United Nations headquarters, a customer of AT&T.
If you read the underlying document, it actually shows that NSA had a traditional FISA order requiring the cooperation (remember, “agents of foreign powers,” as diplomats are, are among the legal wiretap targets under FISA, no matter what we might think about NSA spying on UN in our own country) — meaning whatever telecom serviced the UN legally had to turn over the data. And a big part of AT&T’s cooperation, in addition to technically improving data quality, involved filtering the data to help NSA avoid overload.
BLARNEY began intermittent enablement of DNI traffic for TOPI assessment and feedback. This feedback is being used by the BLARNEY target development team to support an ongoing filtering and throttling of data volumes. While BLARNEY is authorized full-take access under the NSA FISA, collected data volumes would flood PINWALE allocations within hours without a robust filtering mechanism.
In other words, AT&T helped NSA, ironically, by helping it limit what data it took in. Arguably, that’s an analytical role (who builds the algorithms in the filter?), but it’s one that limits how much actually gets turned over to the government.
That doesn’t mean the cooperation was any less valued, nor does it mean it didn’t go beyond what AT&T was legally obliged to do under the FISA order. But it’s not evidence AT&T would wiretap a non-legal (private corporation) target as a favor for NSA. That evidence may exist, somewhere, but it’s not in this story, except insofar as it mentions Stellar Wind, where AT&T was doing such things.
To be fair, AT&T’s UN cooperation is actually emphasized in this story because it was a key data point in the worthwhile ProPublica piece explaining how they proved Fairview was AT&T.
In April 2012, an internal NSA newsletter boasted about a successful operation in which NSA spied on the United Nations headquarters in New York City with the help of its Fairview and Blarney programs. Blarney is a program that undertakes surveillance that is authorized by the Foreign Intelligence Surveillance Court.
FAIRVIEW and BLARNEY engineers collaborated to enable the delivery of 700Mbps of paired packet switched traffic (DNI) traffic from access to an OC192 ring serving the United Nations mission in New York … FAIRVIEW engineers and the partner worked to provide the correct mapping, and BLARNEY worked with the partner to correct data quality issues so the data could be handed off to BLARNEY engineers to enable processing of the DNI traffic.
We found historical records showing that AT&T was paid $1 million a year to operate the U.N.’s fiber optic provider in 2011 and 2012. A spokesman for the U.N. secretary general confirmed that the organization “has a current contract with AT&T” to operate the fiber optic network at the U.N. headquarters in New York.
That is, the UN story is important largely because there are public records proving that AT&T was the provider in question, not because it’s the most egregious example of AT&T’s solicitous relationship with the nation’s spies.
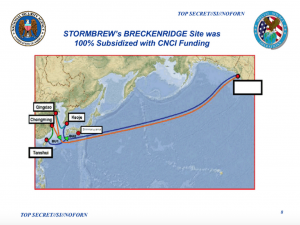
Also in that story proving how they determined Fairview was AT&T and Stormbrew included Verizon was the slide above, bragging that the Comprehensive National Cybersecurity Initiative 100% subsidized Verizon’s Breckenridge site at a new cable landing carrying traffic from China.
It’s not entirely clear what that means — it might just refer to the SCIF, power supply, and servers needed to run the TURMOIL (that is, passive filtering) deployments the NSA wanted to track international traffic with China. But as ProPublica lays out, the NSA was involved the entire time Verizon was planning this cable landing. Another document on CNCI shows that in FY2010 — while significantly less than AT&T’s Fairview — NSA was dumping over $100M into Stormbrew and five times as much money into “cyber” than on FISA (in spite of the fact that they admit they’re really doing all this cybering to catch attacks on the US, meaning it has to ostensibly be conducted under FISA, even if FISC had not yet and may never have approved a cyber certificate for upstream 702). And those numbers date to the year after the Breckenridge project was put on line, and at a time when Verizon was backing off an earlier closer relationship with the Feds.
