2:24
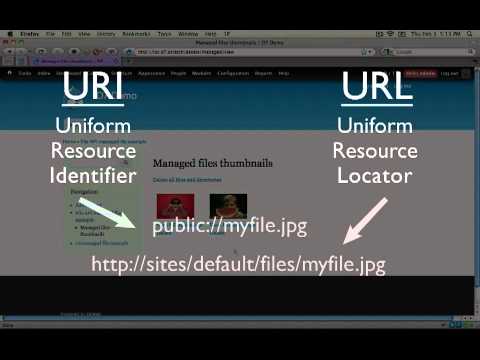
What the difference is between a URI and a URL (a Drupal how-to)
This is one of over 24 videos in a 2-hour series on http://buildamodule.com called "Workin...
published: 10 Jul 2011
author: BuildAModule
What the difference is between a URI and a URL (a Drupal how-to)
What the difference is between a URI and a URL (a Drupal how-to)
This is one of over 24 videos in a 2-hour series on http://buildamodule.com called "Working with Files and the File API". In this 2+ hour collection, we cove...- published: 10 Jul 2011
- views: 2261
- author: BuildAModule
8:47

Internet- und WWW-Technologien, URI - Uniform Resource Identifier
Den kompletten Kurs finden Sie auf: http://http://www.tele-task.de/archive/series/overview...
published: 03 Jan 2014
Internet- und WWW-Technologien, URI - Uniform Resource Identifier
Internet- und WWW-Technologien, URI - Uniform Resource Identifier
Den kompletten Kurs finden Sie auf: http://http://www.tele-task.de/archive/series/overview/943/- published: 03 Jan 2014
- views: 1
10:59
Phishing with Data URI
"The data URI scheme is a URI scheme (Uniform Resource Identifier scheme) that provides a ...
published: 07 Oct 2012
author: Ajin Abraham
Phishing with Data URI
Phishing with Data URI
"The data URI scheme is a URI scheme (Uniform Resource Identifier scheme) that provides a way to include data in-line in web pages as if they were external r...- published: 07 Oct 2012
- views: 1220
- author: Ajin Abraham
11:07

Uniform resource locator
The uniform resource locator, abbreviated as URL (also known as web address, particularly ...
published: 15 Jul 2014
Uniform resource locator
Uniform resource locator
The uniform resource locator, abbreviated as URL (also known as web address, particularly when used with HTTP), is a specific character string that constitutes a reference to a resource. In most web browsers, the URL of a web page is displayed on top inside an address bar. An example of a typical URL would be "http://en.example.org/wiki/Main_Page". A URL is technically a type of uniform resource identifier (URI), but in many technical documents and verbal discussions, URL is often used as a synonym for URI, and this is not considered a problem. URLs are commonly used for web pages (http), but can also be used for file transfer (ftp), email (mailto) and many other applications (see URI scheme for list). URLs are specified in RFC 3986 (2005), and in a WHATWG URL Living Standard. This video is targeted to blind users. Attribution: Article text available under CC-BY-SA Creative Commons image source in video- published: 15 Jul 2014
- views: 0
5:10
wordpress 2 .7 Step 2: Picking a URL / Your website name
http://www.upstartsolutions.net Uniform Resource Locator (URL) is a type of Uniform Resour...
published: 07 Jan 2009
author: Anthony Blando
wordpress 2 .7 Step 2: Picking a URL / Your website name
wordpress 2 .7 Step 2: Picking a URL / Your website name
http://www.upstartsolutions.net Uniform Resource Locator (URL) is a type of Uniform Resource Identifier (URI) that specifies where an identified resource is ...- published: 07 Jan 2009
- views: 1467
- author: Anthony Blando
9:39

12 How to Name Your Web Pages for SEO
12 How to Name Your Web Pages for SEO video tutorial lesson outlines ways for naming your ...
published: 24 Apr 2014
12 How to Name Your Web Pages for SEO
12 How to Name Your Web Pages for SEO
12 How to Name Your Web Pages for SEO video tutorial lesson outlines ways for naming your landing pages for Google. Created by http://goo.gl/5RfrTn rankya seo services this video details information for naming your URI (uniform resource identifier) to send all the right signals to Google. Google's Webmaster Design and Content Guidelines clearly suggest to "Think about the words users would type to find your pages, and make sure that your site actually includes those words within it" and by adhering to these guidelines, we can understand that URL is also a part of your landing page. To learn more about Google's guidelines visit: https://support.google.com/webmasters/answer/35769 One of the most important relevance determination methods Google relies on is the naming structure of your landing page. If your landing pages are about "Methods for Including Keywords in the URL" then logically you would name it something along these lines: keywords-and-your-url.html as your web page name. It is only logical that you name your landing pages according to the content you are presenting your visitors. If you believe that by watching this video you have gained additional knowledge about search engine optimization and naming your web pages, then I would greatly appreciate it if you shared it on your social profiles so that other web site owners can also benefit from. The share URL is: http://youtu.be/_tjqwflKCMk This video tutorial session has been created by #rankyaseoservices for YouTube community and webmasters who want to learn more about creating user friendly websites and ranking in Google search engine organic ranking results. Looking forward to your subscription which you can do that by visiting this internet address: https://www.youtube.com/user/rankyaseoservices- published: 24 Apr 2014
- views: 40
20:15

