2:43

Endpoint - Black Skies
Endpoint - Black Skies @ The Brewery Thunderdome - 12/30/94...
published: 31 Dec 2007
author: flexyournoggin
Endpoint - Black Skies
Endpoint - Black Skies @ The Brewery Thunderdome - 12/30/94
5:15

Endpoint - Intro/Caste
Endpoint - Intro/Caste - 12/30/94 - The Brewery Thunderdome in Louisville, KY. I got this ...
published: 30 Dec 2007
author: flexyournoggin
Endpoint - Intro/Caste
Endpoint - Intro/Caste - 12/30/94 - The Brewery Thunderdome in Louisville, KY. I got this video 3rd/4th hand and do not know who recorded it. If you know (or if it was you, please get in touch)
2:03

Ryu ga Gotoku 3 OST - 16 - End Point
Track 16 - End Point...
published: 29 May 2009
author: Snake2061986
Ryu ga Gotoku 3 OST - 16 - End Point
Track 16 - End Point
4:31

What is Endpoint Security? CoSoSys Information
www.cososys.com What is Endpoint Security? Data Loss, Data Leakage, Data Theft are all con...
published: 22 Mar 2008
author: CoSoSys
What is Endpoint Security? CoSoSys Information
www.cososys.com What is Endpoint Security? Data Loss, Data Leakage, Data Theft are all concerns of Endpoint Security. What is Data Loss Prevention? This video is a short info about Endpoint Security and what you can do to conquer Endpoint Security Threats.
3:06

The Best of IBM Tivoli Endpoint Manager
www.ibm.com IBM Tivoli® Endpoint Manager...
published: 04 Feb 2011
author: ibmservicemanagement
The Best of IBM Tivoli Endpoint Manager
www.ibm.com IBM Tivoli® Endpoint Manager
8:07

What are endpoints, address, contracts and bindings?
This video will discuss about endpoints, address, contracts and bindings in WCF. For more ...
published: 06 Oct 2009
author: dnfvideo
What are endpoints, address, contracts and bindings?
This video will discuss about endpoints, address, contracts and bindings in WCF. For more free articles, interview questions and video tutorials, please visit www.questpond.com
58:55

Whole Brain Emulation: The Logical Endpoint of Neuroinformatics?
Google Tech Talk May 27, 2010 ABSTRACT Presented by Anders Sandberg. The idea of creating ...
published: 01 Jun 2010
author: GoogleTechTalks
Whole Brain Emulation: The Logical Endpoint of Neuroinformatics?
Google Tech Talk May 27, 2010 ABSTRACT Presented by Anders Sandberg. The idea of creating a faithful, one-to-one computer copy of a human brain has been a popular philosophical thought experiment and science fiction plot for decades. While computational neuroscience and systems biology are currently very far away from this goal, the trends towards large-scale simulation, industrialized neuroinformatics, new forms of microscopy and powerful computing clusters point in this direction and are enabling new forms of simulations of unprecendented scope. In this talk I will discuss current estimates of how close we are to achieving emulated brains, technological requirements, research challenges and some of the possible consequences.
6:00

Symantec Endpoint Recovery Tool CdRom
How to use the Symantec Endpoint Recovery Tool CdRom. To download the latest virus definit...
published: 24 Jul 2010
author: AlessandroTani
Symantec Endpoint Recovery Tool CdRom
How to use the Symantec Endpoint Recovery Tool CdRom. To download the latest virus definitions Symantec, go to the website: www.symantec.com
2:30

Full disk encryption in Sophos Endpoint 10
www.sophos.com Find out how we're integrating full disk encryption management and depl...
published: 29 Nov 2011
author: SophosProducts
Full disk encryption in Sophos Endpoint 10
www.sophos.com Find out how we're integrating full disk encryption management and deployment into Sophos Endpoint 10
4:52
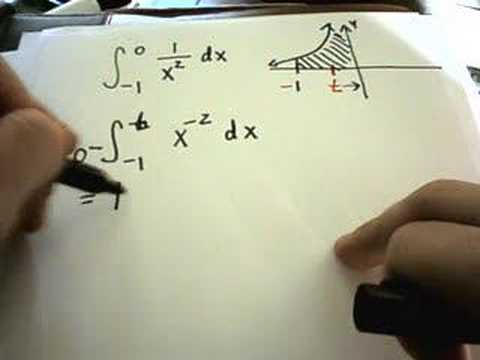
Improper Integral with Infinite Discontinuity at Endpoint
Improper Integral with Infinite Discontinuity at Endpoint. For more free math videos, visi...
published: 16 Apr 2008
author: patrickJMT
Improper Integral with Infinite Discontinuity at Endpoint
Improper Integral with Infinite Discontinuity at Endpoint. For more free math videos, visit PatrickJMT.com
1:14

Endpoint Protector and your data is safe from inside data theft
www.EndpointProtector.com Endpoint Protector secures your data from inside data theft, dat...
published: 08 Jun 2009
author: CoSoSys
Endpoint Protector and your data is safe from inside data theft
www.EndpointProtector.com Endpoint Protector secures your data from inside data theft, data loss and data leakage. This is a funny video we made about data thieves being ignored in the company since the network is protected with Endpoint Protector and the thieves have no chance copying it to their USB Flash Drives. Visit http for more info and a free trial.
13:18

BrainShare Keynote 2011 Novell Part 4 - ZENworks
BrainShare Keynote 2011 - Novell Business Unit - Part 4 ZENworks...
published: 11 Oct 2011
author: novell
BrainShare Keynote 2011 Novell Part 4 - ZENworks
BrainShare Keynote 2011 - Novell Business Unit - Part 4 ZENworks
5:02