How much did Verizon really get for that cable landing, what did they provide in exchange, and given that this was purpose-built to focus on Chinese hacking 6 years ago, why is China still eating our lunch via hacking? And if taxpayers are already subsidizing Verizon 100% for capital investments, why are we still paying our cell phone bills?
Particularly given the clear focus on cyber at this cable landing, I recall the emphasis on Department of Commerce when discussing the government’s partnership with industry in PPD-20, covering authorizations for various cyber activities, including offensive cyberwar (note the warning I gave for how Americans would start to care about this Snowden disclosure once our rivals, like China, retaliate). That is, the government has Commerce use carrots and sticks to get cooperation from corporations, especially on cybersecurity.
None of this changes the fact that AT&T has long been all too happy to spy on its customers for the government. It just points to how little we know about these relationships, and how much quid pro quo there really is. We know from PRISM discussions that the providers could negotiate how they accomplished an order (as AT&T likely could with the order to wiretap the UN), and that’s one measure of “cooperation.” But there’s a whole lot else to this kind of cooperation.
Update: Credo released a statement in response to the story.
As a telecom that can be compelled to participate in unconstitutional surveillance, we know how important it is to fight for our customers’ privacy and only hand over information related to private communications when required by law,” said CREDO Mobile Vice President Becky Bond. “It’s beyond disturbing though sadly not surprising what’s being reported about a secret government relationship with AT&T that NSA documents describe as ‘highly collaborative’ and a ‘partnership, not a contractual relationship,’
CREDO Mobile supports full repeal of the illegal surveillance state as the only way to protect Americans from illegal government spying,” Bond continued, “and we challenge AT&T to demonstrate concern for its customers’ constitutional rights by joining us in public support of repealing both the Patriot Act and FISA Amendments Act.
AT&T Pulled Cell Location for Its “Mobility Cell Data”
ProPublica and NYT have an important story that confirms what we’ve long known — that AT&T, operating under the Fairview program — is all too happy to do business with the NSA. As part of the story, they note that in 2011, AT&T started providing cell data to NSA under the BR FISA program.
In 2011, AT&T began handing over 1.1 billion domestic cellphone calling records a day to the NSA after “a push to get this flow operational prior to the tenth anniversary of 9/11,” according to an internal agency newsletter. This revelation is striking because after Snowden disclosed the program of collecting the records of Americans’ phone calls, intelligence officials told reporters that, for technical reasons, it consisted mostly of landline phone records.
They base the claim on this document, which reads,
On 29 August, FAIRVIEW started delivering Mobility Business Records traffic into MAINWAY under the existing Business Record (BR) FISA authorization. The intent of the Business Records FISA program is to detect previously unknown terrorist threats in the United States through the cell chaining of metadata. This new metadata flow is associated with a cell phone provider and will generate an estimated 1.1 billion cellular records a day in addition to the 700M records delivered currently under the BR FISA. After extensive dialogue with the consumers of the BR data, repeated testing, a push to get this flow operational prior to the tenth anniversary of 9/11, and extensive coordination with external entities via our OGC (to include: FBI, DOJ, ODNI, and FISC) NSA received approval to initiate this dataflow on August 29, 2011. Analysts have already reported seeing BR Cellular records in the Counter Terrorism call-chaining database queries.
Though it provides important new context, that NSA started receiving mobile data on August 29, 2011 is not new news (though that it was getting it from AT&T is). The government released the notice it gave to the House Judiciary Committee that it was receiving that data in October 2013 under FOIA (indeed, this document is one I have pointed to to refute claims that the program didn’t collect cell data).
All that said, the notice, taken together with the context of the internal announcement, does explain more about why the NSA wasn’t getting as much cell data as they wanted.
In the case of Fairview and the collection started on August 29, 2011, the provider “remove[d] the cell [redacted] location information [redacted] before providing the CDRs to NSA.”
Before initiating the acquisition of mobility data, NSA undertook extensive testing to ensure strict compliance with the terms of the FISC Orders. The Court’s Orders are designed to protect the civil liberties and privacy interests of Americans. Following completion of testing, on 29 August 2011, NSA began to receive approximately [redacted] CDRs per day and enter these records into our BR FISA bulk metadata architecture.