Cisco Unified Communications Manager 9.x New Features Lab - URI Dialing - (4 of 6)
This video is 4 of 6 show some of the new features of Cisco Unified Communications Manager...
published: 07 Dec 2012
author: Paul Stryer
Cisco Unified Communications Manager 9.x New Features Lab - URI Dialing - (4 of 6)
Cisco Unified Communications Manager 9.x New Features Lab - URI Dialing - (4 of 6)
This video is 4 of 6 show some of the new features of Cisco Unified Communications Manager 9.x CUCM URI Registration and Dialing URI stands for "Uniform Reso...- published: 07 Dec 2012
- views: 375
- author: Paul Stryer
10:15

Uniform resource locator
This is a synthesized speech reading of the Wikipedia article "Uniform resource locator" a...
published: 13 Feb 2014
Uniform resource locator
Uniform resource locator
This is a synthesized speech reading of the Wikipedia article "Uniform resource locator" and is intended primarily for blind and visually impaired individuals who can not view Wikipedia. This video can also be used for mobile users who wish to listen to Wikipedia articles on the go, or by those who wish to learn a second language by reading the captions in that language while listening in English. Original article available at: http://en.wikipedia.org/wiki/Uniform_resource_locator All text from Wikipedia is licensed under CC-BY-SA: https://en.wikipedia.org/wiki/Wikipedia:Reusing_Wikipedia_content "You are free ... to make commercial use of the work": http://creativecommons.org/licenses/by-sa/3.0/ Text-to-speech synthesized from FestVox, which permits commercial use: "no restrictions on its use (commercial or otherwise)" http://festvox.org/festival/downloads.html Image from http://wikipedia.org/wiki/File:URI_Euler_Diagram_no_lone_URIs.svg is licensed under CC-BY-SA: https://creativecommons.org/licenses/by-sa/3.0/deed.en Note: all these licenses permit commercial use, and therefore we are permitted to monetize videos derived from these contents.- published: 13 Feb 2014
- views: 0
9:20

07 How to Analyze Competitor's Backlinks
07 How to analyze competitor's backlinks for free outlines strategies for competitor backl...
published: 24 Apr 2014
07 How to Analyze Competitor's Backlinks
07 How to Analyze Competitor's Backlinks
07 How to analyze competitor's backlinks for free outlines strategies for competitor backlink analysis. Created by http://goo.gl/V8gG4y SEO consultant expert this video lesson shows you methods for seeing where your competitors are getting backlinks for their website. You can use Google search to find the online footprint of your competitors, for example, you can conduct advanced search queries such as the "link:" operator to see what Google will show for backlink data for your competition's website. Having said that please keep in mind that Google does not reveal all the backlink data it has on any given URL. That is why there are many backlink analysis websites and platforms and almost all of them claim to have the most detailed data sets concerning the hyperlinks pointing back to a particular website. I can confidently tell you that the freely available backlink data gathering on your competitors can be done through: http://siteexplorer.info/ http://backlinkwatch.com/ If you have benefited from this particular video session on analysing competitor's backlinks for free then we encourage you to share it using this uniform resource identifier: http://youtu.be/CfkkymzKFLM When it comes to backlink data analysis, these freely available website's usually give you more in-depth and actionable insights than other paid backlink data research providers on internet. Keep in mind also that, you can construct Google advanced search query syntax to find almost all of the information you will ever need on your competitors. To learn about many different ways of search Google visit: http://goo.gl/t6rHeb Originally uploaded by #rankyaseoservices for loyal fans, subscribers and new visitors, you can find all the other SEO related videos here at: https://www.youtube.com/user/rankyaseoservices/videos Thank you for learning with me, thank you for subscribing, wishing you first page Google rankings;- published: 24 Apr 2014
- views: 67
1:54