Symantec's Endpoint Protection Small Business Edition
There is a newer video review of Symantec's Endpoint Protection.cloud here that includ...
published: 20 Apr 2009
author: davidstrom2007
Symantec's Endpoint Protection Small Business Edition
There is a newer video review of Symantec's Endpoint Protection.cloud here that includes managed services making it easier for SMBs to protect their computers. webinformant.tv
9:16

How My Endpoint Protector Works - Device Control & Endpoint Security as a Service (SaaS)
www.EndpointProtector.com Device Control & Endpoint Security hosted and managed in the...
published: 18 Jun 2009
author: CoSoSys
How My Endpoint Protector Works - Device Control & Endpoint Security as a Service (SaaS)
www.EndpointProtector.com Device Control & Endpoint Security hosted and managed in the cloud. Managing and controlling one or more PCs that are in different locations (office, home or on the road) from one central management consol has never been easier. My Endpoint Protector is a Service where the server for central management is located in the cloud and reachable 24 online and all protected PCs connect to it to receive policies. Your life securing Endpoints and proactively monitoring device use to prevent data loss, data theft and data leakage has just become allot simpler and affordable. Subscribe to your risk FREE Trial at My.EndpointProtector.com
5:20

Set Steering Endpoints traxxas 2.4Ghz
This tutorial will show to set the steering endpoints using the standard Traxxas 2.4Ghz ra...
published: 25 Sep 2010
author: rcnightmare
Set Steering Endpoints traxxas 2.4Ghz
This tutorial will show to set the steering endpoints using the standard Traxxas 2.4Ghz radio controller. Again, this is the same process no matter what Traxxas RC car or truck you have. You may want to set it if there's an obstacle with your turning. First Make Sure You Subscribe To Our Channel Here-Its Free and you'll get updates when we upload new videos like this one: www.youtube.com If You Have Specific Questions, Our Free RC Forum Is The Best Place To Get Them Answered, Its hard to keep up with comments: www.rcnightmare.com Some Of Our Popular Playlists You Should Enjoy: Running Bashing Playlist: www.youtube.com Nitro Rebuild Videos: www.youtube.com Electric Shortcourse Truck Unboxings: www.youtube.com RC Buggy Unboxings: www.youtube.com RC Monster Truck www.youtube.com Traxxas Slash Tutorials: www.youtube.com RC Battery Tutorials: www.youtube.com
3:09

Web protection in Sophos Endpoint 10
www.sophos.com The most complete web protection without any extra software to install. It ...
published: 31 Oct 2011
author: SophosProducts
Web protection in Sophos Endpoint 10
www.sophos.com The most complete web protection without any extra software to install. It works wherever users are however they connect.
8:09

Riemann Sums Right Endpoints Example 1
www.integralcalc.com How to use Riemann Sums and right endpoints to evaluate the area unde...
published: 28 Feb 2011
author: TheIntegralCALC
Riemann Sums Right Endpoints Example 1
www.integralcalc.com How to use Riemann Sums and right endpoints to evaluate the area under the curve.
4:37

What's new in Sophos Endpoint Protection 10
www.sophos.com In this short video we'll tell you about the great new features in Soph...
published: 05 Jan 2012
author: SophosProducts
What's new in Sophos Endpoint Protection 10
www.sophos.com In this short video we'll tell you about the great new features in Sophos Endpoint 10 including web protection, patch assessment and full disk encryption.
14:45

Symantec Endpoint Protection 12
Concerning purchase of a product write to me on mail (andrey00756tyu@yahoo.com) Very cheap...
published: 19 May 2011
author: Andrey7871000
Symantec Endpoint Protection 12
Concerning purchase of a product write to me on mail (andrey00756tyu@yahoo.com) Very cheaply !!!!!! Subscription to 3 years!!!!!!!!!!!
2:30

episode #66: endpoint
endpoint web.mac.com...
published: 08 Oct 2006
author: livecoretv
episode #66: endpoint
endpoint web.mac.com
2:14

My Endpoint Protector explained in plain English / Device Control can be so easy
Manage portable device use online with My Endpoint Protector and stay clear of portable de...
published: 10 Jul 2009
author: CoSoSys
My Endpoint Protector explained in plain English / Device Control can be so easy
Manage portable device use online with My Endpoint Protector and stay clear of portable device threats. Visit my.EndpointProtector.com With My Endpoint Protector you can 1.Control portable device use on Windows and Mac 2.Centrally controlled online, no Server Hardware or Server Software Required 3.Prevent Data Loss, Data Theft and Data Leakage 4.Find out who is trying to do what with your data 5.Setup in minutes 6.Try it today at www.EndpointProtector.com
59:19

Webinar - Endpoint-Level Security - 2011-09-08
Security protection is one of the biggest technology concerns for libraries and nonprofits...
published: 18 Oct 2011
author: TechSoupVideo
Webinar - Endpoint-Level Security - 2011-09-08
Security protection is one of the biggest technology concerns for libraries and nonprofits. During this webinar, Symantec representative Andy Singer discusses some of the threats facing your nonprofit or library, and the enterprise-level security you can deploy, such as Symantec's Endpoint Protection, to help to better protect your organization. What is endpoint protection? Endpoint security products protect networked laptops, desktops, and servers ("endpoints") against viruses, worms, Trojan horses, spyware, adware, rootkits, and threats not seen before ("zero-day attacks"). They consist of client software that run on the endpoints and management software that run on a server. These products are most suitable for organizations with 100 or more endpoints.