[redacted] NSA requested that the [redacted] remove the cell [redacted] location information [redacted] before providing the CDRs to NSA. Consequently, NSA is not currently receiving this field as part of the data being acquired. [redacted]
As the NYT reported earlier this week, NSA had given Verizon Wireless a separate order for phone dragnet order in 2010. But the redaction in the notice to Congress on obtaining mobility data from a year later seems to address the problem with obtaining location information.
We know from the Congressional notice AT&T was willing to strip it. For a lot of reasons, it’s likely Verizon was unwilling to strip it.
This is one of the possible explanations I’ve posited for why NSA wasn’t getting cell data from Verizon, because any provider is only obliged to give business records they already have on hand, and it would be fairly easy to claim stripping the cell location data made it a new business record.
Which is another important piece of evidence for the case made against AT&T in the story. They were willing to play with records they were handing over to the government in ways not required by the law.
Though who knows if that remain(ed) the case? To get to the 30% figure quoted in all the pieces claiming NSA wasn’t getting cell data, you’d probably have to have AT&T excluded as well. So maybe after the Snowden releases, they, too, refused to do things they weren’t required to do by law (though because it had the Hemisphere database which could easily select records, that may have been harder to do).
Update: Adding that FISC took judicial notice of some magistrates’ rulings you needed more than a subpoena for location data in 2006, after Congress said you could only get what you could get with a subpoena in the 2006 PATRIOT Reauthorization. So it’s possible any squeamishness about location collection dates to that point, though we know FISC did still permit the government to get location data with 215 orders.
Did NSA Add a New Dragnet Provider with Its Latest Order?
Cryptome has published the latest phone dragnet order. Contrary to reports, the dragnet order is only for two months (until the end of August), not until the expiration of the bulk dragnet in November, plus retroactive collection to May 31. It also has new language reflecting changes in minimization requirements in USA Freedom Act, and updated language to reflect the Second Circuit’s decision in a paragraph ordering that the government inform FISC if anything changes because of the pending circuit court decisions.
But the most interesting change has to do with the redactions.
The initial redaction (which lists all the providers) is not the same size — the new order, 15-75, has a wider redaction than the last order, 15-24, but the earlier order may be a line longer. But it is very close.
But the paragraph addressing custodians of records is clearly different. Here’s what that first few lines in that paragraph in 15-24 looks like:
Here’s what it looks like in 15-75.
The following paragraph, which addresses Verizon, appears to be the same.
There are two things that might explain the change in redaction. First, the providers may remain the same (understood to be AT&T and Sprint), but the official name used to refer to one may have changed — though I’m not aware of any changes at AT&T or Sprint that might explain that.
Or, they may have added another provider.
Mind you, I expect the government to add new providers once they move to the new querying technique in November, as the government will almost certainly be querying more newfangled kinds of “calls” and “texts” (to include VOIP and other Internet-based communications). So I think additional providers are inevitable.
Still, at least from the redactions of this order, it appears NSA may have already added a new provider.
USA F-ReDux Is Non-Exclusive, but the Second Circuit Might Be
I’m still trying to figure out WTF Mitch McConnell is doing with his Senate machinations over USA F-ReDux. Currently, he has both his short-term reauthorization and USA F-ReDux prepped for a vote, which probably means he’ll bring USA F-ReDux up for cloture or a vote, show that it doesn’t have enough support, and then use that to scaremonger the short-term reauthorization through as a way to wring more concessions out of the House.
Still, given what a dead-ender he is on a bill, USA F-ReDux, that gives the Intelligence Community so many goodies, I can’t help but wonder if there’s another explanation for his intransigence. I can think of one other possibility.
The House Judiciary Committee made it clear USA F-ReDux would be the exclusive means to obtain prospective Call Detail Records under Section 215:
This new mechanism is the only circumstance in which Congress contemplates the prospective, ongoing use of Section 501 of FISA in this manner.