Building a Mobile Augmented Reality Application in HTML5
This video presents research performed by Sangchul Ahn, Byounghyun Yoo, Heedong Ko at Imag...
published: 14 Oct 2013
Building a Mobile Augmented Reality Application in HTML5
Building a Mobile Augmented Reality Application in HTML5
This video presents research performed by Sangchul Ahn, Byounghyun Yoo, Heedong Ko at Imaging Media Research Center of Korea Institute of Science and Technology (http://www.imrc.kist.re.kr/), and Steven Feiner at Columbia University's Computer Graphics and User Interfaces Lab (http://graphics.cs.columbia.edu/top.html). Insight is a mobile AR Web browser that executes HTML5-based AR applications. By extending physical objects and places with Uniform Resource Identifier (URI), we could build objects of interest for mobile AR application as DOM (Document Object Model) elements and control their behavior and user interactions through DOM events in standard HTML documents. A new CSS media type, which is named as PLACE media, is defined to augment virtual objects to the physical objects. In this model, we introduce the concept of PLACE, which is the model of physical space in which the user can be located. With this approach, mobile AR applications can be developed as common HTML documents seamlessly under current Web eco-system.- published: 14 Oct 2013
- views: 13
4:53

HTTPA protocol for tracking How private data is used online.
By now, most people feel comfortable conducting online financial transactions on the Web. ...
published: 17 Jun 2014
HTTPA protocol for tracking How private data is used online.
HTTPA protocol for tracking How private data is used online.
By now, most people feel comfortable conducting online financial transactions on the Web. The cryptographic schemes that protect online banking and credit card purchases have proven their reliability over decades. But right now, there is no effective way to prevent misuse of your data by the people authorized to access it, say for example a bank employee can still access your data, and frequently we are reading news about misuse of the data by the bank employees. i-e Once you share your data with the bank, Healthcare system or any other private company, for your online transactions, you don't have any control over who exactly is using or misusing your data. This situation will change soon, as MIT researchers (Oshani Seneviratne) are now developing a new web technology to address this issue. Their approach is based on "Enabling Privacy Through Transparency". They named their new web technology as HTTPA Protocol. HTTPA stands for Hyper Text Transfer Protocol with Accountability. i-e HTTP with Accountability. HTTPA will automatically monitor the transmission of private data and allow the data owner to examine how it is being used. For example, a HIV or AIDS patient might be interested in knowing if his medical conditions was only used in connection with his treatment purposes, and not for other purposes such as employment or insurance purposes. With the help of this new technology, he will be able to know list of people who accessed his medical records, just by clicking a button. The HTTPA Protocol will be demonstrated at the IEEE's Conference on Privacy, Security and Trust in July and the prinicipal research scientists will also present a sample application involving a health-care records system. With HTTPA, each item of private data would be assigned its own uniform resource identifier. i-e URI, a key component of the Semantic Web. Remote access to a Web server would be controlled much the way it is now, i-e through passwords and encryption. But every time the server transmitted a piece of sensitive data, it would also send a description of the restrictions on the data's use. And it would log the transaction, using only the URI, somewhere in a network of encrypted, special-purpose servers. HTTPA would be voluntary: It would be up to software developers to adhere to its specifications when designing their systems. But HTTPA compliance could become a selling point for companies offering services that handle private data. It's not that difficult to transform an existing website into an HTTPA-aware website. On every HTTP request, the server should say, 'OK, here are the usage restrictions for this resource, and log the transaction in the network of special-purpose servers. When the data owner requests an audit, the servers work through the chain of derivations, identifying all the people who have accessed the data, and what they've done with it. Currently the researchers use a technology known as distributed hash tables — the technology at the heart of peer-to-peer networks like BitTorrent — to distribute the transaction logs among the servers. Redundant storage of the same data on multiple servers serves two purposes: First, it ensures that if some servers go down, data will remain accessible. And second, it provides a way to determine whether anyone has tried to tamper with the transaction logs for a particular data item — such as to delete the record. Source: http://newsoffice.mit.edu/2014/whos-using-your-data-httpa-0613 Subscribe to our YouTube channel at http://www.youtube.com/subscription_center?add_user=qualitypointtech See more Technology News at https://www.youtube.com/playlist?list=PLK2ccNIJVPpB_XqWWq_oaZGIDzmKiSkYc- published: 17 Jun 2014
- views: 67
2:00