But it made it equally clear it is not the exclusive means to obtain Call Detail Records. That’s because the report envisions conducting federated queries including “metadata [the government] already lawfully possess.”
The government may require the production of up to two ‘‘hops’’—i.e., the call detail records associated with the initial seed telephone number and call detail records (CDRs) associated with the CDRs identified in an initial ‘‘hop.’’ Subparagraph (F)(iii) provides that the government can obtain the first set of CDRs using the specific selection term approved by the FISC. In addition, the government can use the FISC-approved specific selection term to identify CDRs from metadata it already lawfully possesses. Together, the CDRs produced by the phone companies and those identified independently by the government constitute the first ‘‘hop.’’
I suggested here that that other “lawfully possessed metadata” probably consisted of data collected under EO 12333 (and permissible for chaining on US persons under SPCMA) and PRISM metadata.
But maybe that’s not all it includes. Maybe, the government has devise a way by which AT&T (or some other backbone provider) will still provide phone records in bulk on a daily basis? Maybe — as Richard Burr claimed before he later unclaimed — the government secretly maintains an IP dragnet under some other authority?
If that was the plan (though keep in mind, USA F-ReDux passed the House after the Second Circuit decision), then the Second Circuit may have ruined that effort. The ruling should limit all collection under a “relevant to” standard, not just that conducted under Section 215. And, as Faiza Patel argued, the decision should also affect collection where the government has dodged Fourth Amendment issues by focusing on “searches” rather than “seizures.”
[A]s Jennifer Daskal explained last Friday, “collection matters.” The Second Circuit rejected the government’s contention that there was no cognizable injury until plaintiffs’ phone records were actually analyzed and reviewed. It ruled that collection is properly analyzed as “seizure,” which if unlawful constitutes a separate injury from the “search” that takes place when records are analyzed either by a human being or a computer.
As the Supreme Court has recognized, in Fourth Amendment cases the analysis of standing is intertwined with the merits question of whether there has been an invasion of a protected privacy interest. Thus, the Second Circuit’s position on collection could have serious implications for other government programs beyond the standing question.
I’ve already suggested the decision might create problems for the virgin birth DOJ secretly gave to EO 12333 data used in SPCMA.
But who knows what else it applies to?
After all, USA F-ReDux was written so as to allow other dragnets (which is what EO 12333 is, after all). But the Second Circuit may pose problems for such dragnets that USA F-ReDux did not.
Going back to Richard Burr’s odd colloquy — which his office’s excuses simply cannot rationally explain — I think it (very remotely) possible the government is dragnetting IP addresses (perhaps for cybersecurity rather than counterterrorism purposes), but worries it has lost authority to do so with the Second Circuit decision. If so, it might be using this fight over counterterrorism data collection to lay congressional support for broader dragnet collection, to be able to sustain whatever other dragnets it has in place.
USA F-ReDux’s “Transparency” Provisions and Phone-PRISM
I’m going to make an unpopular argument.
Most observers of USA F-ReDux point to weakened transparency provisions as one of the biggest drawbacks of the latest version of the bill. They’re not wrong: transparency procedures are worse, remarkably so.
But given that I already thought they were not only inadequate but dangerously misleading,* I’m actually grateful to have had the Intelligence Community do another version of transparency provisions, which shows what they’re most intent on hiding and/or hints at what they will really be doing behind the carefully scripted words they’re getting Congress to rubber-stamp.
For comparison, I’ve put the bulk of the required transparency provisions for USA F-ReDux and Leahy’s USA Freedom below the rules below.
Hiding how 702 numbers will explode
The most remarkable of the changes in the transparency provision is that they basically took out this language requiring a top level count of Section 702 targets and persons whose communications were affected — this language.
(i) the number of targets of such orders;
(ii) the number of individuals whose communications were collected pursuant to such orders; [sub 500 range]
(iii) the number of individuals whose communications were collected pursuant to such orders who are reasonably believed to have been located in the United States at the time of collection; [sub 500 range]
This leaves — in addition to the “number of 702 orders” requirement — just this reporting requirement for back door content and metadata searches which (like the Leahy bill) exempts the gross majority of the back door searches, because they are done by the FBI.