How to add a Spotify player | Wix.com
Add and customize a Spotify play button on your site within minutes. The Spotify play but...
published: 27 Apr 2014
How to add a Spotify player | Wix.com
How to add a Spotify player | Wix.com
Add and customize a Spotify play button on your site within minutes. The Spotify play button allows you to add a playlist for your site visitors to listen to while visiting your site. Learn more about this or any of our other features by visiting the Wix support center center at: http://www.wix.com/support/main/html5- published: 27 Apr 2014
- views: 143
5:03

January Lookbook 2012 | 20 Looks | 20 Styling Tips | 5 Mins.
Music by: Olebaster from Artis Illocanblo Peony Lantern (Split EP) MUSIC LICENSE AGREEMENT...
published: 02 Feb 2012
author: Urbanicon82
January Lookbook 2012 | 20 Looks | 20 Styling Tips | 5 Mins.
January Lookbook 2012 | 20 Looks | 20 Styling Tips | 5 Mins.
Music by: Olebaster from Artis Illocanblo Peony Lantern (Split EP) MUSIC LICENSE AGREEMENThttp://creativecommons.org/licenses/by-nc-sa/3.0/us/legalcode "You ...- published: 02 Feb 2012
- views: 5369
- author: Urbanicon82
5:06

HotSpot Episode 67: How Your Private Data Is Used Online
Recently, NASA beamed a high-definition video message, "Hello, World!", 260 miles from the...
published: 16 Jun 2014
HotSpot Episode 67: How Your Private Data Is Used Online
HotSpot Episode 67: How Your Private Data Is Used Online
Recently, NASA beamed a high-definition video message, "Hello, World!", 260 miles from the International Space Station to Earth using a new laser communications instrument. The message was the first 175-megabit communication for the Optical Payload for Lasercomm Science (OPALS), a technology demonstration that allows NASA to test methods for communication with future spacecraft using higher bandwidth than radio waves. According to NASA, optical communication tools like OPALS use focused laser energy to reach data rates between 10 and 1,000 times higher than current space communications, which rely on radio portions of the electromagnetic spectrum. Because the space station orbits Earth at 17,500 mph, transmitting data from the space station to Earth requires extremely precise targeting. The process can be equated to a person aiming a laser pointer at the end of a human hair 30 feet away and keeping it there while walking. Shatterproof Smartphone Screens Dropping a cell phone can be a pretty traumatic experience. As soon as it hits the ground, you already know you're most likely going to have a shattered screen once you pick it up. Well, researchers at the University of Akron have developed a transparent electrode that could change the face of smartphones, literally, by making their displays shatterproof. In a recently published scientific paper, researchers demonstrated how a transparent layer of electrodes on a polymer surface could be extraordinarily tough and flexible, withstanding repeated scotch tape peeling and bending tests. HTTP with Accountability Researchers in the Decentralized Information Group (DIG) at MIT's Computer Science and Artificial Intelligence Laboratory (CSAIL) are developing a new web technology that would allow you to track how your private data is used online. The new protocol, "HTTP with Accountability," or HTTPA, will automatically monitor the transmission of private data and allow the data owner to examine how it's being used. According to MIT, with HTTPA, each item of private data would be assigned its own uniform resource identifier (URI), a key component of the Semantic Web, a new set of technologies, championed by W3C, which would convert the Web from a collection of searchable text files into a giant database. Remote access to a Web server would be controlled much the way it is now, through passwords and encryption. But every time the server transmitted a piece of sensitive data, it would also send a description of the restrictions on the data's use. And it would log the transaction, using only the URI, somewhere in a network of encrypted, special-purpose servers. NFC: The Critical Link Last week I visited Schaumburg, IL to learn more about NFC technology from NXP Semiconductors. During the tech day, I learned about smart devices and how they really work, security issues that NFC helps to prevent, how to control counterfeit products, and where the market is headed. I also downloaded a few apps, and learned how to program a few tags that NXP provided during the demonstration. According to NXP, as more things get connected, concerns over data privacy and security will emerge. Utilizing NFC as a communication method can help address some of these concerns, because it is specifically designed and engineered to provide zero power operation and maximize privacy at a very affordable price. To learn more about NXP and how NFC is the critical link for the Internet of Things, go to www.nxp.com. Do you have story ideas? Comment below or email wdd_web@advantagemedia.com we'll cover them in an upcoming episode.- published: 16 Jun 2014
- views: 15
Youtube results:
4:47