(A) the number of search terms concerning a known United States person used to retrieve the unminimized contents of electronic communications or wire communications obtained through acquisitions authorized under such section, excluding the number of search terms used to prevent the return of information concerning a United States person; and [FBI Exemption]
(B) the number of queries concerning a known United States person of unminimized noncontents information relating to electronic communications or wire communications obtained through acquisitions authorized under such section, excluding the number of queries containing information used to prevent the return of information concerning a United States person; [FBI Exemption]
This is all the more remarkable given that ODNI has given us the topline number (though not the number of people sucked in) in each of its last two transparency reports.
In other words, ODNI was happy to tell us that the number of FISA 702 targets went up by 4% between 2013 and 2014, but not how much those numbers of targets will go up in 2015, when they presumably begin to roll out the new call chaining provision.
I suspect — and these are well educated but nevertheless wildarseguesses — there are several reasons.
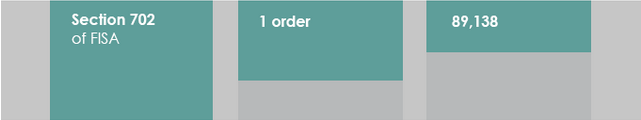
The number of unique identifiers collected under 702 is astronomical
First, the reporting provisions as a whole move from tracking “individuals whose communications were collected” to “unique identifiers used to communicate information.” They probably did that because they don’t really have a handle on which of the identifiers all represent the same natural person (and some aren’t natural persons), and don’t plan on ever getting a handle on that number. Under last year’s bill, ONDI could certify to Congress that he couldn’t count that number (and then as an interim measure I understand they were going to let them do that, but require a deadline on when they would be able to count it). Now, they’ve eliminated such certification for all but 702 metadata back door searches (that certification will apply exclusively to CIA, since FBI is exempted). In other words, part of this is just an admission that ODNI does not know and does not planning on knowing how many of the identifiers they target actually fit together to individual targets.
But since they’re breaking things out into identifiers now, I suspect they’re unwilling to give that number because for each of the 93,000 targets they’re currently collecting on, they’re probably collecting on at least 10 unique identifiers and probably usually far, far more.
Just as an example (this is an inapt case because Hassanshahi, as a US person, could not be a PRISM target, but it does show the bare minimum of what a PRISM target would get), the two reports Google provided in response to administrative subpoenas for information on Shantia Hassanshahi, the guy caught using the DEA phone dragnet (these were subpoenas almost certainly used to parallel construct data obtained from the DEA phone dragnet and PRISM targeted at the Iranian, “Sheikhi,” they found him through), included:
- a primary gmail account
- two secondary gmail accounts
- a second name tied to one of those gmail accounts
- a backup email (Yahoo) address
- a backup phone (unknown provider) account
- Google phone number
- Google SMS number
- a primary login IP
- 4 other IP logins they were tracking
- 3 credit card accounts
- Respectively 40, 5, and 11 Google services tied to the primary and two secondary Google accounts, much of which would be treated as separate, correlated identifiers
So just for this person who might be targeted under the new phone dragnet (though they’d have to play the same game of treating Iran as a terrorist organization that they currently do, but I assume they will), you’d have upwards of 15 unique identifiers obtained just from Google. And that doesn’t include a single cookie, which I’ve seen other subpoenas to Google return.
In other words, one likely reason the IC has decided, now that they’re going to report in terms of unique identifiers, they can’t report the number of identifiers targeted under PRISM is because it would make it clear that those 93,000 targets represent, very conservatively, over a million identifiers — and once you add in cookies, maybe a billion identifiers — targeted. And reporting that would make it clear what kind of identifier soup the IC is swimming in.
Hiding new PRISM providers
There is another reason I think they’ve grown reluctant to show much transparency under 702. Implementing the USA F-ReDux system — in which each provider sets up facilities they can use to chain on non-call detail record session identifying information — means more providers (smaller phone companies, and some new Internet providers, for example) will have what amount to PRISM-lite portals that can also be used for PRISM production. If you build it they will come!
In addition, Verizon and Sprint may be providing more PRISM smart phone materials in addition to upstream collection (AT&T likely already provides a lot of this because that’s how they roll).
So I suspect that, whereas now there’s a gap between the cumulative numbers providers report in their own transparency reports and what we see from ODNI, that number will grow notably, which would lead to questions about where the additional 702 production was coming from. (Until Amazon starts producing transparency reports, though, I’ll just assume they’re providing it all).
Hiding the smart-phone-PRISM
Finally, I think that once USA F-ReDux rolls out, the government (read, FBI, where this data will first be sucked in) will have difficulty distinguishing between the 702 and 215 production from a number of providers — probably AT&T, Verizon, Apple, Google, and Microsoft, but that’s just a guess.
Going back to the case of Hassanshahi, for example (and assuming, as I do, that the government has been parallel constructing the fact that they also targeted the Iranian Sheikhi identifier under PRISM, which would have immediately led them to his GMail account, as they very very easily could), the Tehran phone to Google call between Sheikhi and Hassanshahi would likely come in via at least 3 sources: Sheihki PRISM collection, Google USA F-ReDux returns on the Sheikhi number, and AT&T backbone USA F-ReDux returns on the Sheikhi number. And all that’s before you’ve taken a single hop into Hassanshahi’s accounts.
In other words, what you’re actually getting with USA F-ReDux is a way to get to the metadata of US persons identified via incidental collection under PRISM (again, this should just before for targets of a somewhat loosey goosey definition of terrorism targets). It’s basically a way to get a metadata “hop” off of all the Americans already “incidentally” collected under PRISM (note, permission to do this for targets identified under a probable cause warrant is already written into every phone dragnet order; this just extends that, with FISC review, to PRISM targets). And for the big providers that have anything that might be considered “call” service, the portals from which that will derive will likely be very very closely related.
The Government Changed Its Mind about How Many Databases It Searched in the Hassanshahi Case after It Shut Down the DEA Dragnet
As I noted in this post, the government insists that it did not engage in parallel construction in the case of Shantia Hassanshahi, the Iranian-American busted for sanctions violations using evidence derivative of a search of what the government now claims was a DEA dragnet. “While it would not be improper for a law enforcement agency to take steps to protect the confidentiality of a law enforcement sensitive investigative technique, this case raises no such issue.”
The claim is almost certainly bullshit, true in only the narrowest sense.
Indeed, the changing story the government has offered about how they IDed Hassanshahi based off a single call he had with a phone belonging to a person of interest, “Sheikhi,” in Iran, is instructive not just against the background of the slow reveal of multiple dragnets over the same period. But also for the technological capabilities included in those claims. Basically, the government appears to be claiming they got a VOIP call from a telephony database.
As I lay out below, the story told by the government in various affidavits and declarations (curiously, the version of the first one that appears in the docket is not signed) changed in multiple ways. While there were other changes, the changes I’m most interested in pertain to:
- Whether Homeland Security Investigator Joshua Akronowitz searched just one database — the DEA toll record database — or multiple databases
- How Akronowitz identified Google as the provider for Hassanshahi’s phone record
- When and how Akronowitz became interested in a call to Hassanshahi from another Iranian number
- How many calls of interest there were
As you can see from the excerpts below, Akronowitz at first claimed to have searched “HSI-accessible law enforcement databases,” plural, and suggested he searched them himself. In July 2014, in response to a motion to suppress (and after Edward Snowden had disclosed the NSA’s phone dragnet), Akronowitz changed that story and said he sent a research request to a single database, implying someone else did a search of just one database. Akronowitz told the same story in yet another revised affidavit submitted last October. In the declaration submitted in December but unsealed in January, DEA Assistant Special Agent Robert Patterson stuck with the single database story and used the passive voice to hide who did the database query.