2.2 Uniform Resource Locator
URL....
published: 08 Oct 2012
author: ahangarzadehsdcoe
2.2 Uniform Resource Locator
2:10

"The Island" Teaser Trailer [Minecraft Cinematic] [Cancelled]
UPDATE* - Due to lack of time and motivation i do not intend to finish "The Island" movie....
published: 21 Apr 2012
author: xNextGenGamersx
"The Island" Teaser Trailer [Minecraft Cinematic] [Cancelled]
"The Island" Teaser Trailer [Minecraft Cinematic] [Cancelled]
UPDATE* - Due to lack of time and motivation i do not intend to finish "The Island" movie. Trailer of an extraordinary map i found online and made a video a...- published: 21 Apr 2012
- views: 355
- author: xNextGenGamersx
4:29

S2Member Content Restrictions
Create a Membership Website with WordPress - S2Member Content Restrictions
Now that the p...
published: 09 Feb 2014
S2Member Content Restrictions
S2Member Content Restrictions
Create a Membership Website with WordPress - S2Member Content Restrictions Now that the parameters are set for the membership site the content can be protected. The way you protect content will depend on your site focus. S2Member installs a meta box on each page and post screen. The membership level is selected from this drop-down. And it also has a place for custom capabilities. This is the place for the memb and ecomm tags we setup in a previous video. S2Members also has the ability to protect content for each level in various ways. To set content restrictions navigate to the S2Member Restriction Options page. Content can be protected by Post by entering the post ID in a comma-delimited format. The post ID's can be found on the All Posts Table under the ID column that the WP Show ID plugin installed. This is the plugin we installed in a previous video. Also, if you are using Custom Post Types they can be protected by entering the word ALL followed by a dash and then the custom post type. all-movies would protect all the movie custom post types, for instance. Page restriction is handled in the same way as the post restriction with the Page ID. Enter the ID under the level separated with a comma. Tags are different, tags use the name of the tag. And with the Page Tagger plugin we installed in a previous video, all the pages, along with posts, can be tagged to use the tag restriction. Category Restriction is handled like the post and page restrictions with the Category ID listed under the level. Category ID's can be found on the Posts Category screen. And URI restriction can be used to protect entire sections of a site by using the URI or Uniform Resource Identifier. This is the part of a URL after the dot extension in the site domain name. This is typically used when there's a plugin like BuddyPress is installed. And a specific Post or Page restriction that can be used to sell access to a specific post or page. This can be sold to anyone, even non-members. This is a file that is not protected by any membership levels. It is a specific post or page like an e-book that you want to sell to members and non-members alike. One of the restrictions we'll set in place is the Alternative View Protection. Alternative View Protection filters WordPress database queries. WordPress searches, content excerpts from XML feeds, archive views and even comment feeds. This is an added layer of protection for the site. You can select what is appropriate for your site. For the course we'll use the Filter All WordPress Queries so we can have this added protection. Select the box and then click the save all changes button. Two others forms of restriction that you should be aware of are the Brute Force IP/Login Restriction and the Unique IP Access Restrictions. These are both on by default but can be adjusted or even turned off. Brute Force is when someone tries to guess the username and password by trying different combinations. Brute Force restriction limits the number of attempts or failed logins within a set time period. If this number is exceeded then a ban is placed on that person for 30 minutes. You can adjust this to fit your site by selecting from the drop-down. This feature can be disabled by selecting the Allow Infinite Failed Logins. And it can be reset by clicking the Reset Brute Force Logs. And the Unique IP Access Restrictions works to prevent a member from sharing their username and password with a non-member by monitoring the entry points to the membership site. If a member exceeds the Maximum Unique IP Address set then they will be temporarily banned. Select the Number of unique ID's allowed and then select the banned time period. This feature can be disabled by selecting the Allow Infinite IP's. And it can be rest by Clicking the Reset IP Restrictions Logs button. Remember to click the save all changes button at the bottom of the screen to activate any changes. As your site grows and matures these restrictions can be revised to make your site flexible and user friendly.- published: 09 Feb 2014
- views: 7
1:09

次回も同じ状態で開く 「Windows Vista高速化解説」
http://windows-vista-kousokuka.jp/1-32/index.html 複数開いているホームページをまとめて保存し、必要なときに復帰できるようにしておく...
published: 21 Sep 2012
author: iphoneorjp
次回も同じ状態で開く 「Windows Vista高速化解説」
次回も同じ状態で開く 「Windows Vista高速化解説」
http://windows-vista-kousokuka.jp/1-32/index.html 複数開いているホームページをまとめて保存し、必要なときに復帰できるようにしておく 使用方法 1、 「お気に入りに追加」ボタンをクリックします 2、 「タググループをお気に入りに追加」をクリック 3、 グループ名を決...- published: 21 Sep 2012
- views: 43
- author: iphoneorjp