While Akronowitz’ story didn’t change regarding how he discovered that Hassanshahi’s phone was a Google number, it did get more detailed in the July 2014 affidavit, which explained that he had first checked with another VOIP provider before being referred to Google.
Perhaps most interestingly, the government’s story changed regarding how many calls of interest there were, and between what numbers. In January 2013, Akronowitz said “a number of telephone calls between ‘Sheikhi’s’ known business telephone number and telephone number 818-971-9512 had occurred within a relatively narrow time frame” (though he doesn’t tell us what that time frame was). He also says that his Google subpoena showed “numerous calls to the same Iranian-based telephone number during a relatively finite period of time.” He neither explained that this number was not Sheikhi’s number — it was a different Iranian number — nor what he means by “a relatively finite period of time.” His July and October affidavits said his research showed a contact, “on one occasion, that is, on July 4, 2011,” with Sheikhi’s number. The July affidavit maintained the claim that there were multiple calls between Hassanshahi’s number and an Iranian one: “numerous phone calls between Hassanshahi’s ‘818’ number and one Iranian phone number.” But by October, Akronowitz conceded that the Google records showed only “that Hassanshahi’s ‘818’ number made contact with an Iranian phone number (982144406457) only once, on October 5, 2011” (as well as a “22932293” number that he bizarrely claimed was a call to Iran). Note, Akronowitz’ currently operative story would mean the government never checked whether there were any calls between Hassanshahi and Sheikhi between August 24 and September 6 (or after October 6), which would be rather remarkable. Patterson’s December affidavit provided no details about the date of the single call discovered using what he identified as DEA’s database, but did specify that the call was made by Hassanshahi’s phone, outbound to Iran. (Patterson didn’t address the later Google production, as that was pursuant to a subpoena.)
To sum up, before Edward Snowden’s leaks alerted us to the scope of NSA’s domestic and international dragnet, Akronowitz claimed he personally had searched multiple databases and found evidence of multiple calls between Hassanshahi’s phone number and Sheikhi’s number, as well as (after getting a month of call records from Google) multiple calls to another Iranian number over unspecified periods of time. After Snowden’s leaks alerted us to the dragnet, after Dianne Feinstein made it clear the NSA can search on Iranian targets in the Section 215 database, which somehow counts as a terrorist purpose, and after Eric Holder decided to shut down just the DEA dragnet, Akronowitz changed his story to claim he had found just one call between Hassanshahi and Shiekhi, and — after a few more months — just one call from another Iranian number to Hassanshahi. Then, two months later, the government claimed that the only database that ever got searched was the DEA one (the one that had already been shut down) which — Patterson told us — was based on records obtained from “United States telecommunications service providers” via a subpoena.
Before I go on, consider that the government currently claims it used just a single phone call of interest — and the absence of any additional calls in a later months’s worth of call records collected that fall — to conduct a warrantless search of a laptop in a state (CA) where such searches require warrants, after having previously claimed there was a potentially more interesting set of call records to base that search on.
Aside from the government’s currently operative claim that it would conduct border searches based on the metadata tied to a single phone call, I find all this interesting for two reasons.
First, the government’s story about how many databases got searched and how many calls got found changed in such a way that the only admission of an unconstitutional search to the judge, in December 2014, involved a database that had allegedly been shut down 15 months earlier.
Maybe they’re telling the truth. Or maybe Akronowitz searched or had searched multiple databases — as he first claimed — and found the multiple calls he originally claimed, but then revised his story to match what could have been found in the DEA database. We don’t know, for example, if the DEA database permits “hops,” but he might have found a more interesting call pattern had he been able to examine hops (for example, it might explain his interest in the other phone number in Iran, which otherwise would reflect no more than an immigrant receiving a call from his home country).
All of this is made more interesting because of my second point: the US side of the call in question was an Internet call, a Google call, not a telephony call. Indeed, at least according to Patterson’s declaration (records of this call weren’t turned over in discovery, as far as I can tell), Hassanshahi placed the call, not Sheikhi.
I have no idea how Google calls get routed, but given that Hassanshahi placed the call, there’s a high likelihood that it didn’t cross a telecom provider’s backbone in this country (and god only knows how DEA or NSA would collect Iranian telephony provider records), which is who Patterson suggests the calls came from (though there’s some room for ambiguity in his use of the term “telecommunications service providers”).
USAT’s story on this dragnet suggests the data all comes from telephone companies.
It allowed agents to link the call records its agents gathered domestically with calling data the DEA and intelligence agencies had acquired outside the USA. (In some cases, officials said the DEA paid employees of foreign telecom firms for copies of call logs and subscriber lists.)
[snip]
Instead of simply asking phone companies for records about calls made by people suspected of drug crimes, the Justice Department began ordering telephone companies to turn over lists of all phone calls from the USA to countries where the government determined drug traffickers operated, current and former officials said.
[snip]
Former officials said the operation included records from AT&T and other telecom companies.
But if this call really was placed from a Google number, it’s not clear it would come up under such production, even under production of calls that pass through telephone companies’ backbones. That may reflect — if the claims in this case are remotely honest — that the DEA dragnet, at least, gathered call records not just from telecom companies, but also from Internet companies (remember, too, that DOJ’s Inspector General has suggested DEA had or has more than one dragnet, so it may also have been collecting Internet toll records).
And that — coupled with the government’s evolving claims about how many databases got checked and how many calls that research reflected — may suggest something else. Given that the redactions on the providers obliged under the Section 215 phone dragnet orders haven’t changed going back to 2009, when it was fairly clear there were just 3 providers (AT&T, Sprint, and Verizon), it may be safe to assume that’s still all NSA collects from. A never-ending series of leaks have pointed out that the 215 phone dragnet increasingly has gaps in coverage. And this Google call would be precisely the kind of call we would expect it to miss (indeed, that’s consistent with what Verizon Associate General Counsel — and former DOJ National Security Division and FBI Counsel — Michael Woods testified to before the SSCI last year, strongly suggesting the 215 dragnet missed VOIP). So while FISC has approved use of the “terrorist” Section 215 database for the terrorist group, “Iran,” (meaning NSA might actually have been able to query on Sheikhi), we should expect that this call would not be in that database. Mind you, we should also expect NSA’s EO 12333 dragnet — which permits contact chaining on US persons under SPCMA — to include VOIP calls, even with Iran. But depending on what databases someone consulted, we would expect gaps in precisely the places where the government’s story has changed since it decided it had searched only the now-defunct DEA database.
Finally, note that if the government was sufficiently interested in Sheikhi, it could easily have targeted him under PRISM (he did have a GMail account), which would have made any metadata tied to any of his Google identities broadly shareable within the government (though DHS Inspectors would likely have to go through another agency, quite possibly the CIA). PRISM production should return any Internet phone calls (though there’s nothing in the public record to indicate Sheikhi had an Internet phone number). Indeed, the way the NSA’s larger dragnets work, a search on Sheikhi would chain on all his correlated identifiers, including any communications via another number or Internet identifier, and so would chain on whatever collection they had from his GMail address and any other Google services he used (and the USAT described the DEA dragnet as using similarly automated techniques). In other words, when Akronowitz originally said there had been multiple “telephone calls,” he may have instead meant that Sheikhi and Hassanshahi had communicated, via a variety of different identifiers, multiple times as reflected in his search (and given what we know about DEA’s phone dragnet and my suspicion they also had an Internet dragnet, that might have come up just on the DEA dragnets alone).
The point is that each of these dragnets will have slightly different strengths and weaknesses. Given Akronowitz’ original claims, it sounds like he may have consulted dragnets with slightly better coverage than just the DEA phone dragnet — either including a correlated DEA Internet dragnet or a more extensive NSA one — but the government now claims that it only consulted the DEA dragnet and consequently claims it only found one call, a call it should have almost no reason to have an interest in.